Vulnerability is at the heart of the Mimblewimble protocol, and I don't think it can be fixed. Therefore, in terms of protecting privacy, Mimblewimble can no longer be considered a viable alternative to Zcash or Monero.
In the past two years, Mimblewimble has become popular as a compact protocol for private cryptocurrencies (“privacy coins”). Mimblewimble was coined in 2016 by a hacker under the pseudonym Tom Elvis Jedusor. He sent the protocol description to IRC chat and disappeared. Since then, the most famous implementations of Mimblewimble are Grin crypto-private cryptocurrency created by anonymous developers, as well as Tari and BEAM projects that have attracted venture investments. Even Litecoin is considering Mimblewimble integration .

Several researchers have already hypothesized the potential weaknesses of the privacy mechanism in Mimblewimble. The contribution of my work is that I demonstrate a specific attack method, prove its viability on real cryptocurrency and measure its effectiveness. By running the Grin experiment, I was able to successfully deanonymize 96% of the transactions I reviewed. So now it’s obvious that you can’t rely on Mimblewimble if you need high privacy.
In my github you will find a detailed description of the attack, sources for playing it, collected data and technical FAQ. Further in this article is a general, intuitive explanation of connectivity, how the attack works and what it means for privacy technologies.
What is connectivity?
It is important to understand what this attack means and what it does not mean.
This attack does not allow us to determine the amount that people receive. Mimblewimble successfully hides the amount of transfers using cryptography based on vanilla elliptic curves ( Pedersen obligations scheme ). What this attack allows us to do is determine who paid whom . In other words, it allows us to connect transactions with each other and determine the direction of transfers.
Why is it important?
Let's say Coinbase knows that a specific address belongs to a Venezuelan named Daniel. You, an American user, are trying to withdraw coins with Coinbase. But after expanding the transaction graph, Coinbase determines that you received money from Daniel - even though they don’t know exactly how much. Due to restrictions imposed on Venezuela by the US Foreign Assets Control Authority, Coinbase closes your account. (Of course, exchanges will know a lot about the transaction graph, because they have KYC user data that is displayed in fiat).
Or imagine that some authoritarian government knows that a certain address belongs to a political dissident. You send this dissident a small donut. Later, when you send your Mimblewimble transfer to a local exchange, that exchange transfers your transaction data to the government. Since the government sees the entire graph of the transaction, it now knows that you supported the political dissident.
Such attacks would not be possible in Zcash. Because transactions in Zcash are not connected, or, in other words, every Zcash transaction has a large set of anonymity . An anonymity set is a set of transactions from which your transaction cannot be distinguished. Imagine this as mixing with the crowd: the larger the set of anonymity, the more “crowd” your transaction is mixed.
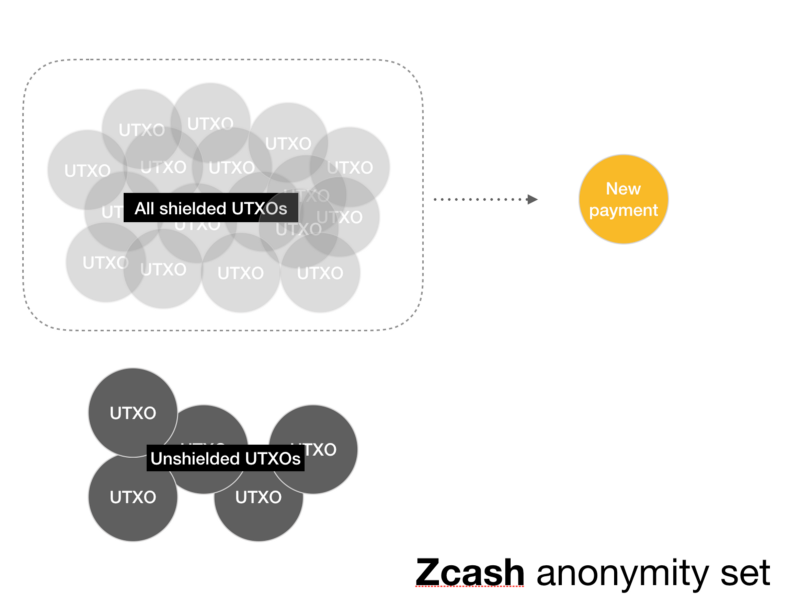
In Zcash, the set of anonymity of each transaction includes all protected coins. This is the maximum possible anonymity from a theoretical information point of view.
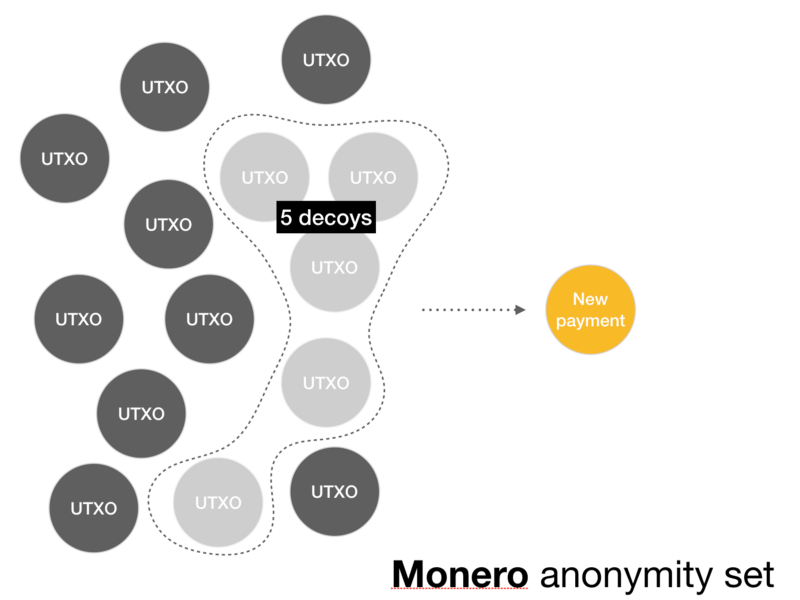
In Monero, the set of anonymity of each transaction is the set of all user-enabled bait transactions. Although the Monero client allows you to set the number of lures in a set, the current default value is 11. (Monero has its own difficulties in choosing lures safely , but I think for the most part it works, plus or minus ).
It was originally supposed that the Mimblewimble anonymity set consists of all transactions in the same block, that is, it looks like this:
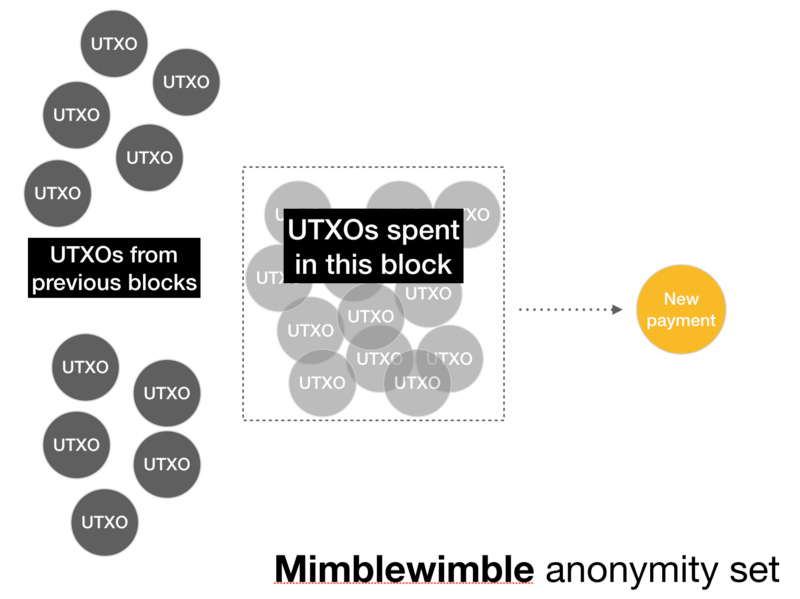
But actually it looks like this:
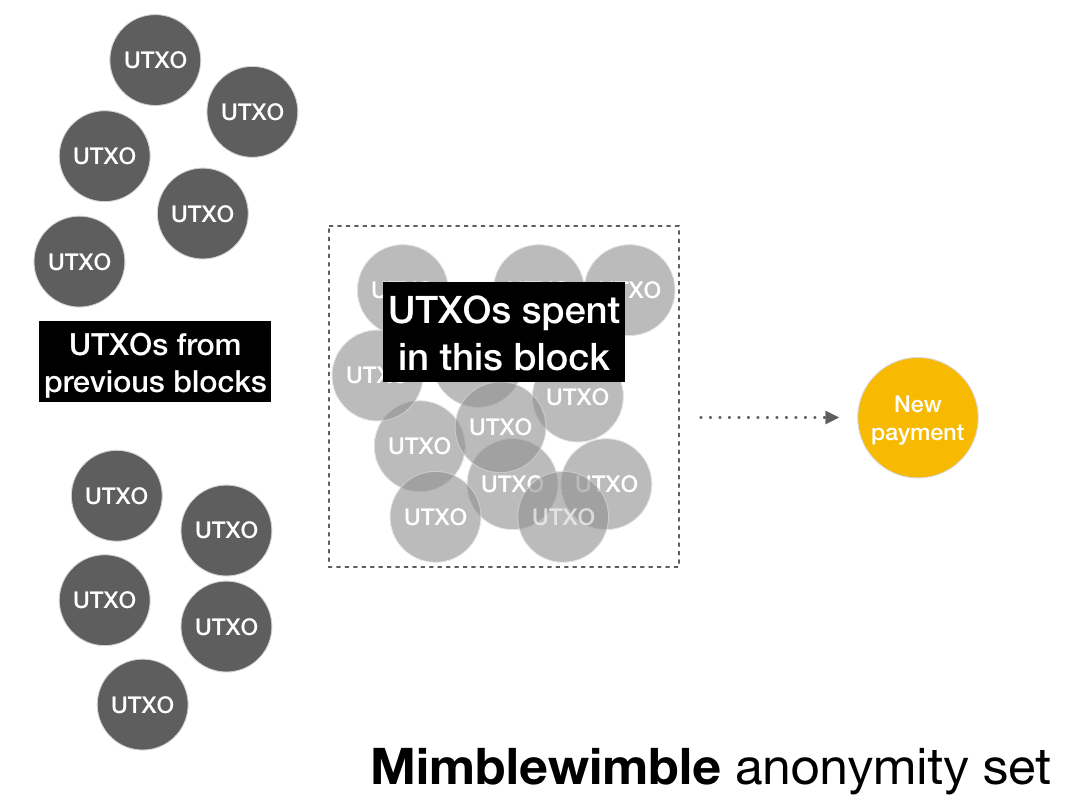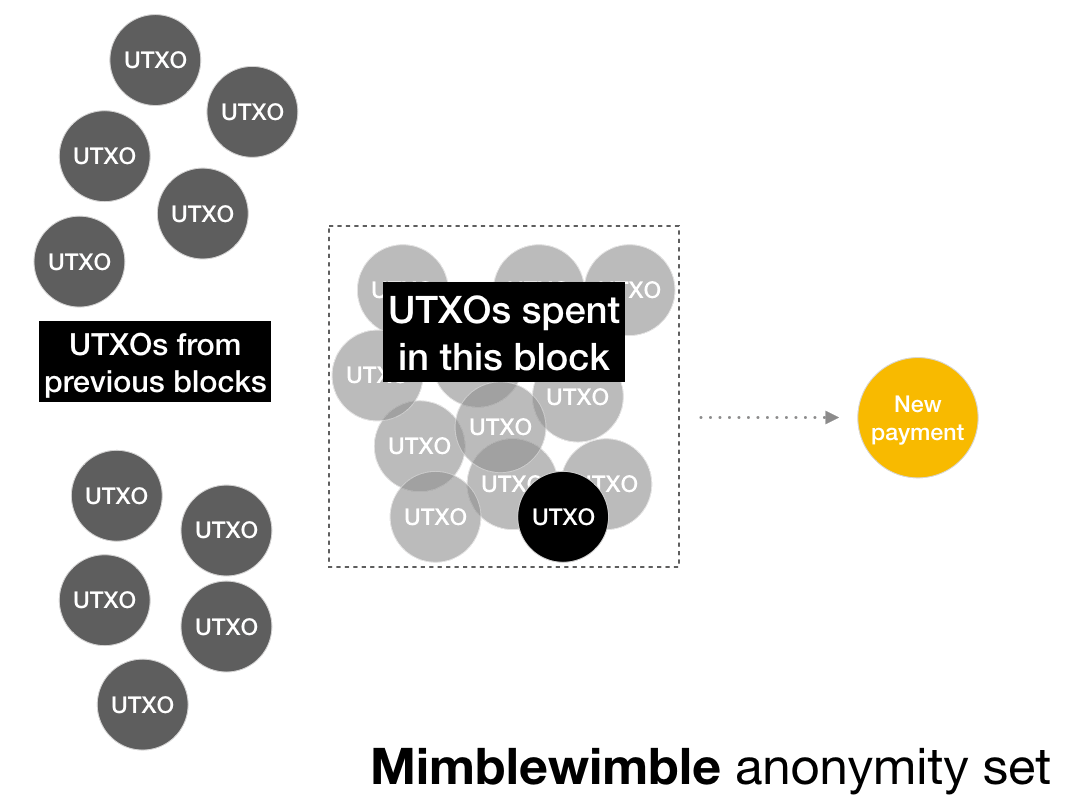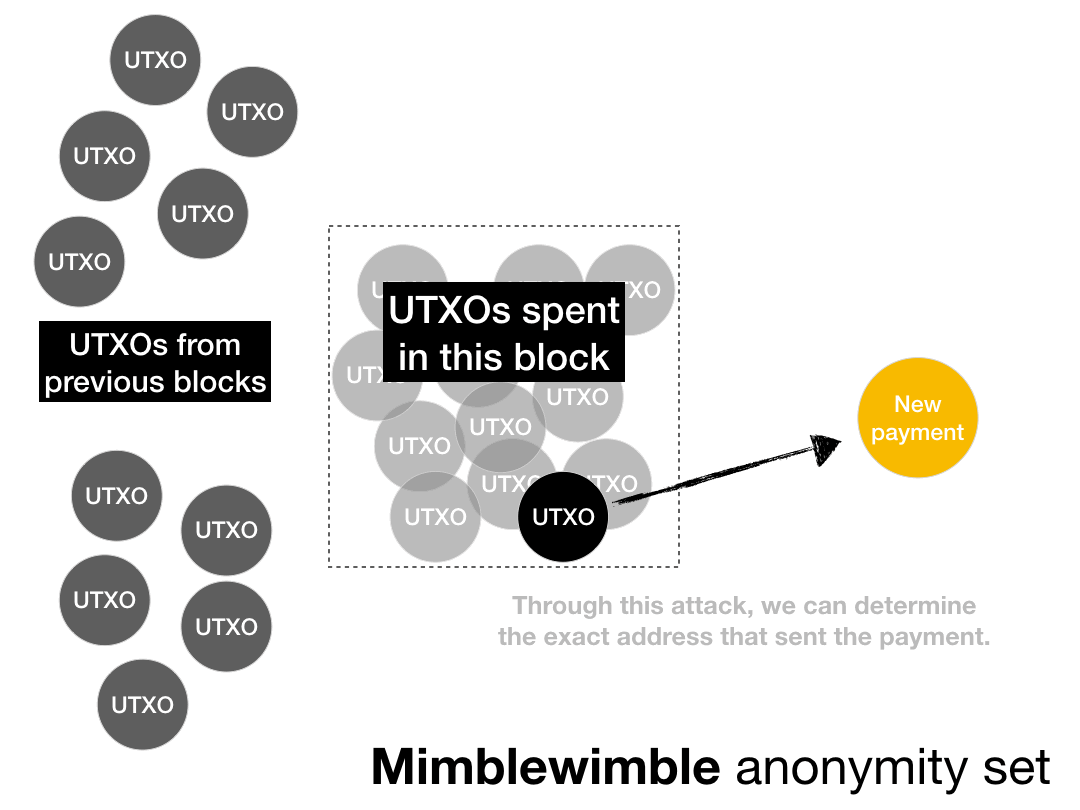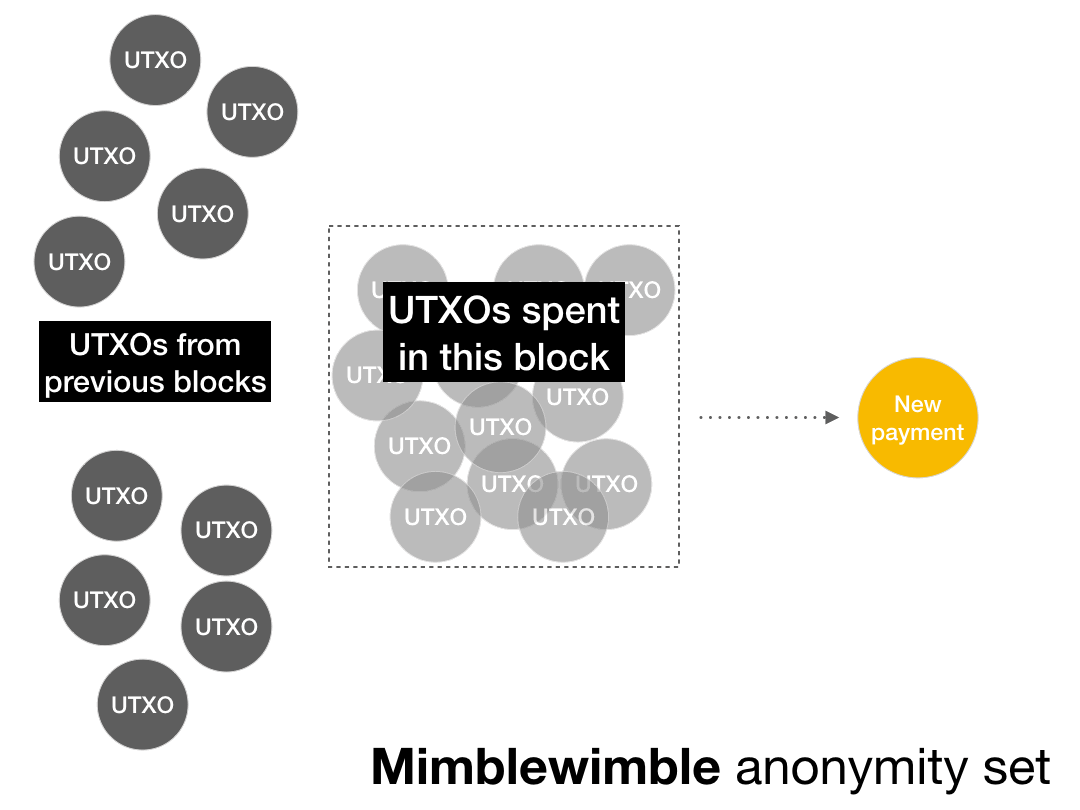
This reduces the Mimblewimble anonymity set to a single address.
I want to say that this is not criticism of Grin in general! I really respect the Grin community and core developers, who have always readily answered my questions on the forums.
Grin still provides higher privacy than Bitcoin and other private coins, as it encrypts amounts securely. But the Mimblewimble privacy model is strictly weaker than that of Zcash or Monero. And this makes it insufficient for many real-world use cases where privacy is needed.
Attack Overview
How exactly can you deanonymize a transaction graph in Mimblewimble?
I noted that, despite the encryption of the transfer amounts, Mimblewimble leaves a traceable transaction graph. But the developers of the protocol knew about this, and therefore Mimblewimble uses two main ways to combat connectivity: through aggregation of the whole block and “dandelion” (Dandelion) .
The idea of end-to-end aggregation is that when transactions are collected in a block, they are aggregated into one “super-transaction”. This “super transaction ” is like a giant CoinJoin - all the inputs and outputs are mixed together, and there is no easy way to determine which one paid to whom. There are just a bunch of inputs and a bunch of outputs, and specific amounts are hidden.
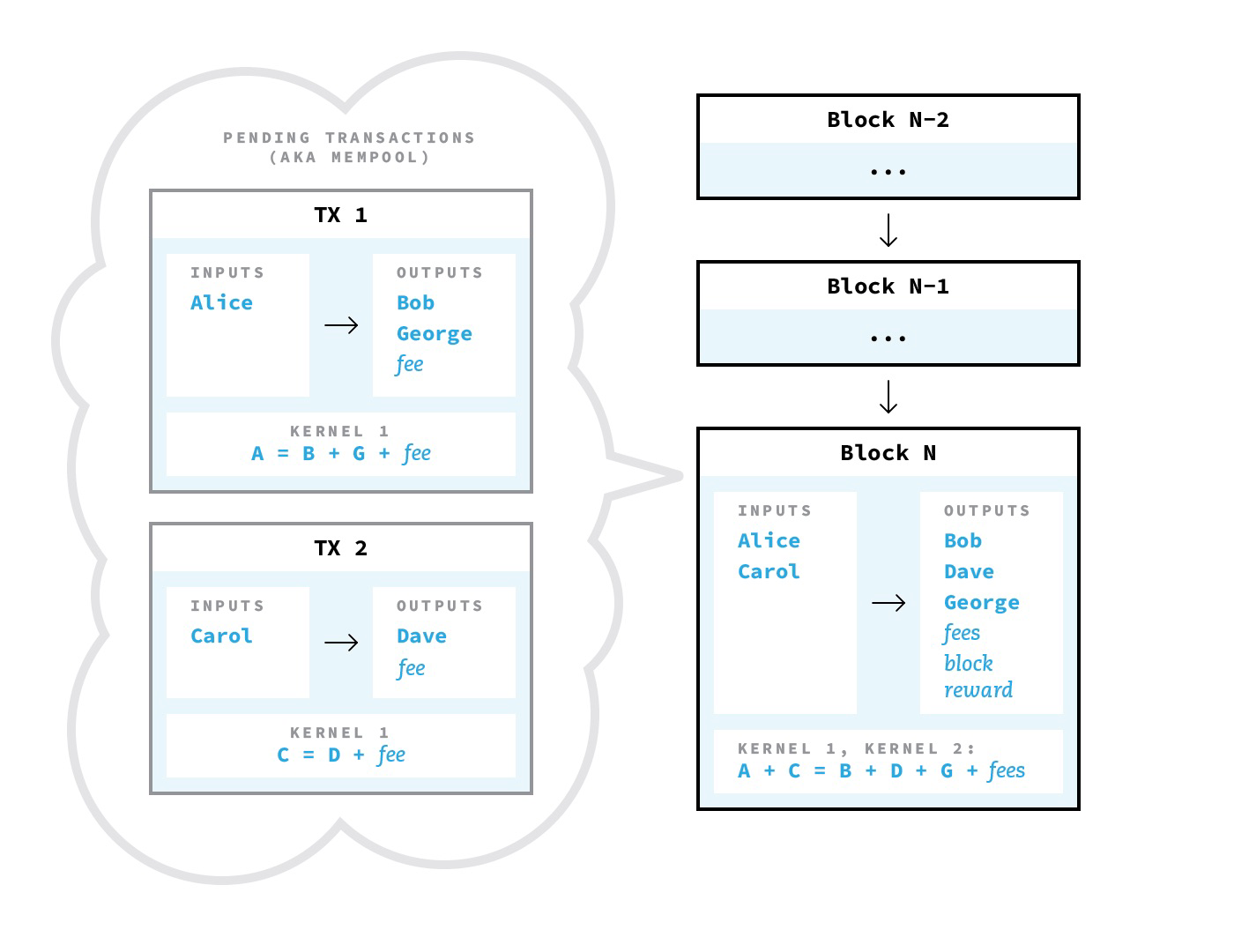
Sounds reliable? There is only one problem: this CoinJoin is built one transaction at a time. Since transactions are constantly being created and sent from different places, if you hold a sniffer node that collects all transactions before end-to-end aggregation is completed, it is very easy to untangle CoinJoin. Any sniffer node can simply monitor the network and remember the original transactions before they are aggregated. This is easy enough if you simply archive all the messages that you see on a P2P network.
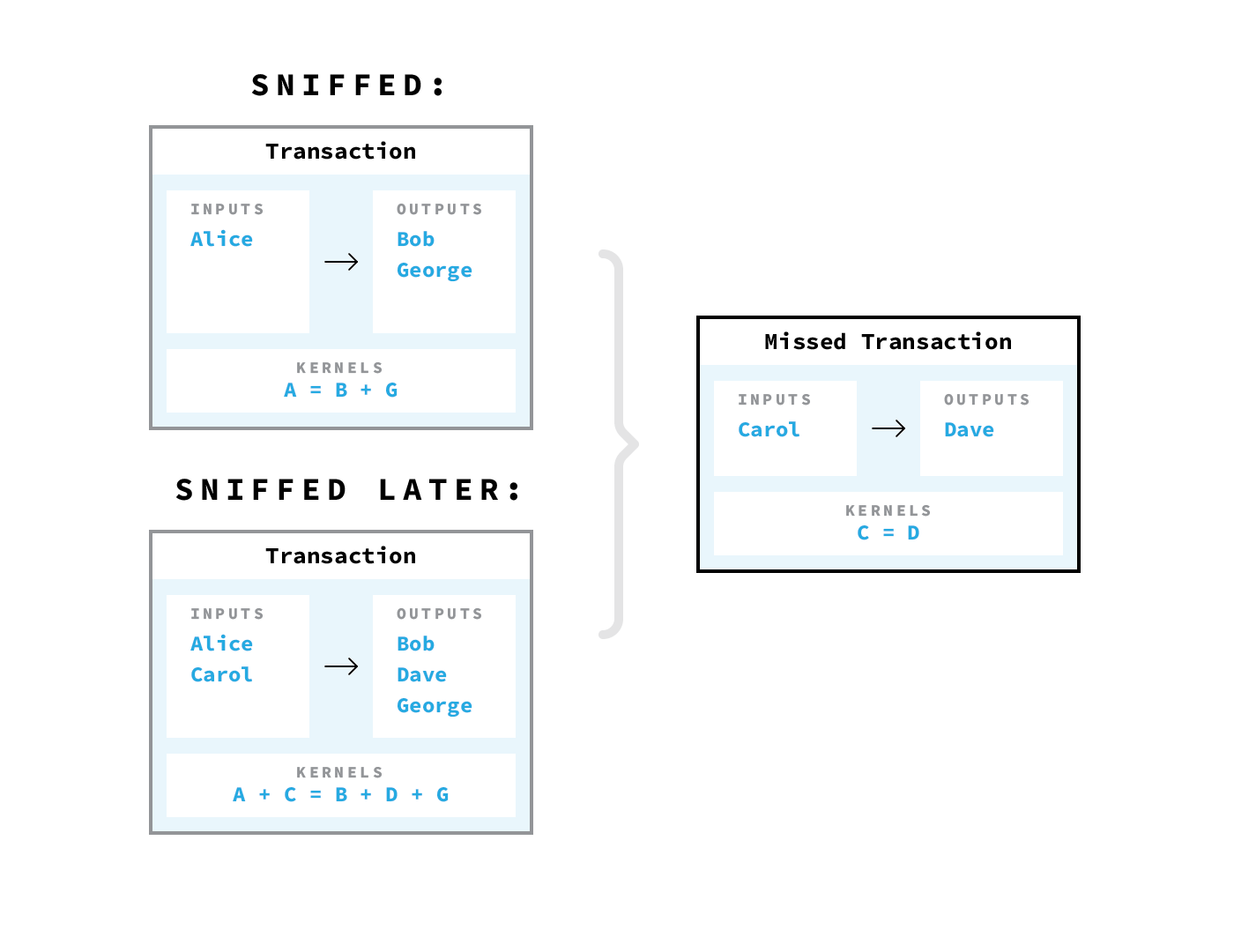
Here you may be surprised - and is that all?
In fact, there is another layer of protection created by the Grin team: the Dandelion protocol (dandelion) . Dandelion is a networking method developed by researchers at Carnegie Mellon University, which should hide the IP of the creator of the transaction.

Usually in cryptocurrencies such as bitcoin, the creator of the transaction simply sends the transaction to all its peers, and it quickly passes through the P2P network. But in the Dandelion protocol, the distribution of each transaction begins with the secret game of a broken phone. The creator transfers his transaction to only one feast, which, in turn, transfers it to another feast, and so on along the chain (dandelion “trunk”). After a random number of such moves, the last feast sends out the transaction, just like in bitcoin (dandelion “flower”). But this feast is so far from the creator of the transaction that no observer can say who started the chain.
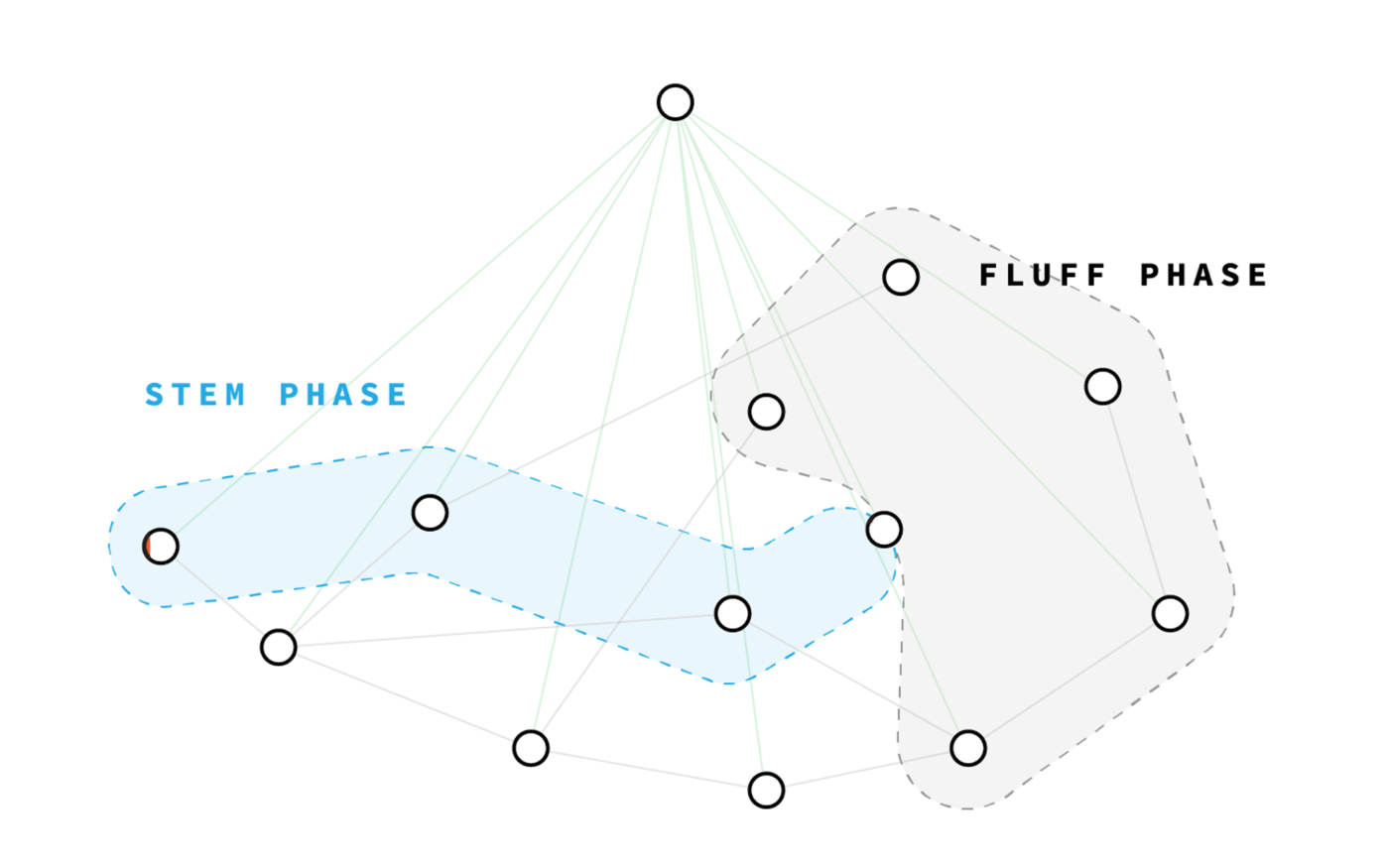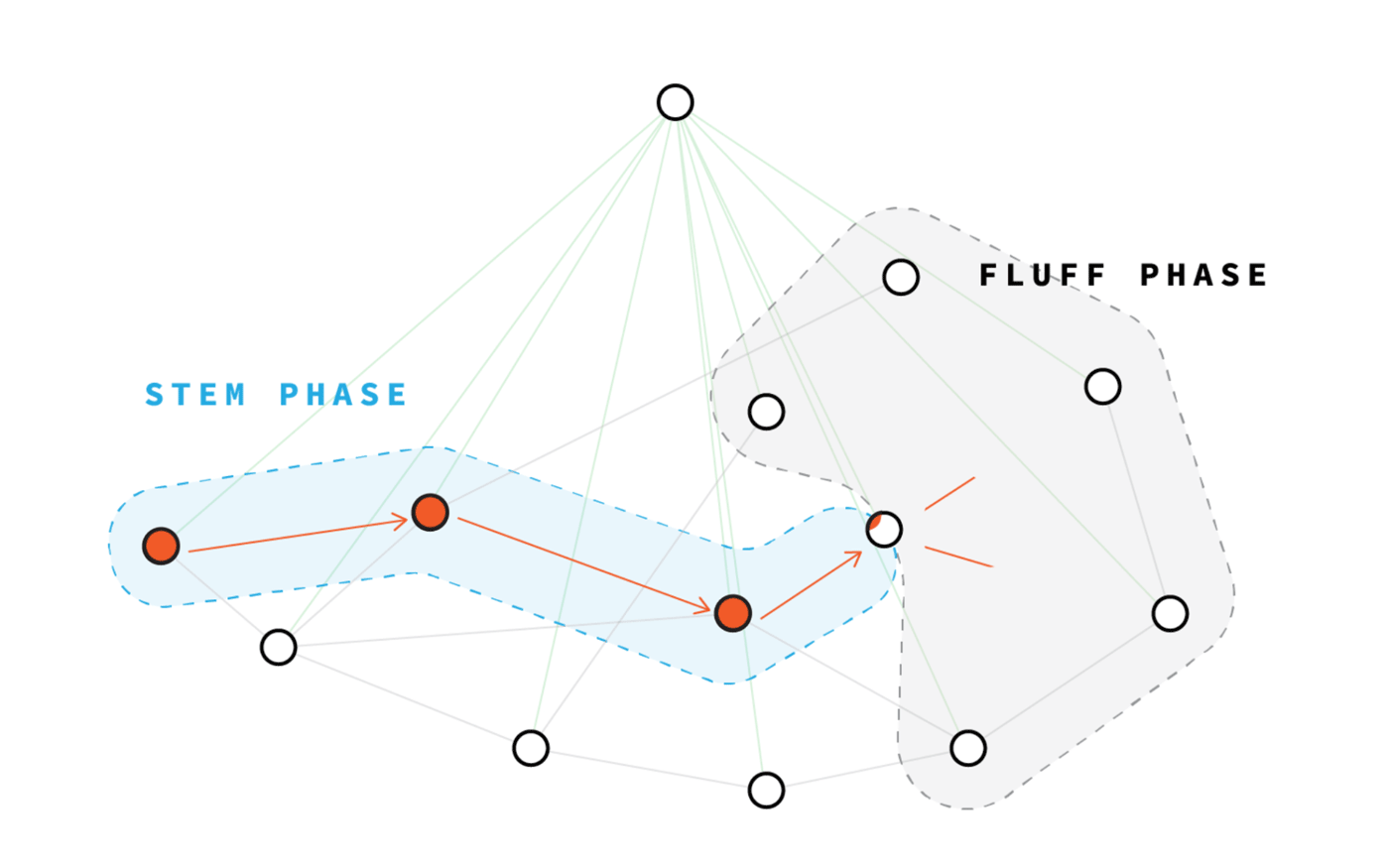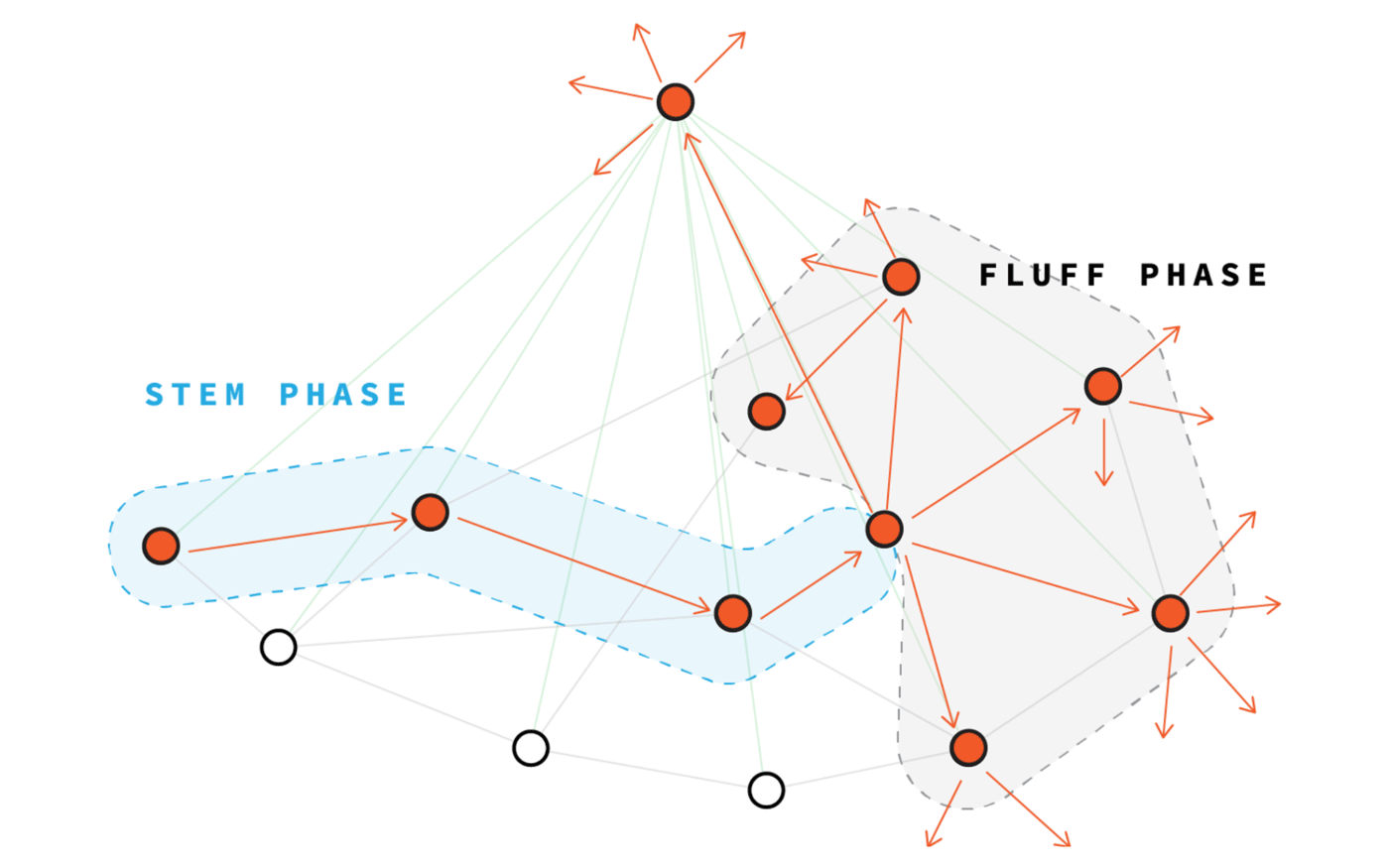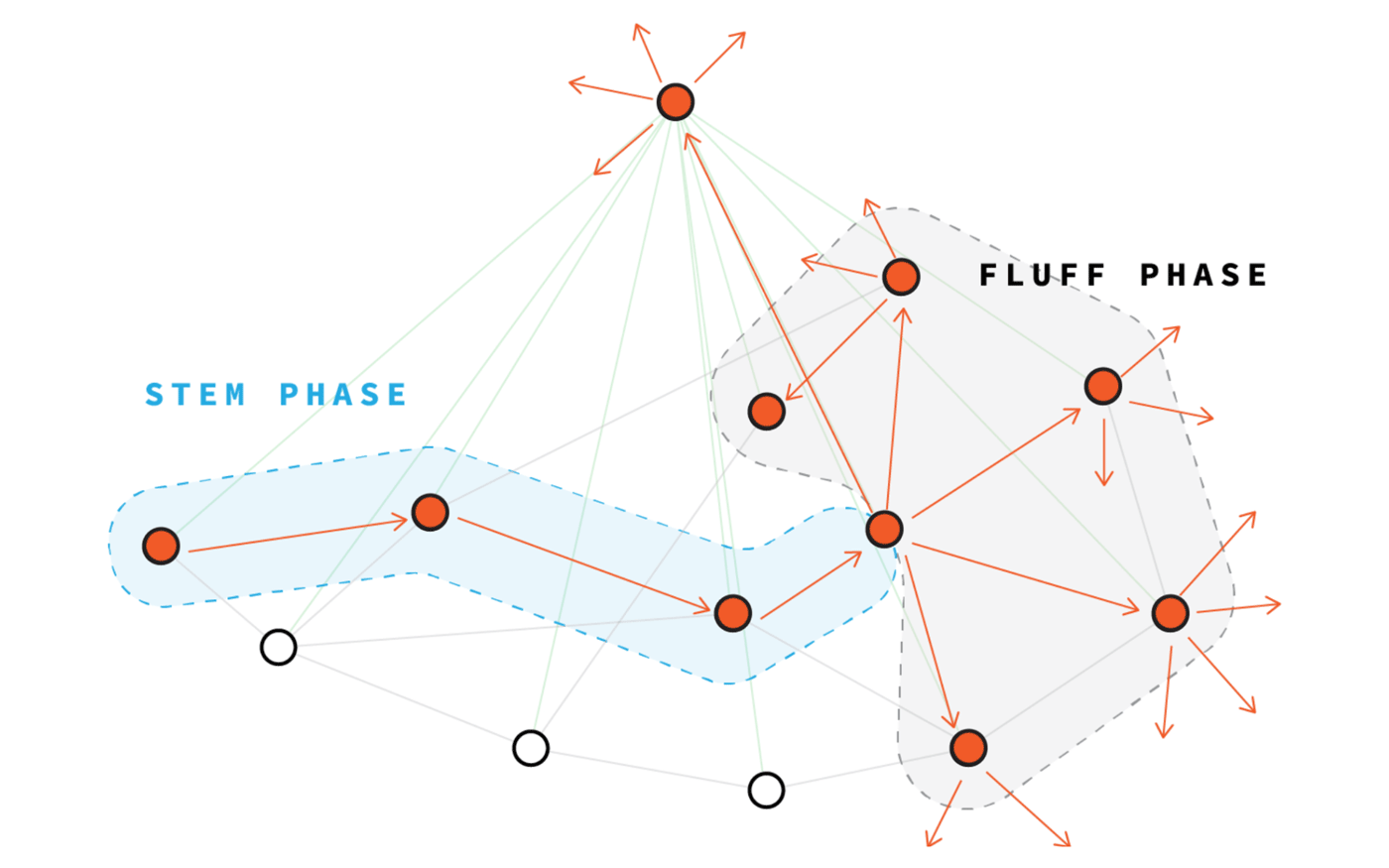
This works great to hide the IP of the person who is committing the transaction. But Dandelion in Grin has a second function: in rare cases, it allows you to maintain the anonymity of the transaction even if there is a sniffer node in the network. Since each transaction begins in the Dandelion “stem” phase, when two transactions intersect in the “stem” propagation phase, they will be aggregated early. If this happens, then by the time the transaction is sent out and becomes visible to everyone, the sniffer node cannot paste the transactions: they are already stuck together in CoinJoin.
This transaction sending mechanism is Grin's primary defense against transactional connectivity by sniffer nodes. But there is an easy way to break her.
By default, each Grin node is connected to 8 other peer nodes. But, increasing the number of peers, I can connect my sniffer node to each network node. If my site has been online continuously for a long time, in the end, almost all the nodes in the network will connect to me, making me a super hub .
When I become a superknot, there is a high probability that I will be in the chain of "dandelion" of each transaction. Thus, the only reason I may not be able to catch a transaction before its aggregation is if the two transactions crossed in the stem phase of the dandelion before I saw at least one of them . If I see at least one of them before they are aggregated, I can separate them with a simple subtraction of the sets.
In my attack, I was able to connect 96% of all transactions, connecting only to 200 peers from the total 3000 peers in the Grin network. But if I were willing to spend a little more money, I could easily connect to 3,000 nodes to stick out almost all transactions. And for this it is not necessary to keep one large supernode - the same attack will work if you run 3,000 separate nodes with unique IPs, each of which will be connected to only one peer. As long as I intercept all the transaction data and dump it into the central master database, the attack will work in exactly the same way.
So is it possible to save Mimblewimble?
Dont clear. In my opinion, in the current version of Grin, there is no way to protect the transaction graph. Just lengthening the “dandelion” is not enough - it will be easy to defeat with a large number of nodes, as I describe in the technical report .
But despite transactional connectivity, Mimblewimble still has properties that set the protocol apart from other cryptocurrencies. Through it, end-to-end aggregation is possible, which is an effective way to reduce the blockchain size, and it effectively hides transaction amounts. If you want high privacy, you can always combine Mimblewimble with another protocol that hides the transaction graph, for example, as in Ethereum 9¾ (which combines Mimblewimble with a Zerocash-style zero-reset scheme).
But it is obvious that Mimblewimble itself is not strong enough to provide high privacy.
Bitcoin is now 11 years old, but cryptocurrencies are still at a very early stage of development. Not so long ago, serious vulnerabilities were discovered in both Zcash and Monero . And this is to be expected: most interesting technologies are still in the research phase.
But this is how science always develops: we constantly put forward new hypotheses and refute them until only those that have passed the test of time remain.
Thanks to Hasib Kireshi for the substantial help in compiling this report and illustrating the sets of anonymity. Additional thanks to Oleg Ostroumov, Elena Nadolinsky, Mohamed Fouda, Lucas Ryan and Nader Al-Naji for reviewing drafts of this post. And many thanks to Jake Stutzman (NEAR Protocol) for Dandelion illustrations and block aggregation. Thank you Daria Smirnova for translating the article.
If you liked the article, I recommend subscribing to my Twitter , where they go first (in English).
Disclosure: Dragonfly Capital is committed to not trading the assets listed in this report for 3 days from the date of publication.