私はメールを「あるべきように」構成することにしました-SPF、DKIM、およびDMARCの構成を試みます。
私はすぐに予約をします-マクロを扱うことさえしなかったし、aspf / adkimを設定しませんでした(それらについては書きましたが)。
DMARCとは何ですか?
RFC7489で説明されています 。
DMARCは、このドメインの受信メールをチェックする方法と、メールがSPFまたはDKIM認証に合格しない場合の対処方法に関するポリシーを設定します。 写真は、DMARCが動作する段階を示しています。
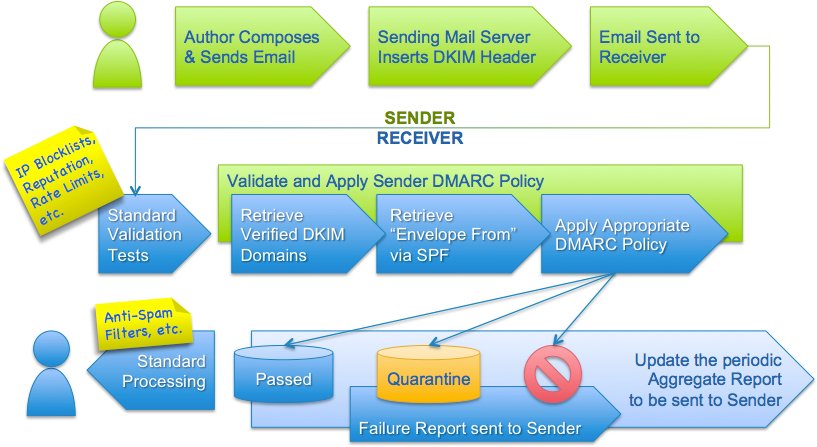
DMARCセットアップ
ドキュメントを読んで Zenを理解するか、最も基本的なポリシーを設定できます-非常に簡単に設定できます-エントリがドメインに追加されます
基本的なDMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- (
@domain.tld
) (
@srv1.domain.tld
,
@srv2.domain.tld
);
- (
postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC ,
quarantine
reject
, :
pct
- percentage - , , forensic report. ,
"v=DMARC1; p=quarantine; pct=50;"
.
pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - :
RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- (
@domain.tld
) (
@srv1.domain.tld
,
@srv2.domain.tld
);
- (
postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC ,
quarantine
reject
, :
pct
- percentage - , , forensic report. ,
"v=DMARC1; p=quarantine; pct=50;"
.
pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - :
RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld #3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld #3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- (@domain.tld
) (@srv1.domain.tld
,@srv2.domain.tld
);
- (postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC ,quarantine
reject
, :
pct
- percentage - , , forensic report. ,"v=DMARC1; p=quarantine; pct=50;"
.pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - :RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld #3 -sub
, #2 -domain
, #1 -tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
:tld
- #1,domain
- #2,sub
- #3,a
- #4
tld
, =1
2 -domain.tld
s
- strict - FQDNd= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- .quarantine
, 5% (pct=5
) , , 10-20-35-50-75-100%,reject
.
SPF/DKIMruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .
_dmarc.domain.tld IN TXT "v=DMARC1; p=;"
p
- policy - , :
none
- , ;
quarantine
- ;
reject
- .
. , :
DMARC
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
sp
- subdomain policy - policy;
rua
- reporting URI for aggregate reports - mailto:mbox@domain.tld XML
Mail.ru DMARC:
<feedback> <report_metadata> <date_range> <begin>1361304000</begin> <end>1361390400</end> </date_range> <email>dmarc_support@corp.mail.ru</email> <extra_contact_info>http://corp.mail.ru/en</extra_contact_info> <org_name>Mail.Ru</org_name> <report_id>1361304000874948</report_id> </report_metadata> <policy_published> <adkim>r</adkim> <aspf>r</aspf> <domain>adan.ru</domain> <p>none</p> <pct>100</pct> <sp>none</sp> </policy_published> <record> <auth_results> <dkim> <domain>adan.ru</domain> <result>pass</result> </dkim> <spf> <domain>adan.ru</domain> <result>pass</result> </spf> </auth_results> <identifiers> <header_from>adan.ru</header_from> </identifiers> <row> <count>20</count> <policy_evaluated> <disposition>none</disposition> <dkim>pass</dkim> <spf>pass</spf> </policy_evaluated> <source_ip>176.9.9.172</source_ip> </row> </record> </feedback>
ri
- requested interval - , , 86400. .
:
- ;
- ( @domain.tld
) ( @srv1.domain.tld
, @srv2.domain.tld
);
- ( postmaster@domain.tld
).
, , , . , , ...
DMARC
DMARC , quarantine
reject
, :
pct
- percentage - , , forensic report. , "v=DMARC1; p=quarantine; pct=50;"
. pct=100
.
aspf
- alignment mode for SPF - SPF:
r
- relaxed - RFC5322.From SPF- ( , ). , , RFC5321.MailFrom, "some.sub.domain.tld", RFC5322.From - "mbox@domain.tld";
s
- strict - RFC5321.MailFrom RFC5322.From .
adkim
- alignment mode for DKIM - DKIM, :
r
- relaxed - : RFC5322.From
d= , - :
/ Organizational Domains RFC:
Organizational Domain:
The domain that was registered with a domain name registrar. In the absence of more accurate methods, heuristics are used to determine this, since it is not always the case that the registered domain name is simply a top-level DNS domain plus one component (eg, "example.com", where "com" is a top-level domain). The Organizational Domain is determined by applying the algorithm found in Section 3.2.
...
The Organizational Domain is determined using the following algorithm:
1. Acquire a "public suffix" list, ie, a list of DNS domain names reserved for registrations. Some country Top-Level Domains (TLDs) make specific registration requirements, eg, the United Kingdom places company registrations under ".co.uk"; other TLDs such as ".com" appear in the IANA registry of top-level DNS domains. A public suffix list is the union of all of these. Appendix A.6.1 contains some discussion about obtaining a public suffix list.
2. Break the subject DNS domain name into a set of "n" ordered labels. Number these labels from right to left; eg, for "example.com", "com" would be label 1 and "example" would be label 2.
3. Search the public suffix list for the name that matches the largest number of labels found in the subject DNS domain. Let that number be "x".
4. Construct a new DNS domain name using the name that matched from the public suffix list and prefixing to it the "x+1"th label from the subject domain. This new name is the Organizational Domain.
Thus, since "com" is an IANA-registered TLD, a subject domain of "abcdexample.com" would have an Organizational Domain of "example.com".
The process of determining a suffix is currently a heuristic one. No list is guaranteed to be accurate or current.
1. " ", publicsuffix.org
2, , . - sub.domain.tld
#3 - sub
, #2 - domain
, #1 - tld
.
3. , , .
4. +1 - .
:
info@a.sub.domain.tld
: tld
- #1, domain
- #2, sub
- #3, a
- #4
tld
, =1
2 - domain.tld
s
- strict - FQDN d= RFC5322.From
.
ruf
- reporting URI for forensic reports - . (, Gmail ).
fo
- failure report options - forensic report:
0
- - ;
1
- ;
d
- DKIM;
s
- SPF.
DMARC?
:
DMARC, :
_dmarc.domain.tld IN TXT "v=DMARC1; p=none; sp=none; rua=mailto:postmaster@domain.tld"
- . quarantine
, 5% ( pct=5
) , , 10-20-35-50-75-100%, reject
.
SPF/DKIM ruf=mailto:your-mbox@domain.tld
fo=1 .
, , - , .