この記事では、アルゴリズムのコンポーネントについて詳しく説明し、マット部分を少し掘り下げて、Pythonでの実装例を示します。 開発では、標準ライブラリの一部のみに限定しました。
ちょっとした紹介
Advanced Encryption Standardは、2人のベルギーの暗号作成者Joan DimenとVincent Raymanによって開発されたRijndaelアルゴリズム([rɛindaːl])の有名な名前です。 アルゴリズムはブロック状で対称的です。 米国政府機関のデータ暗号化標準として採用されました。 最近高く評価されている国家安全保障局は文書を保存するためにそれを使用しています:SECRETレベルまで、128ビットのキーによる暗号化が使用され、TOP SECRET情報には192または256ビットのキーが必要です。 高い暗号強度に加えて、アルゴリズムは最も複雑な数学ではありません。
多くの暗号化
動作させるには、暗号化オブジェクトとしてのバイトセットと、復号化中に必要となる秘密キーが必要です。 長いキーを頭に入れておくのは不便であり、キーの長さは128ビットで、アクセスできないほど十分であると考えられているため、オプション192/256を見ていません。 さらに、 ここで述べたように 、特定の条件下では、長いキーは安定性に遅れることがあります。
いくつかの表記法を紹介します。
- 状態は暗号化の中間結果であり、4行とNb列の長方形のバイト配列として表すことができます。 各状態セルには1バイトの値が含まれます
- Nbは、Stateを構成する列(32ビットワード)の数です。 標準Nb = 4に対して規制
- Nkは32ビットワードのキーの長さです。 AESの場合、Nk = 4、6、8。Nk = 4を使用することを既に決定しています。
- Nr-暗号化のラウンド数。 キーの長さに応じて、Nr = 10、12、または14
アルゴリズムには4つの変換があり、それぞれ独自の方法でStateの状態に影響を与え、最終的に結果を導きます: SubBytes()、ShiftRows()、MixColumns() 、 AddRoundKey() 。 一般的な暗号化スキームは次のように表すことができます。
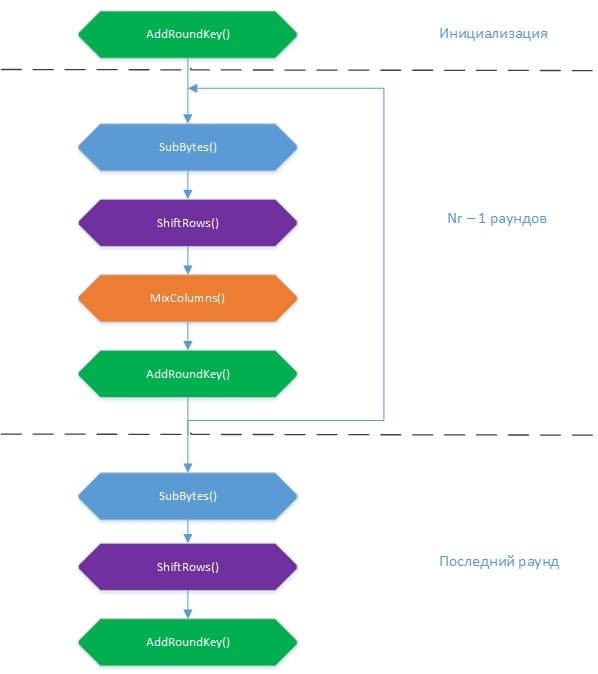
最初に、State配列には、式State [r] [c] = input [r + 4c]、r = 0.1 ... 4;に従って入力値が入力されます。 c = 0.1..Nb つまり、列で。 16バイトのブロックは一度に暗号化されます。

アルゴリズムはバイトで動作し、それらを有限体またはガロア体GF(2 8 )の要素と見なします。 括弧内の数字は、フィールド要素の数またはその力です。 体GF(2 8 )の要素は最大7の次数の多項式であり、係数の行で指定できます。 バイトは、多項式として非常に簡単に表現できます。 たとえば、バイト{1,1,1,0,0,0,1,1,1}は、フィールド要素1x 7 + 1x 6 + 1x 5 + 0x 4 + 0x 3 + 0x 2 + 1x 1 + 1x 0 = 1x 7 +に対応します。 1x 6 + 1x 5 + x +1。 フィールド要素を操作するという事実は、加算および乗算演算のルールを変更するため、非常に重要です。 これについては少し後で触れます。
次に、各変換について詳細に検討します。
SybButes()
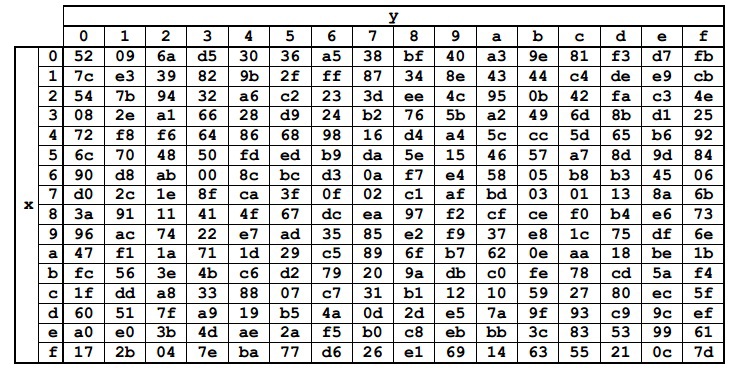
変換は、Stateの各バイトをSbox定数テーブルの対応するバイトに置き換えることです。 Sbox要素の値は16進表記で表されます。 テーブル自体は、既知のフィールドGF(2 8 )を変換することによって取得されました
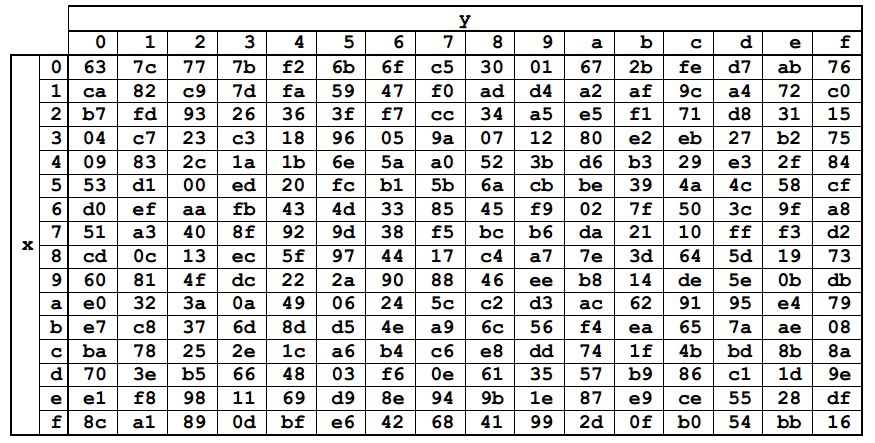
Stateの各バイトは、16進表記で{xy}として表すことができます。 次に、行xと列yの交点にある要素に置き換えます。 たとえば、{6e}は{9f}に、{15}は{59}に置き換えられます。
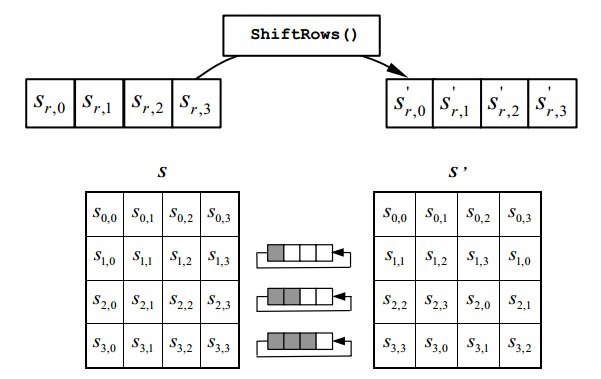
ShiftRows()
簡単な変換。 最初の行に1要素、2番目に2、3番目に3の循環左シフトを実行します。 ゼロラインはシフトされません。
MixColumns()
この変換の一部として、Stateの各列は多項式として表され、フィールドGF(2 8 )でx 4 + 1を法とする固定多項式3x 3 + x 2 + x + 2で乗算されます。 。 標準の公式ドキュメントで提供されている同等のマトリックスエントリを見ると、図はより単純になります。

行列を乗算する場合、a ijの値は、最初の行列のi番目の行と2番目の行列のj番目の列の対応する要素の積の合計として取得されます。
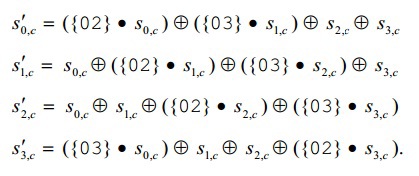
ここで、加算と乗算の通常のルールの動作不能を思い出す必要があります。
新しいルール:
- フィールドGF(2 8 )での加算は、演算XORと同等です。
- {01}による乗算は、乗算を変更しません
- {02}による乗算はルールに従って実行されます。乗算された値が{80}より小さい場合、左に1ビットシフトされます。 乗算値が{80}以上の場合、最初に左に1ビットシフトされ、次に値{1b}のXOR演算がシフトの結果に適用されます。 結果は、値{ff}をスキップできます。つまり、1バイトの境界を超えています。 この場合、結果を{100}で割った余りを返す必要があります。
- 他の定数による乗算は、前の
当然、これらは最終フィールドの算術の一般的な規則ではありませんが、アルゴリズムの一部として、暗号化のために3つの定数と復号化のために4つの定数を掛ける必要があるため、このようなローカルライフハックで十分です。
MixColumns()とShiftRows()は、暗号に拡散を追加します。
AddRoundKey()
変換により、Stateの各要素とRoundKeyの対応する要素のビット単位のXORが生成されます。 RoundKeyはStateと同じサイズの配列であり、KeyExpansion()関数を使用して秘密鍵に基づいてラウンドごとに構築されます。これについては後で検討します。
KeyExpansion()
この補助変換は、ラウンドキーのセット-KeyScheduleを形成します。 KeyScheduleは、Nb *(Nr + 1)列または(Nr + 1)ブロックで構成される長いテーブルで、それぞれのサイズはStateと同じです。 最初のラウンドキーは、計算した秘密鍵に基づいて記入されます。
KeySchedule [r] [c] = SecretKey [r + 4c]、r = 0.1 ... 4; c = 0,1..Nk。
KeyScheduleでは、さらなる操作が可能になるようにバイトを入力する必要があることは明らかです。 このアルゴリズムをホーム暗号化に使用する場合、数字のシーケンスを頭に保存することはまったく便利ではないため、実装ではKeyExpansion()はプレーンテキスト入力を取得し、各文字に
ord()
を使用して、結果をKeyScheduleセルに書き込みます。 これは制限を意味します:長さが16文字以下であり、バイトを
ord()
文字の
ord()
バイナリで255または11111111を超える値を返すべきではありません。そうでない場合、出力で不正な暗号化を受け取ります。 ロシア語のキーを使用すると、暗号化が機能しないことが判明しました。
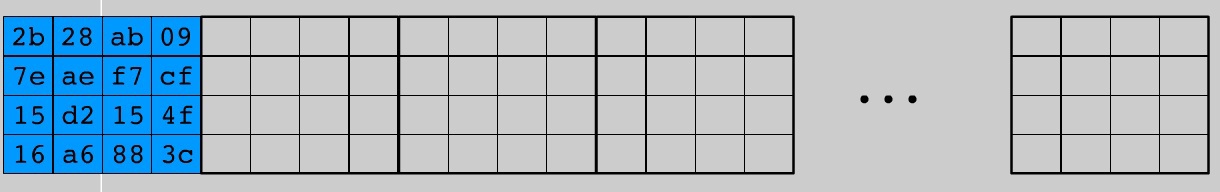
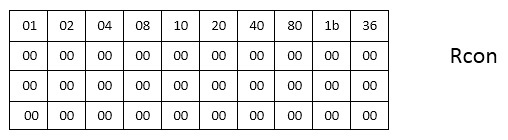
図は、AES-128のKeyScheduleレイアウトを示しています。4列の11ブロック。 アルゴリズムの他のバリエーションでは、Nb列の(Nr + 1)ブロックがそれぞれあります。 次に、空のスペースを埋める必要があります。 変換のために、定数テーブルが再び定義されます-Rcon-値は16進数システムです。
KeySchedule補充アルゴリズム:
- 各反復で、テーブル列を操作します。 列0、..、(Nk-1)には、すでに秘密の単語の値が事前に入力されています。 列番号Nkから始めます(この場合、4番目から)
- 列番号W iが Nkの倍数である場合(この場合、4番目ごと)、列W i-1を取得し、1要素だけ循環左シフトを実行し、すべての列バイトをSubBytes()のようにSboxテーブルの対応するものに置き換えます。 次に、W i-1列を修正したW i- Nk列とRcon i / Nk-1列をXOR演算します。 結果はW i列に書き込まれます。 わかりやすくするために、i = 4の図を示します。
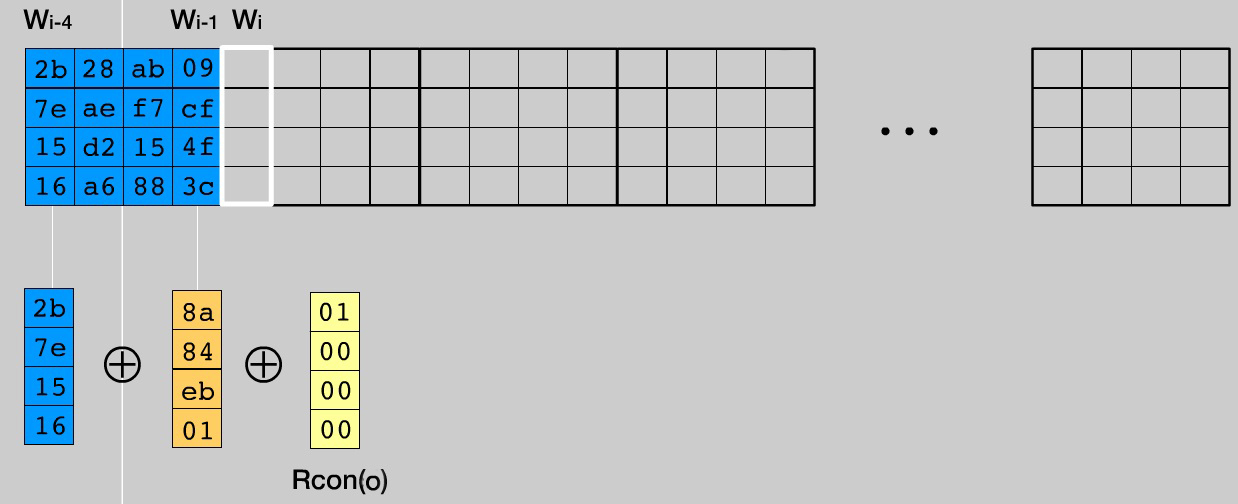
- 残りの列では、W i-NkとW i-1の間でXORを実行します。 結果はW iで書き込まれます
この補助的な変換は、アルゴリズムではMixColumns()で数学が認識された後、書面で最もボリュームがあり、おそらく最も複雑です。 暗号化キーは、4 * Nk個の要素で構成する必要があります(この例では16)。 しかし、私たちはこれをすべて家庭で使用するために行っているので、誰もが16文字のキーを思いついてそれを覚えているとは限りません。 したがって、長さが16未満の行が入力に到着すると、KeyScheduleのIは値{01}を標準に追加します。
KeyExpansion()コード
def key_expansion(key): key_symbols = [ord(symbol) for symbol in key] # ChipherKey shoul contain 16 symbols to fill 4*Nk table. If it's less # complement the key with "0x01" if len(key_symbols) < 4*nk: for i in range(4*nk - len(key_symbols)): key_symbols.append(0x01) # make ChipherKey(which is base of KeySchedule) key_schedule = [[] for i in range(4)] for r in range(4): for c in range(nk): key_schedule[r].append(key_symbols[r + 4*c]) # Comtinue to fill KeySchedule for col in range(nk, nb*(nr + 1)): # col - column number if col % nk == 0: # take shifted (col - 1)th column... tmp = [key_schedule[row][col-1] for row in range(1, 4)] tmp.append(key_schedule[0][col-1]) # change its elements using Sbox-table like in SubBytes... for j in range(len(tmp)): sbox_row = tmp[j] // 0x10 sbox_col = tmp[j] % 0x10 sbox_elem = sbox[16*sbox_row + sbox_col] tmp[j] = sbox_elem # and finally make XOR of 3 columns for row in range(4): s = key_schedule[row][col - 4]^tmp[row]^rcon[row][col/nk - 1] key_schedule[row].append(s) else: # just make XOR of 2 columns for row in range(4): s = key_schedule[row][col - 4]^key_schedule[row][col - 1] key_schedule[row].append(s) return key_schedule
前述のように、KeyScheduleはAddRoundKey()の変換に使用されます。 初期化ラウンドでは、ラウンドキーは最初に0、..、3の数字の列、4、..、7などの数字になります。 AddRoundKey()の全体的なポイントは、XOR状態とラウンドキーを生成することです。
実際、これはすべて暗号化プロセスに関するものです。 暗号化されたバイトの出力配列は、式output [r + 4c] = State [r] [c]、r = 0.1 ... 4;に従ってStateからコンパイルされます。 c = 0.1..Nb その間、記事は遅れているため、ここですぐに復号化手順について説明します。
すぐに解読について
ここでの考え方は単純です。同じキーワードを使用して暗号化変換と逆の変換シーケンスを実行すると、元のメッセージが取得されます。 このような逆変換は、 InvSubBytes()、InvShiftRows()、InvMixColumns()、およびAddRoundKey()です。 復号化アルゴリズムの一般的なスキーム:
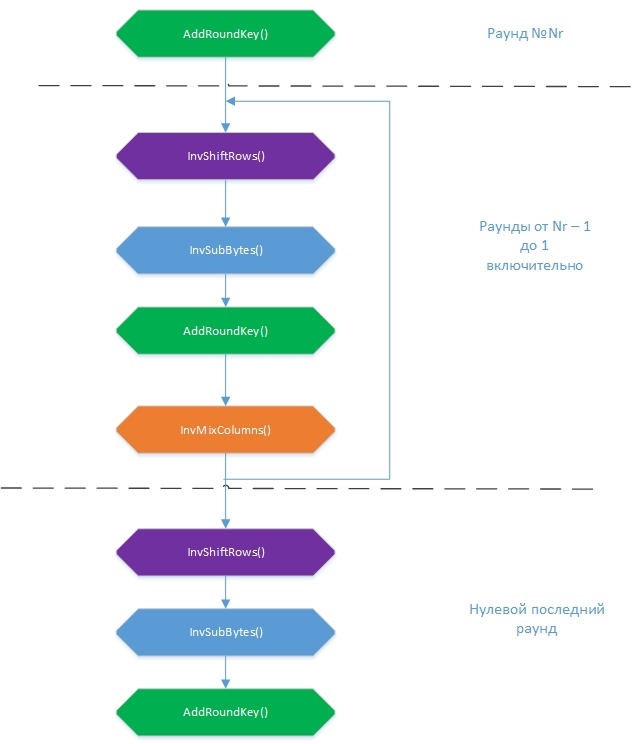
ラウンドキーをAddRoundKey()に追加する順序は、Nr + 1から0の逆順であることに注意してください。最初は、暗号化と同様に、状態テーブルは入力バイトの配列から形成されます。 その後、各ラウンドで変換が実行され、その最後に復号化されたファイルを取得する必要があります。 変換の順序が少し変更されました。 最初のInvSubBytes()またはInvShiftRows()は重要ではありません。1つはバイト値で動作し、2つ目はこれらの値を変更せずにバイトを再配置しますが、標準の擬似コードでの変換シーケンスに従いました。
InvSubBytes()
SubBytes()とまったく同じように機能しますが、置き換えはInvSbox定数テーブルから行われます。
残りの逆変換も、直接対応するものと非常によく似ているため、コードではそれらに個別の関数を選択していません。 変換を記述する各関数には
inv
変数があります。
False
場合、関数は通常モードまたは直接モード(暗号化)で動作し、
True
場合-逆モード(復号化)で動作します。
コード
def sub_bytes(state, inv=False): if inv == False: # encrypt box = sbox else: # decrypt box = inv_sbox for i in range(len(state)): for j in range(len(state[i])): row = state[i][j] // 0x10 col = state[i][j] % 0x10 # Our Sbox is a flat array, not a bable. So, we use this trich to find elem: box_elem = box[16*row + col] state[i][j] = box_elem return state
InvShiftRows()
変換は、状態の最初の行に1要素、2番目に2要素、3番目に3要素ずつ右に循環します。 ゼロ線は回転しません。
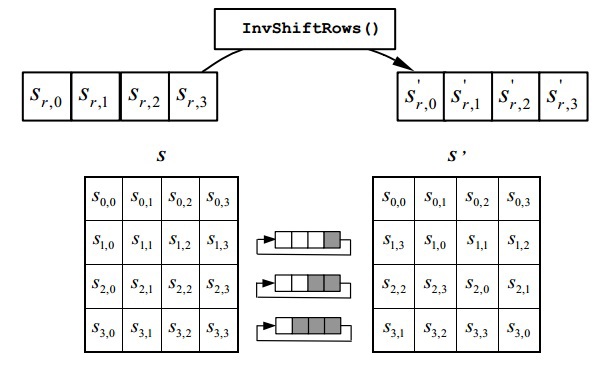
コードの説明:
left_shift/right_shift(array, count)
入力
array
を対応する方向に
count
回回転させます
コード
def shift_rows(state, inv=False): count = 1 if inv == False: # encrypting for i in range(1, nb): state[i] = left_shift(state[i], count) count += 1 else: # decryption for i in range(1, nb): state[i] = right_shift(state[i], count) count += 1 return state
InvMixColumns()
操作は同じですが、各State列には異なる多項式{0b} x 3 + {0d} x 2 + {09} x + {0e}が乗算されます。 マトリックス形式では、次のようになります。

または既製の数式。 もちろん、すべての値は16進表記です。

ここでは、数学に向かって脱線し、{02}より大きい定数で乗算する関数を取得する方法を説明する必要があります。 私が言ったように、それらは{01}と{02}を介してそれらを分解することによって得られます、すなわち:
コンバージョン数
n * {03} = n *({02} + {01})= n * {02} + n * {01}
n * {09} = n *({08} + {01})= n * {02} * {02} * {02} + n * {01}
n * {0b} = n *({08} + {02} + {01})= b * {02} * {02} * {02} + n * {02} + n * {01}
n * {0d} = n *({08} + {04} + {01})= n * {08} + n * {04} + n * {01} = n * {02} * {02} * {02} + n * {02} * {02} + n * {01}
n * {0} = n *({08} + {04} + {02} = n * {08} + n * {04} + n * {02} = n * {02} * {02} * { 02} + n * {02} * {02} + b * {02}
n * {09} = n *({08} + {01})= n * {02} * {02} * {02} + n * {01}
n * {0b} = n *({08} + {02} + {01})= b * {02} * {02} * {02} + n * {02} + n * {01}
n * {0d} = n *({08} + {04} + {01})= n * {08} + n * {04} + n * {01} = n * {02} * {02} * {02} + n * {02} * {02} + n * {01}
n * {0} = n *({08} + {04} + {02} = n * {08} + n * {04} + n * {02} = n * {02} * {02} * { 02} + n * {02} * {02} + b * {02}
もちろん、別の方法で数字を分解することもできますが、分解が個人的に検証されます
n * {09} = n * {03} + n * {03} + n * {03}
対応する関数を呼び出すと、間違った結果が得られます(結果を含む参照テーブルは、ソースリストのリンクの1つにあります)。 彼は、代替の(コメント付き)バージョンの計算を特別に残しました。これは、それらがより理解しやすく、エレガントであるが、何らかの理由で正しく動作しないためです。
補助乗算関数
def mul_by_02(num): if num < 0x80: res = (num << 1) else: res = (num << 1)^0x1b return res % 0x100 def mul_by_03(num): return mul_by_02(num)^num def mul_by_09(num): #return mul_by_03(num)^mul_by_03(num)^mul_by_03(num) - works wrong, I don't know why return mul_by_02(mul_by_02(mul_by_02(num)))^num def mul_by_0b(num): #return mul_by_09(num)^mul_by_02(num) return mul_by_02(mul_by_02(mul_by_02(num)))^mul_by_02(num)^num def mul_by_0d(num): #return mul_by_0b(num)^mul_by_02(num) return mul_by_02(mul_by_02(mul_by_02(num)))^mul_by_02(mul_by_02(num))^num def mul_by_0e(num): #return mul_by_0d(num)^num return mul_by_02(mul_by_02(mul_by_02(num)))^mul_by_02(mul_by_02(num))^mul_by_02(num)
コードの説明: MixColumns()に関するセクションで説明した規則に従って、関数
mul_by_<>
にGF(2 8 )の対応する定数を乗算します。
コード
def mix_columns(state, inv=False): for i in range(nb): if inv == False: # encryption s0 = mul_by_02(state[0][i])^mul_by_03(state[1][i])^state[2][i]^state[3][i] s1 = state[0][i]^mul_by_02(state[1][i])^mul_by_03(state[2][i])^state[3][i] s2 = state[0][i]^state[1][i]^mul_by_02(state[2][i])^mul_by_03(state[3][i]) s3 = mul_by_03(state[0][i])^state[1][i]^state[2][i]^mul_by_02(state[3][i]) else: # decryption s0 = mul_by_0e(state[0][i])^mul_by_0b(state[1][i])^mul_by_0d(state[2][i])^mul_by_09(state[3][i]) s1 = mul_by_09(state[0][i])^mul_by_0e(state[1][i])^mul_by_0b(state[2][i])^mul_by_0d(state[3][i]) s2 = mul_by_0d(state[0][i])^mul_by_09(state[1][i])^mul_by_0e(state[2][i])^mul_by_0b(state[3][i]) s3 = mul_by_0b(state[0][i])^mul_by_0d(state[1][i])^mul_by_09(state[2][i])^mul_by_0e(state[3][i]) state[0][i] = s0 state[1][i] = s1 state[2][i] = s2 state[3][i] = s3 return state
AddRoundKey()
XOR演算のプロパティにより、この変換はそれ自体に反比例します。
(a XOR b)XOR b = a
したがって、それを変更する必要はありません。 ラウンドキーのセットは、KeyExpansion()関数を使用した暗号化と同じ方法で形成されますが、ラウンドキーは逆の順序で置き換える必要があります。
コード
def add_round_key(state, key_schedule, round=0): for col in range(nk): # nb*round is a shift which indicates start of a part of the KeySchedule s0 = state[0][col]^key_schedule[0][nb*round + col] s1 = state[1][col]^key_schedule[1][nb*round + col] s2 = state[2][col]^key_schedule[2][nb*round + col] s3 = state[3][col]^key_schedule[3][nb*round + col] state[0][col] = s0 state[1][col] = s1 state[2][col] = s2 state[3][col] = s3 return state
これで、書くための包括的な変換関数のセットができました。
暗号化機能
def encrypt(input_bytes, key): # let's prepare our input data: State array and KeySchedule state = [[] for j in range(4)] for r in range(4): for c in range(nb): state[r].append(input_bytes[r + 4*c]) key_schedule = key_expansion(key) state = add_round_key(state, key_schedule) for rnd in range(1, nr): state = sub_bytes(state) state = shift_rows(state) state = mix_columns(state) state = add_round_key(state, key_schedule, rnd) state = sub_bytes(state) state = shift_rows(state) state = add_round_key(state, key_schedule, rnd + 1) output = [None for i in range(4*nb)] for r in range(4): for c in range(nb): output[r + 4*c] = state[r][c] return output
復号化機能
def decrypt(cipher, key): # let's prepare our algorithm enter data: State array and KeySchedule state = [[] for i in range(nb)] for r in range(4): for c in range(nb): state[r].append(cipher[r + 4*c]) key_schedule = key_expansion(key) state = add_round_key(state, key_schedule, nr) rnd = nr - 1 while rnd >= 1: state = shift_rows(state, inv=True) state = sub_bytes(state, inv=True) state = add_round_key(state, key_schedule, rnd) state = mix_columns(state, inv=True) rnd -= 1 state = shift_rows(state, inv=True) state = sub_bytes(state, inv=True) state = add_round_key(state, key_schedule, rnd) output = [None for i in range(4*nb)] for r in range(4): for c in range(nb): output[r + 4*c] = state[r][c] return output
これらの2つの関数は、暗号化または暗号化されていないバイトのリストと、シークレットキーワードを含むプレーンテキスト文字列を受け取ります。
結論、興味深いリンク
記事はかなり長いことが判明しました。 私は写真でテキストを希釈しようとしましたが、それはあなたにとって興味深いものであり、誰も退屈しなかったと思います。 この記事に記載されているコードは完全なものではありません。 定数テーブルのグローバル宣言、MixColumns()の小さな関数は挿入しませんでしたが、それらはどこかにあると説明した言葉でのみ挿入しました。 私がPRであるとは考えないでください。しかし、完全に結合されたコードはリポジトリで取得できます 。 また、ファイルへのパスを指定し、秘密鍵を入力し、ソースと同じディレクトリにある暗号化されたファイルを取得することができる控えめなCLIインターフェイスもあります(復号化されたファイルは同じ方法で取得できます)。 健康に暗号化してください!
そして最後に、1つの重要なニュアンスについて話す必要があります-パディングまたはブロックへの追加。 AESはブロック暗号化アルゴリズムであり、
encrypt()/decrypt()
関数は入力バイトの正確に1ブロックを使用します(128ビットキーを使用するバージョンの場合、これは16バイトです)。 ファイルの最後には、1つのブロックを形成しない1〜15バイトが残っています。 暗号化せずに単純に宛先ファイルに送信できますが、場合によっては、ファイルの最後に重要なものが含まれている可能性があり、このオプションは適切ではありません。 2番目のオプションは、ブロック暗号に関するウィキペディアの記事で提案されました。
受信者はペイロードの終わりを見つけることができないため、ゼロビットを単純に追加しても問題は解決しません。 さらに、このオプションは、Oracleアドオンによる攻撃につながります。 したがって、実際には、ISO / IEC 9797-1で「追加方法2」として標準化されたソリューションが適用可能で、メッセージの最後に1ビットを追加し、残りのスペースをゼロで埋めます。 この場合、そのような攻撃に対する抵抗性が証明されました。
それで私はしました(最初のオプションは残っていましたが、コメントアウトしました。突然、便利になりました)。
ソース選択:
- 公式文書
- アルゴリズムの暗号化部分の非常に明確な視覚的解釈 。 著者が私を訴えないように、私はそこからスクリーンショットを数枚撮りました。
- ウィキペディアなしではどこにもありません
- MixColumns()に関する別の記事 。 0〜255の数字のリストにGFフィールドの暗号で使用される定数(2 8 )を乗算した結果のテーブルが含まれています。
- AESの歴史とアルゴリズム自体についての面白い漫画 。 すでに記事を書いていたときに初めて見つけたのは残念です。