だから挑戦。 Ubuntu 12.04を搭載したサーバーがあります。 彼はなる必要があります:
- Active Directoryを備えたPDC Windowsドメイン。
- Radiusサーバーでの承認を伴うVPNサーバー(たとえば、PPTPとしますが、MS-CHAP v2およびMPPE-128を強制的にサポートします)。
- それに応じて-Freeradiusサーバーによって。
- ADユーザーが透過的にログインするターミナルサーバー。
降りる。
Samba4を置く
Samba4 / HOWTOを注意深く読みました。 インストールの開始時に、Samba4 -4.0.0rc2の次のバージョンが利用可能でした。 今、私が知る限り-4.0.0rc3。 RC2を使用して説明します。
HOWTOの指示に従ってすべてを行いますが、いくつかのニュアンスを忘れないでください。
- 結局のところ、LinuxコンピューターでADユーザーを認証する必要がありますか? 次に、システムにlibpam0g-devパッケージをインストールすることを忘れないでください( sudo apt-get install libpam0g-dev )。 これらのライブラリがないと、Pambaはsamba4でサポートされません(必要なpam_winbind.soライブラリを含む/ usr / local / samba / lib / security /ディレクトリはビルドされたプロジェクトには存在しません)。
- (強く!) ./configureの代わりに./configure.developerを使用することをお勧めします。
次に、 WiKi Samba4 HOWTOの説明に従ってください 。 ビルドされたsamba4は、ディレクトリ/ usr / local / samba /に配置されます。 繰り返しますが、すべてのsamba4バイナリは/ usr / local / samba / bin /ディレクトリにあり 、サービスは/ usr / local / samba / sbin /ディレクトリにあるため、絶対パスを使用してアクセスするか、修正する必要があることに注意してくださいPATH変数、または-私が行ったように、samba4をsamba3なしのマシンに置いた場合-すべてのファイルのシンボリックリンクをディレクトリ/ usr / local / samba / bin /からディレクトリ/ usr / bin /に、ディレクトリ/ usr / local /から作成するsamba / sbin / -ディレクトリ/ usr / sbin /へ 。
HOWTOの説明に従って、samba4のプロビジョニングを行います。 とりわけ、この手順は/ usr / local / samba / etc /ディレクトリにメインのsamba構成ファイル-smb.confを作成します。これには必要なオプションと「ボール」を追加し、... sambaを実行します。 これは私の/usr/local/samba/etc/smb.confのようなものです:
# Global parameters [global] dos charset = CP860 workgroup = <DOMAIN> # NetBIOS realm = <domain.-> # netbios name = <NetBIOS_Name> # NetBIOS server role = active directory domain controller dns forwarder = 127.0.0.1 # dns-. template shell = /bin/bash # , – … winbind use default domain = Yes winbind enum users = Yes winbind enum groups = Yes [netlogon] path = /usr/local/samba/var/locks/sysvol/uchteno.local/scripts read only = No [sysvol] path = /usr/local/samba/var/locks/sysvol read only = No #[profiles] # path = /var/lib/samba/profiles # read only = no # browseable = No # «», .
/ etc / init /ディレクトリでsamba4を実行するには、 次の内容のsamba4.confファイルを作成します。
description "SMB/CIFS File and Active Directory Server" author "Jelmer Vernooij <jelmer@ubuntu.com>" start on (local-filesystems and net-device-up) stop on runlevel [!2345] expect fork normal exit 0 pre-start script [ -r /etc/default/samba4 ] && . /etc/default/samba4 install -o root -g root -m 755 -d /var/run/samba install -o root -g root -m 755 -d /var/log/samba end script exec /usr/local/samba/sbin/samba –D
サービスの開始/停止は次のとおりです。
# service samba4 start # service samba4 stop # service samba4 restart
DNSを設定するには、 ゾーンを含むbind9はこのサーバーで既に実行されており、独自のビルトインDNSサーバーを持つsamba4は、既に構成されたbind9と「友達を作る」ことを望みませんでした。バインド9。
それ以外はすべて、上記のHOWTOに厳密に従っており、いくつかのコメントがあります。
- Windows 7にインストールされているWindowsリモート管理ツールパッケージには、2つの不快な機能があります(これまでのところ2つに気付きました)。
-まず、ユーザープロパティのADUCスナップインには、「ダイヤルイン」タブがまったくありません(またはロシア語ではどうですか?)。したがって、他の方法でユーザーのリモートアクセス設定を行う必要があります。
-第二に、特別に作成されたユーザーがすべての可能なグループに含まれていたにもかかわらず、グループポリシーの管理は管理者アカウントでのみ可能です... - 正直なところ、samba4でのグループポリシーの可能性を詳細に把握するまでは...
したがって、samba4がインストールされ、実行されています。 LinuxでのADユーザー認証の番です
Winbindセットアップ
Wiki Samba4 / Winbindのドキュメントにアクセスして、そこに書かれているALL-ALL-ALLを実行します。 /etc/nsswitch.confに変更を加えた後、システムを再起動することを忘れないでください。一般的には、再起動が必要です。 /etc/pam.d/内のファイルに注意してください。間違えた場合、サーバーが「ブラックボックス」に変わるので、 sshまたはコンソールからアクセスすることはできません...エラーなしですべてを実行した場合-これで、Active DirectoryユーザーアカウントでLinuxサーバーにログインできます!
ただし、必要なアクションを一覧表示し、すべての(動作している!)設定ファイルを一覧表示して、すべてが1か所に収まるようにします。
だから。
ライブラリlibnss_winbind.soを使用可能にします 。
# ln -s /usr/local/samba/lib/libnss_winbind.so.2 /lib/libnss_winbind.so # ln -s /lib/libnss_winbind.so /lib/libnss_winbind.so.2
/etc/nsswitch.confを編集します。
#/etc/nsswitch.conf
passwd: compat winbind group: compat winbind shadow: compat hosts: files dns networks: files protocols: db files services: db files ethers: db files rpc: db files netgroup: nis
この編集後、すぐに再起動してください!
winbindのテスト。 はい、システムにそのようなプロセスがないことに恥ずかしがらないでください-sambaデーモンがすべての機能を実行するようになりました。
Winbindの可用性:
$ /usr/local/samba/bin/wbinfo -p Ping to winbindd succeeded
Winbindはドメインユーザーのリストを返します。
$ /usr/local/samba/bin/wbinfo -u ... <_>\Administrator ...
getent passwdは、Linuxとドメインの両方のすべてのユーザーのリストを提供します。
$ getent passwd root:x:0:0… ... <_>\Administrator:x:0:100::/home/MATWS/Administrator:/bin/false ...
idコマンドは、ドメインユーザーに関する情報を返します。
$ id Administrator uid=0(root) gid=100(users) groupes=0(root),100(users),3000004(Group Policy Creator Owners),3000008(Domain Admins)
samba4の「調達」段階で作成された管理者ドメインユーザーは、uid = 0であり、その後のすべての結果に注意してください。
パムのセットアップ
まず、 pam_winbind.soライブラリを利用可能にします :
# ln -s /usr/local/samba/lib/security/pam_winbind.so /lib/security
/etc/pam.d/ディレクトリーで以下のファイルを構成します。
/etc/pam.d/common-auth
# # /etc/pam.d/common-auth - authentication settings common to all services # # This file is included from other service-specific PAM config files, # and should contain a list of the authentication modules that define # the central authentication scheme for use on the system # (eg, /etc/shadow, LDAP, Kerberos, etc.). The default is to use the # traditional Unix authentication mechanisms. # # As of pam 1.0.1-6, this file is managed by pam-auth-update by default. # To take advantage of this, it is recommended that you configure any # local modules either before or after the default block, and use # pam-auth-update to manage selection of other modules. See # pam-auth-update(8) for details. # here are the per-package modules (the "Primary" block) auth sufficient pam_winbind.so auth [success=1 default=ignore] pam_unix.so nullok_secure use_first_pass # here's the fallback if no module succeeds auth requisite pam_deny.so # prime the stack with a positive return value if there isn't one already; # this avoids us returning an error just because nothing sets a success code # since the modules above will each just jump around auth required pam_permit.so # and here are more per-package modules (the "Additional" block) # end of pam-auth-update config
/etc/pam.d/common-account :
# # /etc/pam.d/common-account - authorization settings common to all services # # This file is included from other service-specific PAM config files, # and should contain a list of the authorization modules that define # the central access policy for use on the system. The default is to # only deny service to users whose accounts are expired in /etc/shadow. # # As of pam 1.0.1-6, this file is managed by pam-auth-update by default. # To take advantage of this, it is recommended that you configure any # local modules either before or after the default block, and use # pam-auth-update to manage selection of other modules. See # pam-auth-update(8) for details. # # here are the per-package modules (the "Primary" block) account sufficient pam_winbind.so account [success=1 new_authtok_reqd=done default=ignore] pam_unix.so # here's the fallback if no module succeeds account requisite pam_deny.so # prime the stack with a positive return value if there isn't one already; # this avoids us returning an error just because nothing sets a success code # since the modules above will each just jump around account required pam_permit.so # and here are more per-package modules (the "Additional" block) # end of pam-auth-update config
/etc/pam.d/common-session :
# # /etc/pam.d/common-session - session-related modules common to all services # # This file is included from other service-specific PAM config files, # and should contain a list of modules that define tasks to be performed # at the start and end of sessions of *any* kind (both interactive and # non-interactive). # # As of pam 1.0.1-6, this file is managed by pam-auth-update by default. # To take advantage of this, it is recommended that you configure any # local modules either before or after the default block, and use # pam-auth-update to manage selection of other modules. See # pam-auth-update(8) for details. # here are the per-package modules (the "Primary" block) session [default=1] pam_permit.so # here's the fallback if no module succeeds session requisite pam_deny.so # prime the stack with a positive return value if there isn't one already; # this avoids us returning an error just because nothing sets a success code # since the modules above will each just jump around session required pam_permit.so # The pam_umask module will set the umask according to the system default in # /etc/login.defs and user settings, solving the problem of different # umask settings with different shells, display managers, remote sessions etc. # See "man pam_umask". session required pam_mkhomedir.so session required pam_winbind.so session optional pam_umask.so # and here are more per-package modules (the "Additional" block) session required pam_unix.so session optional pam_ck_connector.so nox11 # end of pam-auth-update config
これで、ドメインユーザーとしてLinuxコンピューターにログインできるようになりました。
フリー半径
次のステップでは、freeradiusサーバーをインストールして構成し、pptpdをActive DirectoryデータとMS-CHAP v2およびMPPE-128プロトコルを使用してfreeradiusと連動するように構成します。 また、samba3を使用してMS-CHAP v2を実装する必要があり、さらにクールなことに、samba4とradius-serverを異なるマシンに分離する必要があるとは思わないでください!
そのため、ここでもWiKi Samba4 / HOWTO / Virtual_Private_Networkを出発点として使用します。 しかし、文字通りではありません。 降りる。
freeradiusをインストールします。
sudo apt-get install freeradius freeradius-common freeradius-krb5 freeradius-ldap freeradius-utils radiusclient1
前述のWiKiの記事と比較して、radiusclient1パッケージのインストールがここに追加されることに注意してください。これは、pptpdがradiusプラグインで動作するために必要です。
freeradiusの構成。 この/etc/freeradius/radiusd.confがあります:
prefix = /usr exec_prefix = /usr sysconfdir = /etc localstatedir = /var sbindir = ${exec_prefix}/sbin logdir = /var/log/freeradius raddbdir = /etc/freeradius radacctdir = ${logdir}/radacct confdir = ${raddbdir} run_dir = ${localstatedir}/run/freeradius db_dir = ${raddbdir} libdir = /usr/lib/freeradius pidfile = ${run_dir}/freeradius.pid max_request_time = 30 cleanup_delay = 5 max_requests = 1024 listen { type = auth ipaddr = <ip_address_> # port = 0 interface = eth0 } listen { type = auth ipaddr = 127.0.0.1 port = 0 interface = lo } listen { type = acct ipaddr = <ip_address_> port = 0 interface = eth0 } listen { type = acct ipaddr = 127.0.0.1 port = 0 interface = lo } # , , #listen { type = auth …} listen {type = acct …} hostname_lookups = no allow_core_dumps = no regular_expressions = yes extended_expressions = yes log { destination = files file = ${logdir}/radius.log syslog_facility = daemon stripped_names = no auth = no auth_badpass = no auth_goodpass = no } checkrad = ${sbindir}/checkrad security { max_attributes = 200 reject_delay = 1 status_server = yes } proxy_requests = no $INCLUDE clients.conf thread pool { start_servers = 5 max_servers = 32 min_spare_servers = 3 max_spare_servers = 10 max_requests_per_server = 0 } modules { $INCLUDE ${confdir}/modules/ } instantiate { exec expr expiration logintime } $INCLUDE policy.conf $INCLUDE sites-enabled/
次に、 / etc / freeradius / clients.confに次のように記述します。
client localhost { ipaddr = 127.0.0.1 netmask = 32 secret = samba4 # «» shortname = localhost }
EAP-TTLSおよびPEAPを必要とする内部トンネルの可能性を削除します。
sudo rm -rf /etc/freeradius/sites-enabled/inner-tunnel
これで、 デフォルトのディレクトリは/ etc / freeradius / sites-enabled /ディレクトリに残り、編集しています:
authorize { preprocess auth_log chap mschap #suffix # , .. ldap expiration logintime pap } authenticate { Auth-Type PAP { pap } Auth-Type CHAP { chap } Auth-Type MS-CHAP { mschap } Auth-Type LDAP { ldap } } preacct { preprocess acct_unique suffix files } accounting { detail radutmp attr_filter.accounting_response } session { radutmp } post-auth { exec Post-Auth-Type REJECT { attr_filter.access_reject } } pre-proxy { } post-proxy { }
/ etc / freeradius / modules /ディレクトリに移動し、必要なモジュールを編集します。
ファイル/ etc / freeradius / modules / ldap (すべてのcnとdcをあなたのものに置き換えます):
ldap { server = "localhost" identity = "cn=VPN,cn=users,dc=example,dc=com" # ldap # password = <__> basedn = "dc=example,dc=com" filter = "(sAMAccountName=%{Stripped-User-Name:-%{User-Name}})" ldap_connections_number = 5 timeout = 4 timelimit = 3 net_timeout = 1 tls { start_tls = no } access_attr = "msNPAllowDialin" dictionary_mapping = ${confdir}/ldap.attrmap edir_account_policy_check = no # WiKi , # Active Directory ! chase-referrals = yes rebind = yes }
/ etc / freeradius / modules / mschapの編集:
mschap { use_mppe = yes ( mppe-128) require_encryption = yes require_strong = yes with_ntdomain_hack = no # - – !!! ntlm_auth = "/usr/local/samba/bin/ntlm_auth3 --request-nt-key \ --username=%{Stripped-User-Name:-%{User-Name:-None}} \ --challenge=%{mschap:Challenge:-00} \ --nt-response=%{mschap:NT-Response:-00}" }
もう一度、ntlm_auth = "/ usr / local / samba / bin / ntlm_auth3 parameter ..."に注目します。Samba4はsamba3と「友達」であり、MS-CHAP v2をサポートしないntlm_authバイナリの他に、これをすべてドラッグするntlm_auth3バイナリがあります「!
PPTPD
そして最後にpptpd。 pptpd自体はすでにインストールおよび設定されていることが理解されています( /etc/pptpd.confファイルを編集する必要はありません!)
/ etc / ppp / pptpd-optionsを編集:
############################################################################### # $Id: pptpd-options 4643 2006-11-06 18:42:43Z rene $ # # Sample Poptop PPP options file /etc/ppp/pptpd-options # Options used by PPP when a connection arrives from a client. # This file is pointed to by /etc/pptpd.conf option keyword. # Changes are effective on the next connection. See "man pppd". # # You are expected to change this file to suit your system. As # packaged, it requires PPP 2.4.2 and the kernel MPPE module. ############################################################################### # Authentication # Name of the local system for authentication purposes # (must match the second field in /etc/ppp/chap-secrets entries) name pptpd # Optional: domain name to use for authentication # # Strip the domain prefix from the username before authentication. # (applies if you use pppd with chapms-strip-domain patch) #chapms-strip-domain # Encryption # Debian: on systems with a kernel built with the package # kernel-patch-mppe >= 2.4.2 and using ppp >= 2.4.2, ... refuse-pap refuse-chap refuse-mschap # Require the peer to authenticate itself using MS-CHAPv2 [Microsoft # Challenge Handshake Authentication Protocol, Version 2] authentication. require-mschap-v2 # Require MPPE 128-bit encryption # (note that MPPE requires the use of MSCHAP-V2 during authentication) require-mppe-128 # Network and Routing # If pppd is acting as a server for Microsoft Windows clients, this # option allows pppd to supply one or two DNS (Domain Name Server) # addresses to the clients. The first instance of this option # specifies the primary DNS address; the second instance (if given) # specifies the secondary DNS address. # Attention! This information may not be taken into account by a Windows # client. See KB311218 in Microsoft's knowledge base for more information. ms-dns <ip_dns> # – 127.0.0.1 # If pppd is acting as a server for Microsoft Windows or "Samba" # clients, this option allows pppd to supply one or two WINS (Windows # Internet Name Services) server addresses to the clients. The first # instance of this option specifies the primary WINS address; the # second instance (if given) specifies the secondary WINS address. ms-wins <ip_wins> # – 127.0.0.1 # Add an entry to this system's ARP [Address Resolution Protocol] # table with the IP address of the peer and the Ethernet address of this # system. This will have the effect of making the peer appear to other # systems to be on the local ethernet. # (you do not need this if your PPTP server is responsible for routing # packets to the clients -- James Cameron) proxyarp # Debian: do not replace the default route nodefaultroute # Logging # Enable connection debugging facilities. # (see your syslog configuration for where pppd sends to) debug # Print out all the option values which have been set. # (often requested by mailing list to verify options) #dump # Miscellaneous # Create a UUCP-style lock file for the pseudo-tty to ensure exclusive # access. lock # Disable BSD-Compress compression nobsdcomp auth logfile /var/log/pptpd.log # radius plugin radius.so plugin radattr.so
ファイル/etc/radiusclien/radiusclient.conf (私の意見では、authserverとacctserverを修正しない限り、私はそれに触れませんでした):
# General settings # specify which authentication comes first respectively which # authentication is used. possible values are: "radius" and "local". # if you specify "radius,local" then the RADIUS server is asked # first then the local one. if only one keyword is specified only # this server is asked. auth_order radius,local # maximum login tries a user has login_tries 4 # timeout for all login tries # if this time is exceeded the user is kicked out login_timeout 60 # name of the nologin file which when it exists disables logins. # it may be extended by the ttyname which will result in # a terminal specific lock (eg /etc/nologin.ttyS2 will disable # logins on /dev/ttyS2) nologin /etc/nologin # name of the issue file. it's only display when no username is passed # on the radlogin command line issue /etc/radiusclient/issue # RADIUS settings # RADIUS server to use for authentication requests. this config # item can appear more then one time. if multiple servers are # defined they are tried in a round robin fashion if one # server is not answering. # optionally you can specify a the port number on which is remote # RADIUS listens separated by a colon from the hostname. if # no port is specified /etc/services is consulted of the radius # service. if this fails also a compiled in default is used. authserver localhost # RADIUS server to use for accouting requests. All that I # said for authserver applies, too. # acctserver localhost # file holding shared secrets used for the communication # between the RADIUS client and server servers /etc/radiusclient/servers # dictionary of allowed attributes and values # just like in the normal RADIUS distributions dictionary /etc/radiusclient/dictionary # program to call for a RADIUS authenticated login login_radius /usr/sbin/login.radius # file which holds sequence number for communication with the # RADIUS server seqfile /var/run/radius.seq # file which specifies mapping between ttyname and NAS-Port attribute mapfile /etc/radiusclient/port-id-map # default authentication realm to append to all usernames if no # realm was explicitly specified by the user # the radiusd directly form Livingston doesnt use any realms, so leave # it blank then default_realm # time to wait for a reply from the RADIUS server radius_timeout 10 # resend request this many times before trying the next server radius_retries 3 # LOCAL settings # program to execute for local login # it must support the -f flag for preauthenticated login login_local /bin/login
ファイル/ etc / radiusclien / server :
# Make sure that this file is mode 600 (readable only to owner)! # #Server Name or Client/Server pair Key #---------------- --------------- 127.0.0.1 samba4 # «», freeradius?
非常に重要なポイント-ファイル/etc/radiusclient/dictionary.microsoftを作成します。 私は彼のテキストを引用しません、なぜなら ここで完全に入手できます )
そして、ファイルの最後に/ etc / radiusclient /辞書の行を追加します
/etc/radiusclient/dictionary.microsoftを含めて、次のものを取得します。
# # Updated 97/06/13 to livingston-radius-2.01 miquels@cistron.nl # # This file contains dictionary translations for parsing # requests and generating responses. All transactions are # composed of Attribute/Value Pairs. The value of each attribute # is specified as one of 4 data types. Valid data types are: # # string - 0-253 octets # ipaddr - 4 octets in network byte order # integer - 32 bit value in big endian order (high byte first) # date - 32 bit value in big endian order - seconds since # 00:00:00 GMT, Jan. 1, 1970 # # Enumerated values are stored in the user file with dictionary # VALUE translations for easy administration. # # Example: # # ATTRIBUTE VALUE # --------------- ----- # Framed-Protocol = PPP # 7 = 1 (integer encoding) # # # Following are the proper new names. Use these. # # # !!!! !!!!! INCLUDE /etc/radiusclient/dictionary.microsoft
すべてがそうです。 Samba4はすでに実行中です。freeradiusサーバーとpptpdデーモンを再起動する必要があります。
ADUCスナップインに[ダイヤルイン]タブがないという問題を解決する
そうそう。 特定のユーザーのVPNアクセスを有効/無効にする方法について。 Windowsリモート管理ツールパッケージをインストールしましたか? そのため、Windows 7の[ダイヤルイン]タブでWiKiページに表示されるADUCスナップインの画像は表示されません。 そして、次のようなものが表示されます:

そして、ダイヤルインタブまたはそのロシアの対応する着信コールはどこにありますか? ここでユーザー権限を管理する方法は? 心配する必要はありません。 私たちは困難を恐れていませんか? ドメインコントローラーは、とりわけLDAPサーバーであるため、このようなサーバーを管理するためのツール(たとえば、 LdapAdmin )を配置し、それを駆動します。
まず、samba4サーバーへの接続を構成します。サーバーアドレスを登録し、[フェッチDN]ボタンをクリックし、最上位レベルのベースであるラジオボックス[GSS-API]を選択します。ユーザー–管理者として、このユーザーのパスワードを接続します。 ドメインの展開中に積み重ねられたカタログ全体が表示されます。 必要なユーザーを選択し、編集モードに入ります。 msNPAllowDialin属性を見つけて、TRUEまたはFALSEを入力します(必須-大文字で!):
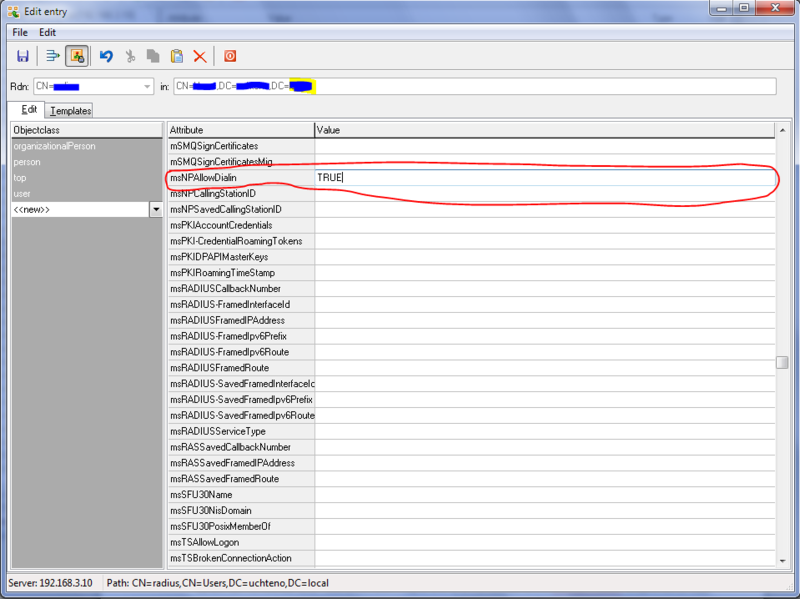
保存します。 このユーザーは、VPN経由でのログインを許可(または禁止)されます。
まとめ
私の意見では、投稿の最初に設定されたすべてのタスクは解決されました。 ソリューションに費やした時間(約2週間半)は、主にインターネット上のドキュメントの調査、そのようなソリューションの経験、受け取った情報とサーバーで自分の目で見た現実との比較、samba4のコンパイルと再コンパイル、および編集、編集と構成の編集を繰り返します...しかし、結果は私を満足させました。結果は、Windows Server 2008 R2をActive Directory、ネットワークポリシーとアクセスサービス、リモートデスクトップサービスにほぼ完全に置き換えたものです OVAは書いていない)。