Infobase specialists: “A smart car is far from always a safe car”

Source: Getty Images
Three years ago, two information security specialists showed that the new Jeep models are vulnerable to attackers. Here we have in mind not driving performance and other characteristics, but the ability to control various functions remotely. And the “smarter” machine, the more it is subject to outside influence. Unfortunately, the demonstration conducted by the above-mentioned experts did not lead to anything. Yes, the manufacturer Jeep tried to solve the problem, but other companies still pay as little attention to the necessary information security measures as before.
Recently, Trend Micro employees published a post that gives an insight into how well modern cars are
“You can disable airbags, geo sensors, disable or enable central locking and hijack a car,” said Federico Maggi, one of the members of the Trend Micro team, who conducted the tests. According to him, possible attacks will go unnoticed - it is extremely difficult to detect them.
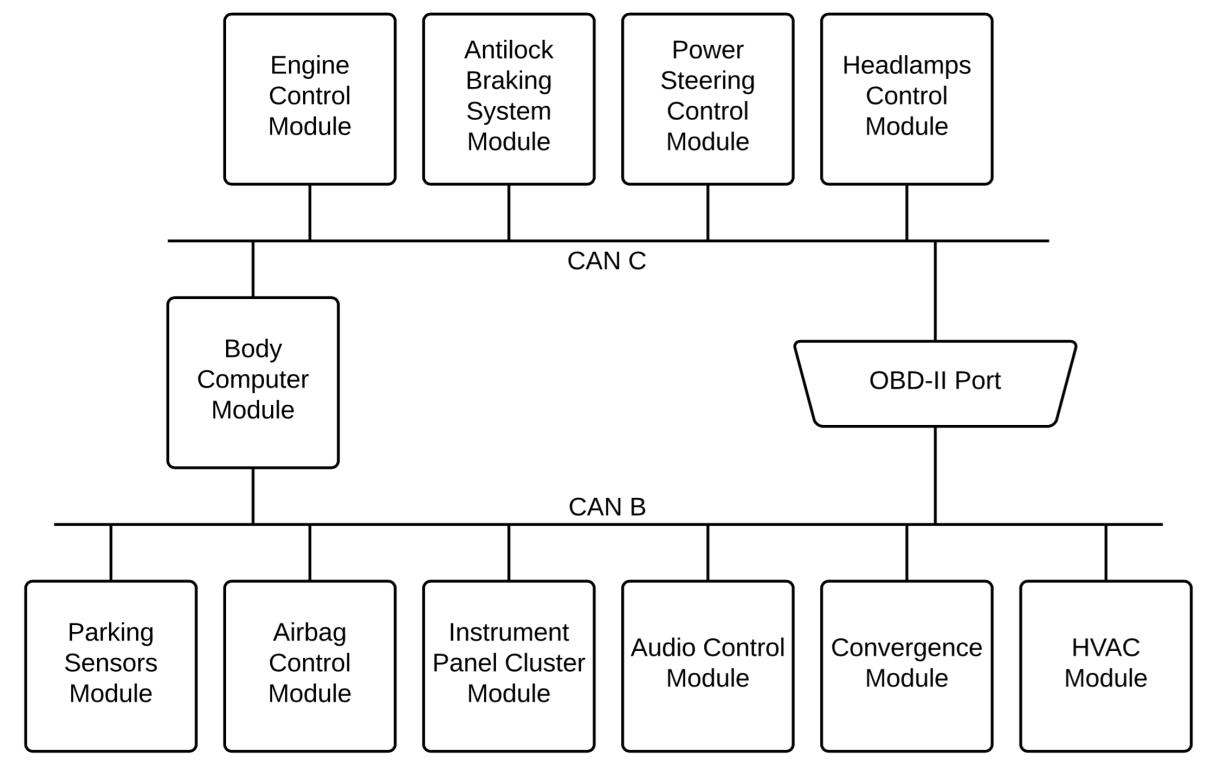
CAN network diagram
So far, researchers have demonstrated only a fraction of the threats that are not critical. In any case, the interception of the control of the car, which was shown in 2015 on the example of the Jeep SUV, has not yet been shown. Nevertheless, something similar can be done with Tesla, probably one of the most technologically advanced land vehicles of the person at the moment.
The positive point in all this is that the found vulnerabilities cannot be exploited remotely by 100%. Nevertheless, the attacker needs one-time access to the control and safety system of the car. Without this, it will be impossible to carry out your plan. It is necessary to connect either to the wireless network or to the OBD port of the car.
However, the threat of attacks of this type is serious enough for car manufacturers to simply ignore the problem.
So what's the threat? As mentioned above, vulnerabilities in CAN can be used to your advantage. Namely - the attackers, if they wish, can make any element of the car seem "defective" for the central control system of the machine. In this case, this element is turned off by the car itself, and it will not work. To detect this type of attack, according to the researchers, is quite difficult, if not impossible.
At the same time, it is possible to disconnect the elements of the vehicle control system in different ways by giving out various error messages. As a result, the same attack may look from the side, as a few incidents unrelated to each other. Accordingly, it will be extremely difficult to detect the attack. In addition, to understand whether something is really broken or if someone is attacking a car is impossible.
So far, this work is purely theoretical. A real attacker is unlikely to be able to conduct an attack predicted by experts in any close time. According to the head of the research group, he “will be surprised if he sees this in practice.”
But this is now, because there are not so many “smart” cars. But over time they become more and more. Accordingly, hackers can switch their attention to not hacking auto systems (some have been doing this for a long time). Therefore, before the theoretical problem becomes real, specialists try to preempt the possibility of exploiting vulnerabilities in CAN.
The authors of the work referred to in this material say that car manufacturers should focus not only on the design and driving properties of their cars, but also on the security of the cars they produce from the threat of external interference.
All Articles