Malicious software that has gone down in history. Part II

As mentioned in the previous part - viruses are an integral part of the world of computer technology and the Internet. They are different: funny and harmless, large and complex, fast and destructive, spyware and even sabotage. The creators of these programs clearly have a bright mind, but not always a clear conscience. Today we will get acquainted with viruses that are not included in the selection of the previous part . Go.
ANIMAL

This program only formally bears the title of a “worm”, since its author had no malicious intent from the beginning. ANIMAL is a computer guessing game where the player can give hints to the game, and she must guess which animal he has guessed. The game worked on UNIVAC 1100/42 computers under Exec-8 OS. And it was created back in 1974 by John Walker, who literally began to fall asleep with requests to share his creation. At that time, it was necessary to record the program (in this case, the game) on a magnetic tape and send it by mail. This tedious process was extremely annoying to John, and in January 1975 he added a special subroutine PERVADE, the task of which was to search for a free directory and record a game on it. So the spread of the game went much faster.
Creeper

Perhaps the first program, which can be called the Internet worm. It was discovered in the early 70s, and spread through the ARPANET (the predecessor of the modern Internet).
The history of creation and even the very existence of Creeper is shrouded in secrets, theories and inaccuracies. Someone says that the program came out into the world in the early 70s, and someone believes that in the late 1960s. It is known that Creeper was written by Bob Thomas. He was also the author of the Tenex RSEXEC OS, on the basis of which Creeper acted.
The main actions of Creeper were displaying a message in the terminal - “I'M THE CREEPER ... CATCH ME IF YOU CAN” and transferring yourself from one machine to another. That is, the program did not copy itself, namely, it jumped from device to device.
Then Ray Tomlinson, a colleague of Bob Thomas, wrote the program REAPER, whose task was to search for and destroy Creeper. Thus, the first nematode program appeared - in simple words, a virus that destroys another virus.
Elk cloner
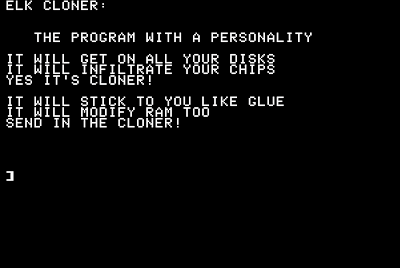
Another representative of the early forms of viruses. It was written by Richard Skrenta, a 15 year old guy, especially for Apple II.
It infected DOS, which was recorded on floppy disks. As soon as the computer was booted from this floppy, the virus was activated. He also tracked when access to non-infected floppies occurred and copied himself to them, thereby spreading through the system. However, this virus did not carry much harm. Every 50 downloads, he would display a creeping message:
Elk Cloner: The program with a personality
It will get on all your disks
It will infiltrate your chips
Yes it's Cloner!
It will stick to you like glue
It will modify ram too
Send in the Cloner!
Jerusalem

Discovered in Israel at the end of 1987, this virus remained active until 1995. Infected .com and .exe files under the DOS operating system. The virus further infected all the programs that were launched on the machine after its activation. Jerusalem had two cardinally opposite results, harmless and extremely destructive. The first - also called BlackBox - is a screening (if the system is in text mode) of a black square with row 5, line 5 through row 16, line 16. The second result - every Friday, the 13th virus deleted any program running on that day. Another funny feature of the virus was that it avoided infecting the COMMAND.COM file.
DATACRIME
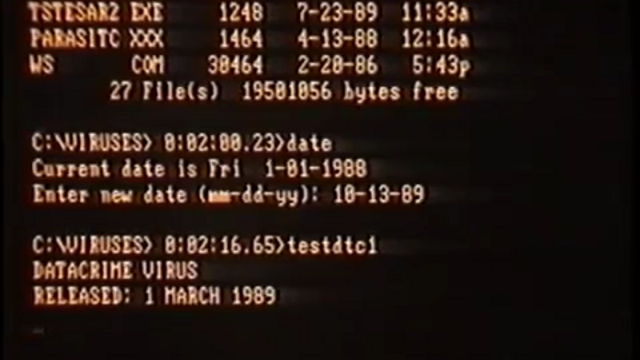
Having made a lot of noise back in 1989, the Datacrime virus re-recorded parts of hard drives and outputted a message. And now in order. The virus got on the computer when the infected file opened. Then he scanned the disks in a certain sequence (C :, D :, A :, B :) in search of .com files for their infection. It's funny that the virus went around a dozen expensive files, in which the seventh letter was D, apparently avoiding infection with COMMAND.COM.
If the infected file was launched on October 13 or after, the virus would display the following message: “DATACRIME VIRUS '' RELEASED: 1 MARCH 1989”. Then formatted the first 9 tracks of the hard disk.
Aids
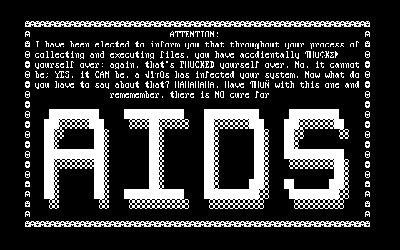
A trojan that replaces the AUTOEXEC.BAT file, which later used to count how many times the computer was loaded. For 90 times, AIDS hid directories, encrypted file names on drive C, which made the system inoperative. The virus then prompts the user of the infected machine to “renew the license” and contact PC Cyborg Corporation for making a payment (transfer $ 189 to a mailbox in Panama). There are also versions of the AIDS virus that do not wait for 90 PC downloads, but disrupt C drive immediately after its activation.
The creators of AIDS also gave their victims a look at the “licensing agreement”, the text of which contained the following:
If you install [this] on a microcomputer ...
If you’re liking this
In the case of a license agreement, it is a lawsuit.
They will adversely affect other program applications ...
You are hereby advised by the terms of this license agreement; [your PC] will stop functioning properly ...
You are strictly prohibited from [this product] with others ...
In the end, the virus lost the sound (a certain “squeak”) and outputted a message:
I have been accdientally (sic) yourself HÜ yourself KΣ [[PHUCKED]: yourself over: again, that's PHUCKED yourself over. No, it cannot be; YES, it CAN be,: a √ìτûs [virus] has infected your system. What do you have? : HAHAHAHAHA. There is NO cure for
AIDS (huge font).
Win95.CIH
Also known as Chernobyl, the virus was first detected in June 1998 in Taiwan. Once the virus is activated, by opening the infected file, it captures all executable files. At the same time, the infected files did not differ in their "weight" from their healthy version, due to the unique infection method used by CIH. He searched for empty, unused spaces in files, then broke himself into several small parts and injected the code of these parts into empty space.
CIH actually had two options for the outcome of its activities, both activated on April 26th. In the first case, the virus overwrites the hard disk, starting with sector 0, using an endless loop until the system completely drops. The second option - an attack on the Flash BIOS and an attempt to damage the data stored there, which led to the fact that nothing was displayed when the computer was started. The victims of the virus were machines under Windows 95, 98 and ME.
Victims of the CIH virus has become a huge number of computers and companies. In Korea, about 1 million PCs were damaged, and the damage amounted to $ 250 million. Boston University was also hit (students were removed right before the exams), 200 computers in Singapore, 100 in Hong Kong, 10 large companies in India and others.
CIH has spread so much that even some of the programs delivered to the market have been infected by it, including the Wing Commander game, driver updates for the CD-R400 from Yamaha, and even Aptiva computers from IBM have entered the market with a pre-installed virus.
Onehalf
One of the most common viruses of the mid-90s. After infection, the virus installed itself in the master boot record of the boot disk. Infected the computer's memory when booting the OS, and then intercepted the INT 21h interrupt. Each time the PC starts, the virus encrypts 2 tracks on the hard disk.
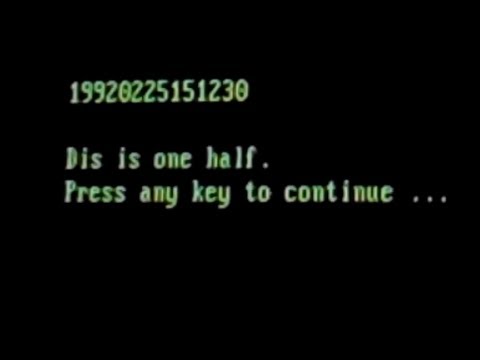
When half of the disk was encrypted, the virus would display a message similar to the following:
Dis is one half. Press any key to continue ...
The encrypted parts of the disk could no longer be used by the system, because even the removal of the virus did not completely eliminate the problem.
OneHalf is a representative of stealth viruses, because it used polymorphic methods of distribution, which made it impossible for most antiviruses to detect it.
When Windows 95 and newer versions came out, the OneHalf virus has almost become extinct.
Morris worm

Robert Tappan Morris
Scandalous network worm. It was recorded for the first time on November 2, 1988, for which he received its alternative name - Internet worm of November 2, 1988. Made a lot of noise during its existence.
The creator of the worm was Robert Tappan Morris, a graduate student at Cornell University. Robert was not going to infect the entire ARPANET, he thought that only VAX computers with 4BSD and Sun 3 operating systems would infect his creation. But the worm had portable C code, which allowed it to spread to other machines.
How the worm acted. First, he scanned the computer, trying to find out if it was already infected or not. Then he randomly overwritten himself in order to ensure his invisibility. The basis of the worm's activity was a vulnerability in the Sendmail mail server, Finger, rsh / rexec services with dictionary selection of passwords. This dictionary consisted of 400 keywords, only. And considering that in those days very few people paid due attention to security, the login and password often coincided. To hide its trace, Morris worm deleted its executable files, renamed its process to sh.
The irony is that the father of Robert, the author of the worm, was an NSA computer expert. He advised his son to surrender to the authorities, which the latter did. This is how the first case in the history of the Computer Fraud and Abuse Act (1986) came about. Robert was threatened with 5 years in prison and a $ 250,000 fine. But due to the fact that he surrendered himself, he was sentenced to 3 years probation, 10,000 fines and 400 hours of community service.
Red october

Fans of James Bond movies and all spyware, this item is for you. In October 2012, the antivirus company Kaspersky Lab detected a spyware malware.
The researchers of this virus stated that it was actively functioning around the world for 5 years before it was discovered. The virus collected and transmitted to its creators information of a different nature (secret, diplomatic, state, personal, etc.). The virus spread through an email with an infected file, and used to further spread vulnerabilities in Microsoft Word and Excel. Later, a webpage was discovered that exploited a Java plug-in vulnerability.
After the exposure, domain registrars and hosting companies around the world covered about 60 domain names that were used by the Red October virus. After such a turn of events, the attackers themselves stopped distributing Red October.
It is still unknown who is the author of Red October and exactly what goals he (or they) pursued.
Cookie monster

For those who remember the wonderful children's show “Sesame Street”, the name Cookie Monster is associated with a big blue monster who just has fun with cookies. In 1970, the same year, Chris Tavares wrote the same program for the computer IBM 2741 OS Multics. This program displayed the message “give me cookies” in the terminal, and the user had to enter a “cookie” (from English - cookies) to unlock the terminal. Cookie Monster was originally a laugh program. The author manually sent it to his classmates.
Of course, Cookie Monster cannot be called a virus (although many sources call it that), because it does not have a replication and distribution mechanism. But, nevertheless, Cookie Monster can be attributed to programs of a malicious nature, although there was no particular harm.
Ontario

Not just one virus, but a whole family of viruses called Ontario, the first representative of which was discovered back in July 1990 - Ontario.512.
Ontario.512 was activated by opening an infected file (.COM, .EXE or .OVL). Then it became a resident program and infected all the files that were opened on the computer after that. Infected files increased in size by 512 bytes (.COM extension files) or by 512-1023 bytes (.EXE and .OVL extension files). Some systems with large file sectors could produce information on increasing the size of files by more than 1023 bytes.
Ontario.1024 was discovered in October 1991. Also infect files, but only with the extension .COM or .EXE, increasing their size by 1024 bytes. If the virus was located in the computer's memory, the user did not receive information about the increase in file size. This was a manifestation of the stealth (stealth) mechanisms of the virus. The virus also reduced the available memory by 3072 bytes and could cause problems in working with printers.
Ontario.2048 was discovered in September 1992. Unlike its predecessors, it possessed the characteristics of polymorphic and stealth viruses. When opening an infected file (extensions .COM, .EXE, .OVL, or .SYS), the virus became resident and infected all the files that were opened after that. Infected files increased in size by 2048 bytes, but, as in the case of Ontario.1024, if the virus was in the memory itself, then such symptoms could not be detected.
The virus also contained encrypted text:
COMSPEC = \ COMMAND.COM COMEXEOVLSYS
MSDOS5.0
Yam
Your PC has a bootache! - Get some medicine!
Ontario-3 by Death Angel
- The first line is a reference to the infection method of the file COMMAND.COM + extensions of the infected files;
- The second line is the MS-DOS version on which the virus was written;
- The third line is the Youngsters Against McAfee virus writers group (which the author has joined);
Also from the text it can be assumed that the author of all three viruses of the Ontario family is a certain Death Angel.
With the advent of Windows, the spread of Ontario viruses will diminish. And by 2006 they were virtually extinct.
Neshta

Do not think that viral geniuses are only in the USA. There are plenty of smart guys among programmers from the countries of the former USSR, but not everyone uses their minds for good purposes. As, for example, the author of the virus Neshta. It was first discovered in 2005. It is believed that the virus was created in Belarus, where it was most prevalent. In addition, the word "Neshta" refers to the Belarusian word " Neshta ", which means " something ".
The virus was created in the Delphi programming language. When infecting a computer, the Neshta virus created the svchost.com file in the Windows system folder, and the following line was added to the registry: [HKCR \ exefile \ shell \ open \ command] @ = "% WINDIR% \ svchost.com \"% 1 \ "% *". This led to the fact that when you run any file with the .exe extension, the virus infected it, and instead it was run by svchost.com. All infected files increased in size by 41472 bytes, due to the introduction of malicious code.
In one of the versions of the virus (there were two of them: a and b) the author’s message was as follows:
Delphi-the best. Fuck off all the rest. Neshta 1.0. Made in Belarus. Pryvitane ўsim ~ tsikavim ~ belarus_kim dzhachatam. Aliaksandr Rygoravich, you taxame. Vosn - a couple of caps ... Alivaryya - a good drink! Best regards 2 Tommy Salo. [Nov-2005] yours [Dziadulja Apanas]
Many companies, including the Belarusian bank Tekhnobank, whose computers were infected in 2007, became victims of the virus. This led to the fact that customers of this fin. institutions could not conduct cash transactions for several days.
The Neshta virus so badly spoiled all the nerves that the law enforcement agencies of Belarus declared a hunt for its author, but, as is known, to no avail.
Nimda

One of the most remarkable worms. He became the first worm to run without the need to open an infected email. The first to begin to modify the sites in order to offer the user to download the file (containing the worm, of course).
For its propagation, Nimda used not one method, but as many as 5:
- Email;
- Open shared network resources;
- Infected websites;
- Vulnerabilities in IIS;
- Backdoors left in systems by the predecessor worms Code Red II and sadmind / IIS
More about distribution methods
Infected Sites
The worm-infected site has JavaScript code that causes the browser to download the README.EML file containing the worm:
script language = "javascript">
window.open ("readme.eml", null, "resizable = no, top = 6000, left = 6000")
The README.EML file will open in a smaller window if the user is using Explorer 5.5 with Service Pack 1 (or earlier versions of service packs). There is a possibility that with this method the worm cannot infect the Windows NT or Windows 2000 systems.
The subject of the letter and the message itself may be absent or be random. The letter will have an attached file - README.EXE, which can even start from the preview panel without any user intervention, since it exploits a vulnerability in Explorer 5.5 with Service Pack 1, when Explorer was used to render html mail.
Local Area Networks
In the case of connecting to a local network with an infected PC, the victim machine will receive the RICHED20.DLL file located in any of the folders with the .doc or .eml files. These files will be hidden.
Servers
Using a vulnerability in Microsoft IIS 4.0 / 5.0 servers, the worm is copied to the “scripts” directory under the name ADMIN.DLL.
The Nimda worm (admin backwards) infects personal computers on Windows 95, 98, NT, 2000 or XP systems and servers on Windows NT and Windows 2000.
The following code was found in the worm code: Concept Virus (CV) V.5, Copyright © 2001 RPChina. This convinced many researchers that this software was developed specifically in China, but apart from the fact that the first distribution came from networks in Asia, there is no exact data.
Cryptolocker
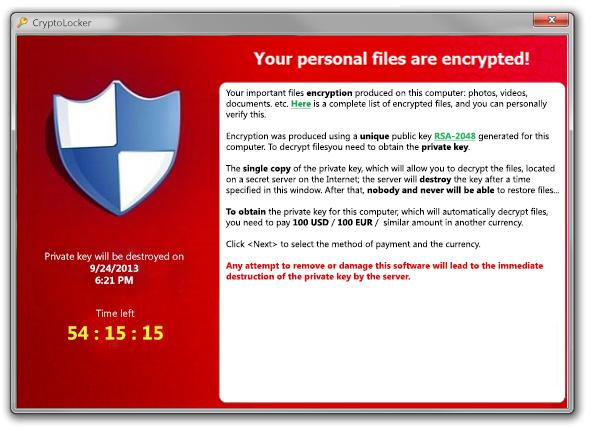
Here we will talk not only about malware, but about the whole cyber attack made with it. In the period from September 5, 2013 to May 2014, many Windows users were victims of ransomware.
The basis of the attack was a trojan that spread through infected email attachments. When the PC was infected, the Trojan encrypted Microsoft Office files, OpenDocument, images and AutoCAD files. Next, a message was displayed on the screen informing the user that his files are encrypted, and if he wants to get them back, then you need to pay $ 400 (or euro) via an anonymous prepaid cash voucher or the same amount but in Bitcoin. This must be done within 72 hours or 100 hours. Otherwise, the key on the server (necessary for decryption) will be destroyed, and the files will remain encrypted. If the user-victim is still decided on the deal, he downloaded the decryption program. However, many of the victims claimed that even after the payment was made, their files remained encrypted.
In November 2013, the creators of CryptoLocker went even further in their arrogance and confidence in impunity. They opened an online center where victims could pay a ransom for their data, even if the deadline passed (in this case, the price increased to 10 bitcoins).
On June 2, 2014, it was officially announced that Tovar had previously been in operation, as a result of which the Gameover Zeu botnet used to distribute CryptoLocker was eliminated. One of the accused was a Russian hacker named Evgeny Bogachev. According to the data collected by the researchers of the attack, the extortion hackers were enriched by $ 3 million.
Netsky

The worm of the year 2004, so to speak.
Spread through a spam letter with the following senders:
Ebay Auctions <responder@ebay.com>
Yahoo Auctions <auctions@yahoo.com>
Amazon automail <responder@amazon.com>
MSN Auctions <auctions@msn.com>
QXL Auctions <responder@qxl.com>
EBay Auctions <responder@ebay.com>
Yahoo Auctions <auctions@yahoo.com>
Amazon automail <responder@amazon.com>
MSN Auctions <auctions@msn.com>
QXL Auctions <responder@qxl.com>
EBay Auctions <responder@ebay.com>
The text of the letter contained the following:
# ----------------- message was sent by automail agent ------------------ #
Congratulations!
You were successful in the auction.
Auction ID: <**** **** ****> - A
Product ID: <**** **** ****> - P
(where **** **** is a set of random numbers)
A detailed description of the product and the bill
are attached to this mail.
Please contact the seller immediately.
Thank you!
Attached to the letter was a file with alleged auction details:
prod_info_04155.bat
prod_info_04650.bat
prod_info_33462.cmd
prod_info_33967.cmd
prod_info_42313.pif
prod_info_42314.pif
prod_info_42818.pif
prod_info_49146.exe
prod_info_49541.exe
prod_info_54234.scr
prod_info_54235.scr
prod_info_54739.scr
prod_info_33325.txt.exe.zip
prod_info_33543.rtf.scr.zip
prod_info_34157.htm.exe.zip
prod_info_43631.doc.exe.zip
prod_info_43859.htm.scr.zip
prod_info_47532.doc.scr.zip
prod_info_54433.doc.exe.zip
prod_info_55761.rtf.exe.zip
prod_info_56474.txt.exe.zip
prod_info_56780.doc.exe.zip
prod_info_65642.rtf.scr.zip
prod_info_77256.txt.scr.zip
prod_info_87968.htm.scr.zip
prod_info_04650.bat
prod_info_33462.cmd
prod_info_33967.cmd
prod_info_42313.pif
prod_info_42314.pif
prod_info_42818.pif
prod_info_49146.exe
prod_info_49541.exe
prod_info_54234.scr
prod_info_54235.scr
prod_info_54739.scr
prod_info_33325.txt.exe.zip
prod_info_33543.rtf.scr.zip
prod_info_34157.htm.exe.zip
prod_info_43631.doc.exe.zip
prod_info_43859.htm.scr.zip
prod_info_47532.doc.scr.zip
prod_info_54433.doc.exe.zip
prod_info_55761.rtf.exe.zip
prod_info_56474.txt.exe.zip
prod_info_56780.doc.exe.zip
prod_info_65642.rtf.scr.zip
prod_info_77256.txt.scr.zip
prod_info_87968.htm.scr.zip
When an infected file was opened, the virus created a mutex that prevented the launch of more than one copy of the worm, which copied itself to the Windows folder under the name Services.exe. Next, Netsky added a special entry to the registry that allows it to run when the computer is turned on. Another, very funny, feature of the worm was the removal of Taskmon and Explorer entries from the registry of keys that were left there by another Mydoom worm.
Netsky also scanned all disks in search of folders with names containing "share" or "sharing" and copied themselves into them as
following files:
doom2.doc.pif
sex sex sex sex.doc.exe
rfc compilation.doc.exe
dictionary.doc.exe
win longhorn.doc.exe
e.book.doc.exe
programming basics.doc.exe
how to hack.doc.exe
max payne 2.crack.exe
e-book.archive.doc.exe
virii.scr
nero.7.exe
eminem - lick my pussy.mp3.pif
cool screensaver.scr
serial.txt.exe
office_crack.exe
hardcore porn.jpg.exe
angels.pif
porno.scr
matrix.scr
photoshop 9 crack.exe
strippoker.exe
dolly_buster.jpg.pif
winxp_crack.exe
sex sex sex sex.doc.exe
rfc compilation.doc.exe
dictionary.doc.exe
win longhorn.doc.exe
e.book.doc.exe
programming basics.doc.exe
how to hack.doc.exe
max payne 2.crack.exe
e-book.archive.doc.exe
virii.scr
nero.7.exe
eminem - lick my pussy.mp3.pif
cool screensaver.scr
serial.txt.exe
office_crack.exe
hardcore porn.jpg.exe
angels.pif
porno.scr
matrix.scr
photoshop 9 crack.exe
strippoker.exe
dolly_buster.jpg.pif
winxp_crack.exe
Also for further distribution, the worm looked for email addresses among files
extensions
.msg
.oft
.sht
.dbx
.tbb
.adb
.doc
.wab
.asp
.uin
.rtf
.vbs
.html
.htm
.pl
.php
.txt
.eml
.oft
.sht
.dbx
.tbb
.adb
.doc
.wab
.asp
.uin
.rtf
.vbs
.html
.htm
.pl
.php
.txt
.eml
The result of the worm's activity was a strong slowdown, and sometimes a fall, of computers, which, in turn, led to enormous financial losses. They ranged from about 25.6 to 31.3 billion dollars worldwide.
The author of this creation is Sven Jaschan, a student from Germany. He is also the author of the Sasser worm (about him in the next block). Sven was caught and sentenced to 21 months probation and 30 hours of community service.
Sasser
Another creation of Sven Yashan. Dated in 2004. He made a lot of noise and harm in financial terms, although initially he didn’t have such a goal.
The worm spread using a LSASS vulnerability in Microsoft Windows, and did not require any action from the victim user to activate.
Sasser created an FTP server on port 5554 for its distribution. On disk C, the worm created a file under the root with the name win.log, which contained the IP address of the computer that the worm was trying to infect recently. The worm also used the Windows API to check the IP address of the system in order to later generate a new address based on it. in 25% of cases, the first 2 digits of the generated address coincide with the host when the last 2 are random. There is a probability of 23% that only the first digit will match, and a probability of 52% that the generated IP will be absolutely random. The random address selection process uses 128 threads, which can significantly degrade the performance of an infected machine.
Sasser also creates a script (cmd.ftp) in the system of the victim machine that “forces” it to download the worm from an infected ftp server. After the download is complete, the script is deleted.
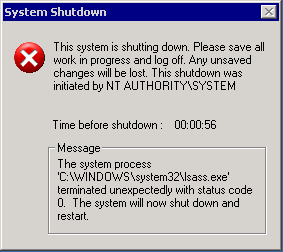
The outcome of the worm’s work was a constant reboot of the computer with an output of the lsass.exe process errors. However, this was enough for many companies to suffer huge losses. In total, the damage from Sasser was approximately $ 18 billion. A total of about 250,000 machines were infected.
As mentioned earlier, Sven was later punished for his creation. If selfish intentions were revealed in his actions, then the punishment would be much more severe.
Anna Kournikova
In 2001, the Danish programmer Jan de Wit created the worm Anna Kournikova. The victim user received a letter with an alleged photograph of a famous tennis player Anna Kournikova. There were naturally no photos, but there was a worm that infected the computer if the file containing it was opened. The name of the file was AnnaKournikova.jpg.vbs. The reason why the user could not hesitate to open the file in the standard Windows settings that hide the file extension. Thus, the user saw the following - AnnaKournikova.jpg. Then the worm scanned the mail address database in Microsoft Outlook and sent itself to all contacts.
Worm development took a couple of hours from de Vita. According to the investigation, he used a special Visual Basic program “Worm Generator”, which he downloaded on Sunday February 11th. And on the same day, at about 3:00 pm, the worm was ready and released on the Internet.
Jan de Wit came to the police himself. The lawyers insisted that de Wit did not wish evil to anyone and created a worm without regard to the consequences. However, the FBI provided evidence that the harm was still, and not small, more than 166,000 dollars. As a result, Yang was sentenced to 150 hours of community service or 75 days in prison.
agent.btz

Computer worm, put on the ears of the Pentagon. In 2008, a flash drive infected with the agent.btz worm was inserted into a laptop at a US military base in the Middle East. The computer was connected to the US Central Command (USCENTCOM). The worm spread to all systems, including the secret. He did this by creating an AUTORUN.INF file in the root of each of the disks. I could also scan a computer for backdoors that I used for distribution.
The Pentagon spent about 14 months cleaning its systems from the worm. They even banned the use of flash drives or other portable media.
There were a lot of speculations and conspiracy theories around this worm. Someone thought he was developed by a lone hacker. And the Pentagon was only an accidental victim among many. Others assured that the worm is a product of the sabotage activity of Russia or China.
Zeus

Troyan, which became a weapon in the hands of scammers It was first discovered in 2007.
The Trojan spread through social networks (about 1.5 million photo posts on Facebook that were redirected to the site with the Trojan) and via email. After infection, it was introduced into the system and scanned for the presence of registration type information (logins and passwords).Thus, attackers were able to connect to the bank accounts of their victims and conduct money transfer operations. The funds were transferred to other “infected” accounts or to fake accounts, which complicated the process of tracking the chain by the attacker.
Some versions of Zeus were camouflaged using the digital signature of Kaspersky Lab, which, as a result of the study, was found fake. Also, the fact that the Trojan could infect not only Windows-based computers, but also BlackBerry or Android mobile devices, was also more prevalent.
In 2010, on October 1, the FBI announced that it was conducting one of the most large-scale operations to catch criminals who had been involved in the theft of about $ 70 million from the accounts of the victims of the Zeus Trojan. About 100 people were arrested: 90 in the US, the rest in the UK and Ukraine.
Conclusion

On computer viruses, Trojans and worms, you can talk almost forever, because every day there is, if not a new virus, then certainly a new version of the old one. Some of them were created for fun and creative self-realization, while others became instruments of criminals who robbed their victims. But, nevertheless, I would like to note that the majority of cases of infection occurred through the fault of the victim himself, and more precisely because of her naivety and gullibility. Therefore you should not open strange letters, such as “Great_boobs.png”, or visit questionable sites. Also do not forget to update your antivirus. Enjoy your day and safe surfing the Internet.
As advertising. These are not just virtual servers! This is a VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better! We made VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month , options are available with RAID1 and RAID10) , do not miss the chance to place an order for a new type of virtual server, where all resources belong to you, as on a dedicated one, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!
All Articles