WikiLeaks has published the CIA documentation on infecting physically isolated computers.
On June 22, 2017, the WikiLeaks website published documents from a CIA project called Brutal Kangaroo . This is a set of tools for Windows designed to infect physically isolated computers that are disconnected from the Internet (air gap) using flash drives. The information is relatively recent: the program documentation is dated February 23, 2016.
Physical isolation (air gap) is one of the security measures when a protected computer network is physically isolated from unsafe networks and the Internet. In this case, there is no possibility for the computer outside the network to establish communication with the computer inside it. For intelligence organizations, such systems present a certain problem. First, the process of installing spyware on such computers is complicated: you need to deliver a USB flash drive to them. Secondly, it is more difficult to remove information from an infected computer, if it is physically isolated.
The documentation states that the Brutal Kangaroo project consists of the following components:
- Drifting Deadline: a flash drive infection tool.
- Shattered Assurance: a server-based tool that tracks the process of automated infection of flash drives, is also the main distribution method for the Brutal Kangaroo suite. To infect individual flash drives using the program Drifting Deadline.
- Broken Promise: postprocessor Brutal Kangaroo.
- Shadow: the main mechanism of presence. This is a stage 2 tool that spreads inside a closed network and works as a hidden CnC network.
In order for Brutal Kangaroo to work, .Net 4.5 must be installed on the computer.
In the Drifting Deadline program, the user chooses the execution vector of the malicious code from the flash drive: it can be x86 and x64 DLL, which is automatically loaded in the explorer or the .lnk file, the autorun.inf setting. Malicious load can be injected directly into the process explorer.exe (in 32-bit OS) or svchost (in 64-bit) and never written to disk. Alternatively, you can not set the vector of automatic execution, and leave only the executable file that the victim will have to run manually.
On the flash drive, then you need to place the three service files Drifting Deadline. The user chooses in what format to place them: files can be assigned arbitrary names or use a compressed format when they are compressed into a single file with an arbitrary name. In the latter case, the files are compressed into one cryptoblob.
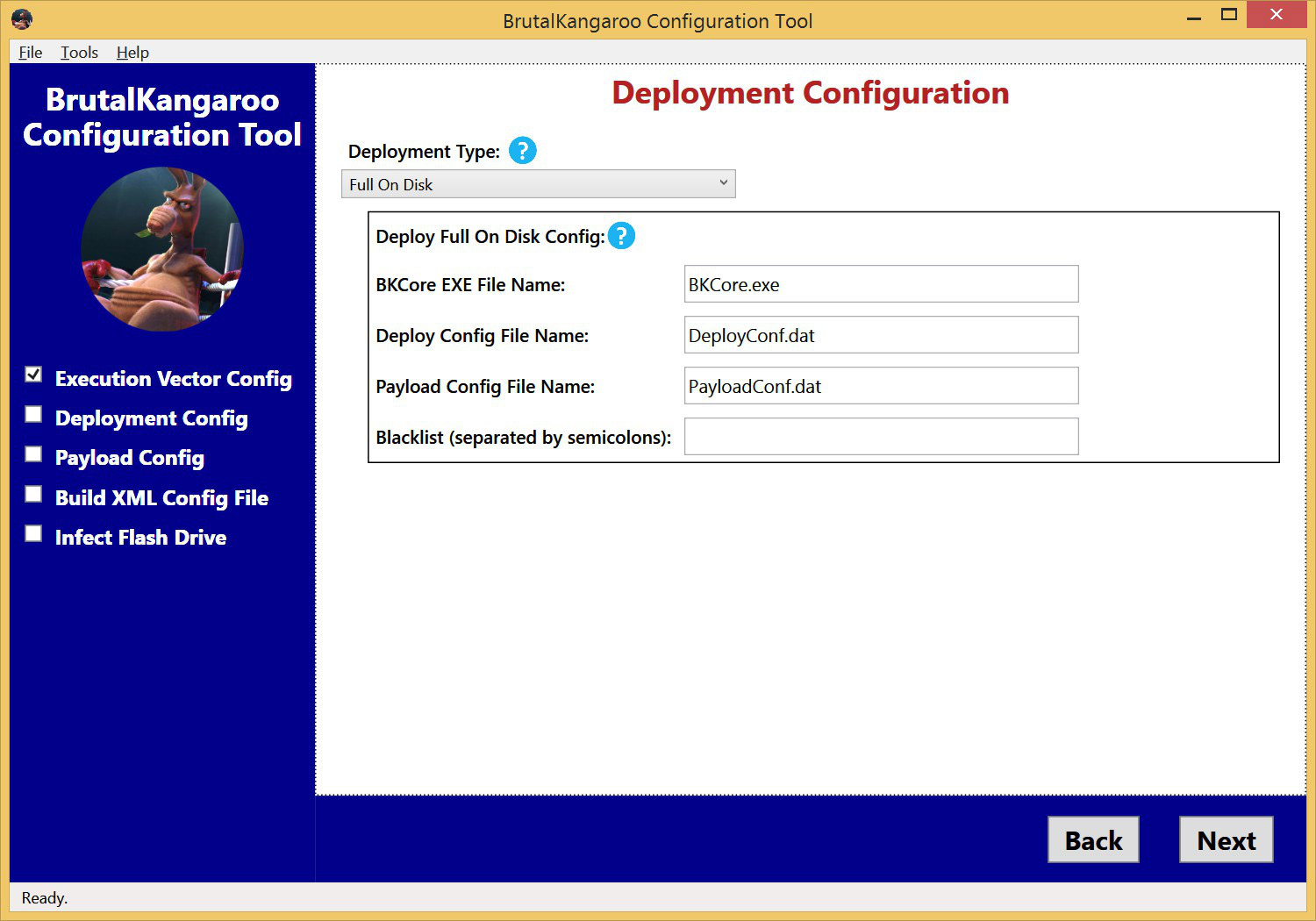
Next, the scout selects spyware modules that will be written to the USB flash drive, and indicates what information the victim needs to collect and write to the USB flash drive. Creates a mask for the collected files. It also indicates the maximum amount of information to collect and the minimum percentage of free space on the flash drive, which should remain (probably not to cause suspicion). Specifies the recording format for the information collected. For example, everything can be written to an existing file (for example, jpg or png) or directly by streaming data to NTFS, which will be hidden from view. Specifies the maximum number of spy module launches, launch conditions (for example, only when an administrator is authorized by the system), blacklist processes under which the launch was canceled, etc. All selected configuration settings are saved to an XML file. After that, you can carry out the procedure of infection of the flash drive.

Brutal Kangaroo supports this mode of operation: if the “primary host” is accessible via the Internet, the CIA agent infects it remotely, and the USB flash drive is already infected automatically from this computer. It is assumed that the unsuspecting victim will take a flash drive - and take it to a physically isolated computer, and then bring it back. In this case, all collected data stored on a flash drive will be forwarded to a CIA agent.
Interestingly, the documents address some of the problems associated with the use of spyware. For example, it is indicated that antiviruses show a warning message if software is automatically launched from a flash drive when it is inserted into a computer. At the same time, a low level of antivirus recognition of the program working files themselves is noted.
In the published collection of 11 documents that were created from 2012 to 2016. There is also documentation on the previous tools, instead of which Drifting Deadline is used. The developer of the tools indicated a division of the CIA Engineering Development Group. This unit is part of DDI (Directorate for Digital Innovation), see CIA organizational chart . It develops, tests, and maintains all CIA software. It also developed many other exploits that WikiLeaks previously published, including an exploit for Samsung TVs called Weeping Angel, which adds to the TV's 'Fake-Off' mode when the TV looks off, but at the same time records conversations in the room and sends them over the Internet to the CIA server.
All Articles