The WikiLeaks team has published information about the software with which the CIA has infected home routers for years.

It seems that the CIA software toolbox is inexhaustible. The WikiLeaks team has already published several collections of such software, but each new publication is another surprise. A few days ago, the WikiLeaks team posted information about another selection of CIA exploits that were used to attack routers of 10 of the most well-known manufacturers of network equipment, including Linksys, Dlink and Belkin. The software allowed attackers to monitor traffic as well as manipulate it, and this applies to both incoming and outgoing data packets. In addition, the same software was used to infect connected devices.
The software package in question is CherryBlossom. It is reported that this software is most effective for several models of routers, including D-Link DIR-130 and Linksys WRT300N. That's because these devices are vulnerable to remote hacking, even if using a complex administrator password. One of the exploits from the package, called Tomato, allows you to extract passwords, no matter how difficult they are. At the same time, the universal plug and play function remains enabled and can be used by hackers.
Judging by the report of WikiLeaks, with the help of this malicious software, employees hacked the protection of about 25 models of routers. When this software was modified, the “range” of vulnerable devices expanded to 100 models.
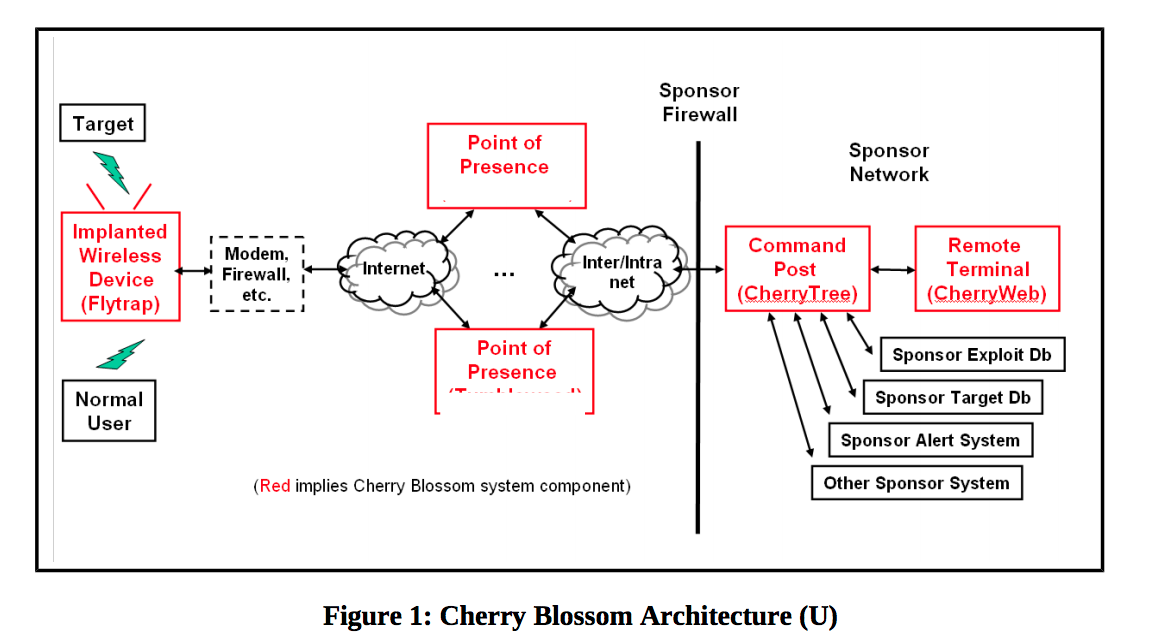
Description of the software package from the CIA is 175 pages , the information is exhaustive. As soon as the exploit finds a vulnerability and infects the router, it gets “FlyTrap” status by contacting a CIA server with the code name CherryTree. The router regularly sends information about its status and various information that may be useful to the CIA officers in their activities. If necessary, the router can send various tasks. For example, track traffic of a specific type or modify it in a special way.
In addition, if desired, the CIA could infect almost any device connected to the router. And also monitor the IP, MAC-addresses of these devices, e-mail users, their nicknames and VoIP-numbers. If desired, it was possible to track all the traffic of a specific user or force the browser on the victim’s computer to open access to the current user’s sessions.
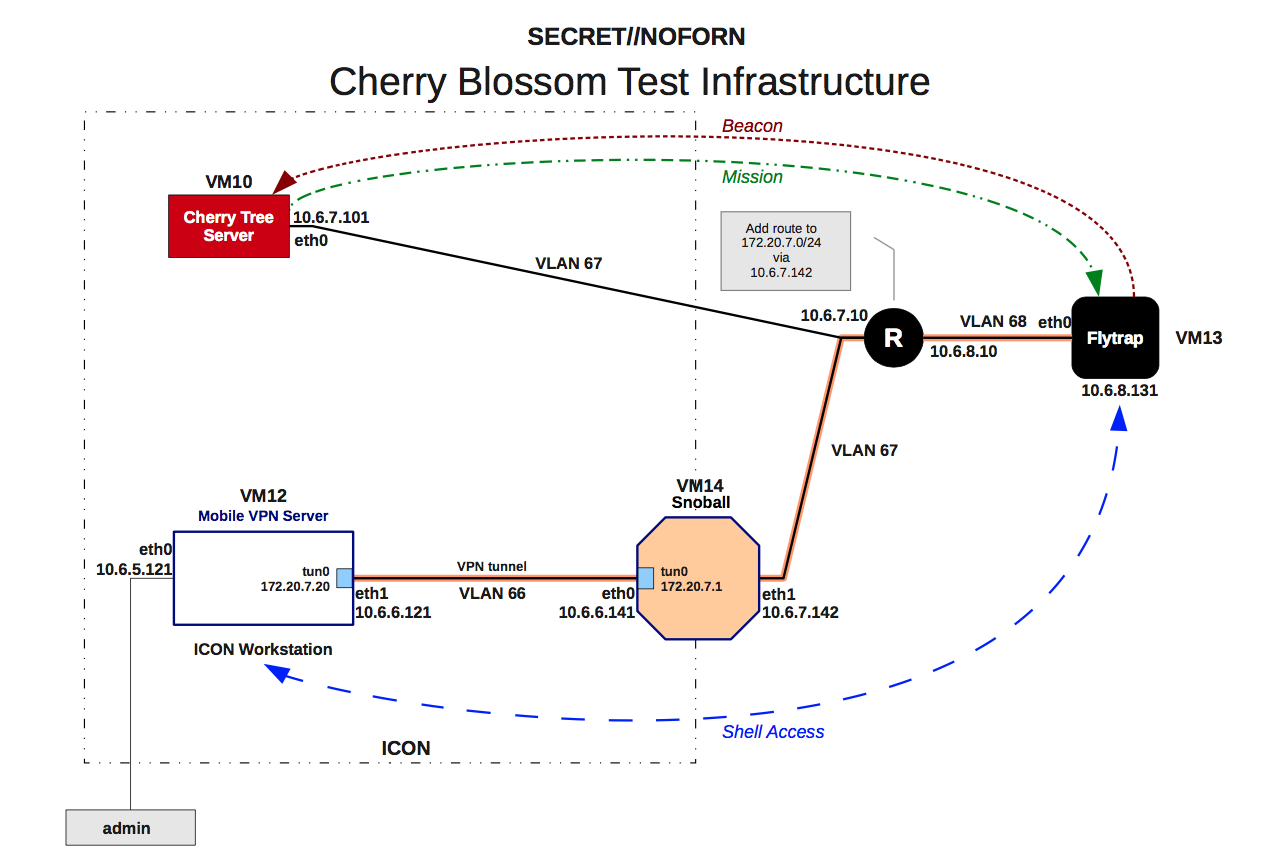
Cherry Blossom Infrastructure
Interestingly, any information transmitted by the infected router to the CIA server was encrypted. To gain access to it, cryptographic authentication is required, so a third-party person (for example, an information security specialist who discovered the router's access to a third-party server) could not decrypt this traffic.
The technical nuances of the CIA software package for routers are not new - there is nothing for specialists here that could be surprising. All this has been used by attackers and representatives of infobase for many years. But the CherryBlossom package, in principle, can be called the most functional of all ever used (of course, we are talking only about the software, about which something is known). There is a user-friendly interface, command-line management and a whole list of other features.
It is worth noting that the information about this software was discovered by WikiLeaks as part of the Vault7 mission. Previously, the resource has already laid out a large amount of information about spyware from the CIA, as well as the software itself. The CIA has not yet confirmed or denied any involvement, but there is nothing left for the management to do. However, information security experts who have studied this information claim that the CIA is involved in creating software and drafting technical documentation for it, there is no doubt about that.
This release of WikiLeaks has no source code or executable files. All this software, according to representatives of the resource, can fall into the wrong hands, and then the vulnerabilities of routers will be exploited with triple zeal. Laying out the software itself is a group of hackers Shadow Brokers, which, thus, protests against the policy of Donald Trump. Their work led to the spread of WCry malware, which infected 727,000 computers in 90 countries. However, it is not yet known whether these guys have software that WikiLeaks talks about or not.
All Articles