I have such an outbreak of events is outrageous, because this method is unsafe. Reassign the number from one SIM card to another began at the beginning of the mobile era - this is how the number is restored when the SIM card is lost. “Digital Money Weaning Specialists” realized: the option “overwrite SIM cards” can be used in fraudulent schemes. After all, the one who controls the SIM card can manage other people's online banking, and electronic wallets, and even cryptocurrency. And you can take over another person’s number by bribing a telecom employee using fraud or fake documents.

Thousands of SIM swap episodes have been revealed - this is what this fraud scheme has been called. The scale of the disaster suggests that the world will soon abandon the 2FA via SMS. But this does not happen - the study says that it is not the users who choose the 2FA method, but the service owners.
We suggest using the secure 2FA method with the delivery of one-time codes via the blockchain, and we will tell you how to connect it to the service owner.
The bill goes to millions
In 2019, SIM swap fraud increased by 63% according to the London police, and the “average check” of the attacker was 4,000 GBP. I did not find statistics in Russia, but I assume that it is even worse.
SIM swapping is used to steal popular Twitter, Instagram, Facebook, VK accounts, bank accounts, and recently got to cryptocurrencies, the Times newspaper reports from bitcoin entrepreneur Joby Weeks. High-profile cases of theft of cryptocurrencies using SIM swap have been appearing in the press since 2016; on 2019 came a real peak.
In May, US prosecutors in the eastern district of Michigan indicted nine young people between the ages of 19 and 26: they were allegedly part of a hacker gang called “The Community”. The gang is charged with seven swap attacks, as a result of which hackers appropriated cryptocurrency worth more than $ 2.4 million. And in April, a student from California, Joel Ortiz, received 10 years in prison for SIM swapping; $ 7.5 million in cryptocurrencies became its prey.

Photo by Joel Ortiz at a university press conference. Two years later, he will be detained for cyber fraud.
How SIM Swap Works
Swap means exchange. In all such schemes, criminals assign a victim’s phone number, usually through re-issuing a SIM card, and use it to reset a password. A typical SIM swap in theory looks like this:
- Intelligence service. Fraudsters find out the victim’s personal data: name and phone. They can be found in open sources (social networks, friends) or obtained from an accomplice - an employee of a mobile operator.
- Blocking. Victim’s SIM card is deactivated; To do this, just call the technical support of the provider, report the number and say that the phone has been lost.
- Capture, transfer numbers to your SIM card. Usually this is also done through an accomplice in a telecom company or by forging documents.
In real life it is still more severe. Attackers select a victim, and then daily monitor the location of the phone - one request for information that the subscriber has switched to roaming costs 1-2 cents. As soon as the owner of the SIM card has gone abroad, they agree with the manager in the communication salon to issue a new SIM card. It costs about $ 50 (I found information - in different countries and from different operators from $ 20 to $ 100), while the manager will be fired in the worst case - there is no responsibility for this.
Now all intruders will receive all SMS, and the owner of the phone will not be able to do anything about it - he is abroad. And then the villains get access to all the accounts of the victim and, if desired, change passwords.
Chances to return stolen goods
Banks sometimes go towards the victims and withdraw transfers from their accounts. Therefore, it is possible to return fiat money, even if the offender is not found. But with cryptocurrency wallets, everything is more complicated - both technically and legally. So far, no exchange / wallet has paid compensation to swap victims.
If the victims want to defend their money in court, then they accuse the operator: he created the conditions for the theft of money from the account. This is exactly what Michael Turpin did , who lost $ 224 million due to swap. Now he is suing AT&T telecommunications company.

So far, no state has working schemes to legally protect cryptocurrency owners. It is impossible to insure your capital or receive compensation for its loss. Therefore, it is easier to prevent a swap attack than to deal with its consequences. The most obvious way is to use a more reliable “second factor” for 2FA.
SIM swap is not the only 2FA problem via SMS
Confirmation codes in SMS are also unsafe from a technical point of view. Messages can be intercepted due to fatal vulnerabilities in Signaling System 7 (SS7). 2FA by SMS is officially recognized as unsafe (the US National Institute of Standards and Technology speaks about this in its Digital Authentication Guide ).
Moreover, the presence of 2FA often inspires the user with a sense of false security, and he chooses a simpler password. Therefore, such authentication does not complicate, but facilitates the access of an attacker to the account.
And often SMSs come with a long delay or do not come at all.
Other 2FA methods
Of course, on smartphones and SMS, the light did not converge. There are other 2FA methods. For example, one-time TAN codes: the method is primitive, but working - it is still used in some banks. There are systems using biometric data: fingerprints, retinal scans. Another option that seems like a reasonable compromise in terms of convenience, reliability and price is special applications for 2FA: RSA Token, Google Authenticator. And there are physical keys and other methods.
In theory, everything looks logical and reliable. But in practice, modern 2FA solutions have problems, and because of them, reality is different from expectations.
According to the study , the use of 2FA is an inconvenience in principle, and the popularity of 2FA via SMS is explained by “less inconvenience compared to other methods” - receiving one-time codes is understandable for the user.
Many 2FA methods users associate with the fear that access will be lost. A physical key or a list of TAN passwords can be lost or stolen. I personally have a negative experience using Google Authenticator. My first smartphone with this application broke - evaluate my efforts to restore access to accounts. Another problem is the transition to a new device. Google Authenticator is not able to export due to security concerns (if keys can be exported, what kind of security is there?) Once I transferred the keys manually, and then decided that it was easier to leave the old smartphone in a box on a shelf.
The 2FA method should be:
- Safe - only you should gain access to your account, not attackers
- Reliable - you get access to your account whenever you need it
- Convenient and affordable - using 2FA is clear and takes a minimum of time
- Cheap
We believe that blockchain is the right solution.
Use 2FA on the blockchain
For a user, 2FA on the blockchain looks the same as receiving one-time codes via SMS. The only difference is in the delivery channel. The way to get a 2FA code depends on what the blockchain offers. In our project (the information is in my profile) this is a Web application, Tor, iOS, Android, Linux, Windows, MacOS.
The service generates a one-time code and sends it to the messenger on the blockchain. Further, according to the classics: the user enters the received code in the service interface and logs in.
In the article How a decentralized messenger works on the blockchain, I wrote that the blockchain ensures the security and privacy of messaging. Regarding the issue of sending 2FA codes, I will highlight:
- One click to create an account - no phones or emails.
- All messages with 2FA codes are encrypted End-to-End curve25519xsalsa20poly1305.
- MITM attack is excluded - each message with a 2FA code is a transaction on the blockchain and is signed by Ed25519 EdDSA.
- A message with a 2FA code falls into its block. The sequence and timestamp of blocks cannot be fixed, and therefore the order of messages.
- There is no central structure that does checks for the “authenticity” of a message. This is done by a consensus-based distributed node system, and it belongs to users.
- Inability to disable - accounts cannot be blocked, and messages can be deleted.
- Access 2FA codes from any device at any time.
- Delivery confirmation message with 2FA code. A service sending a one-time password knows for sure that it has been delivered. No “Submit Again” buttons.
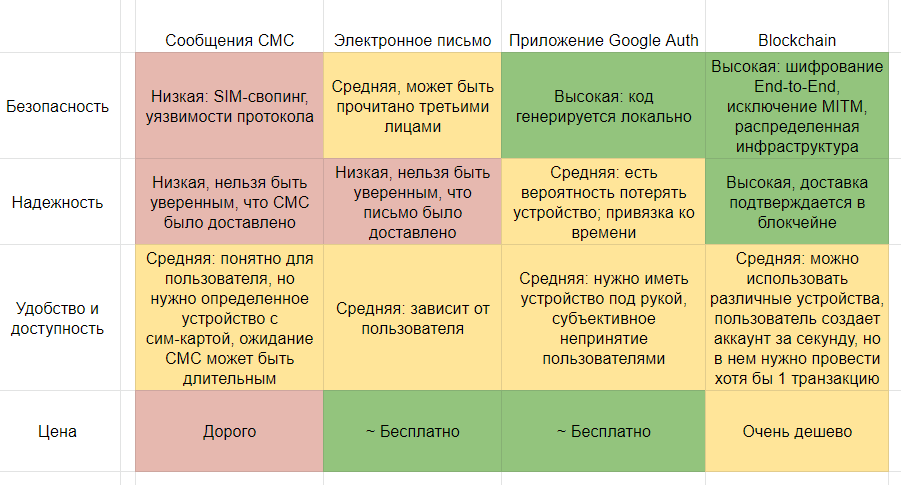
For comparison with some other 2FA methods, I have compiled a table:
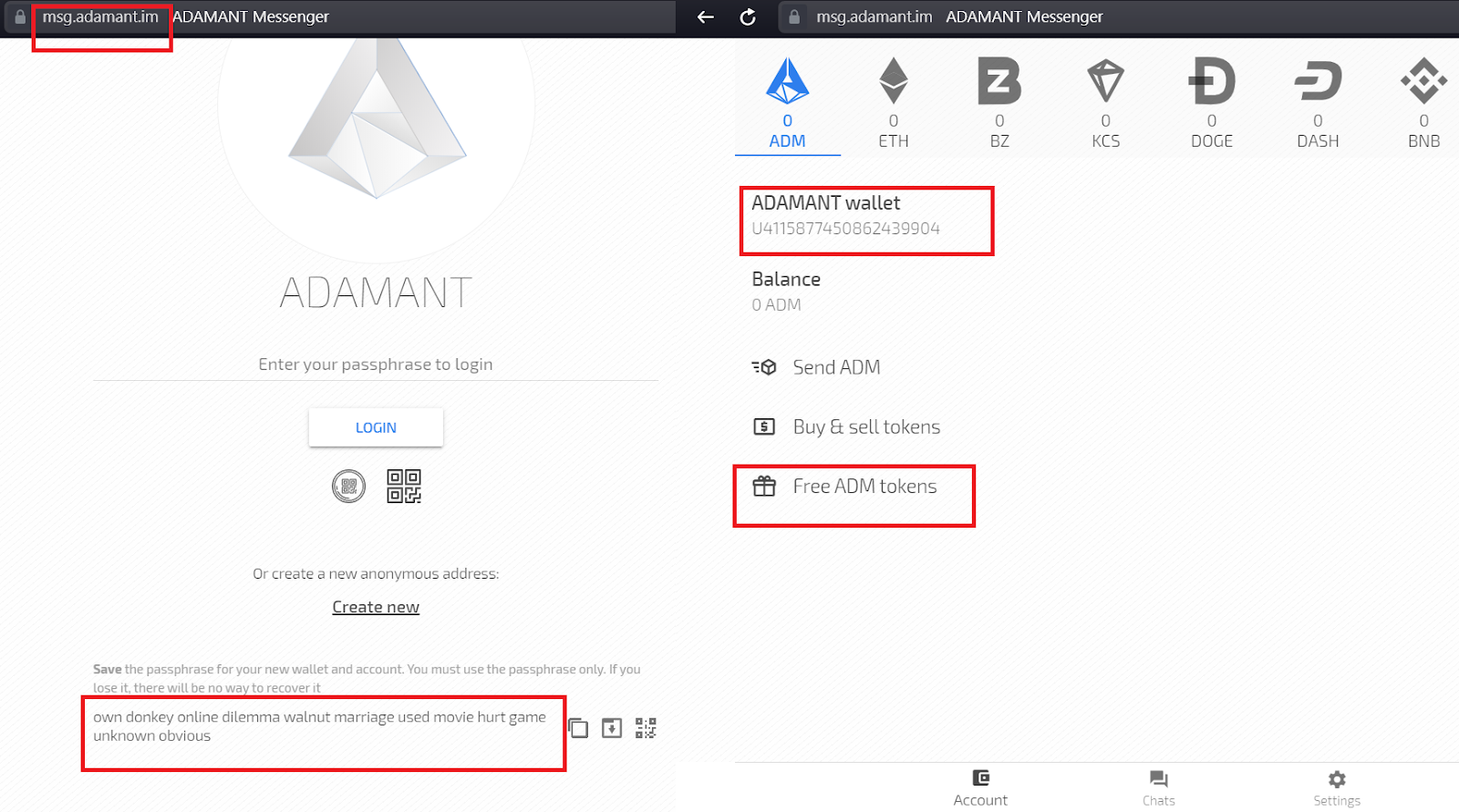
The user receives an account in the blockchain messenger to receive codes in a second - only passphrase is used to enter. Therefore, the methods of application can be different: you can use one account to get codes for all services, or you can create a separate account for each service.
There is also a disadvantage - an account must have at least one transaction. In order for the user to receive an encrypted message with a code, you need to know his public key, and he appears in the blockchain only with the first transaction. We got out this way: they gave us the opportunity to get free tokens in our wallet. However, a more correct solution is to name the account a public key. (For comparison, our account number U1467838112172792705 is a derivative of the public key cc1ca549413b942029c4742a6e6ed69767c325f8d989f7e4b71ad82a164c2ada . For the messenger, this is more convenient and readable, but for a sending system 2FA-codes -) I think in the future someone will make such a decision and transfer “Convenience and Accessibility” to the green zone.
The cost of sending a 2FA code is really low - 0.001 ADM, now it is 0.00001 USD. Again, you can raise your blockchain and make the price zero.
How to connect 2FA on the blockchain to your service
I hope I was able to interest a few readers to add blockchain authorization to their services.
I’ll tell you how to do this using our messenger as an example, and by analogy you can use another blockchain. In the 2FA demo application, we use postgresql10 to store account information.
Connection Stages:
- Create an account on the blockchain from which you will send 2FA codes. You will receive a passfrase, which is used as a private key for encrypting messages with codes and for signing transactions.
- Add a script to your server to generate 2FA codes. If you already use some other 2FA method with one-time password delivery, this step has already been completed.
- Add a script to your server to send codes to the user in the blockchain messenger.
- Create a user interface for sending and entering 2FA code. If you already use some other 2FA method with one-time password delivery, this step has already been completed.
1 Create an account
Creating an account in the blockchain is the generation of a private key, a public key, and an account address derived from it.

First, the passphrase BIP39 is generated, from which the SHA-256 hash is considered. The hash is used to generate the ks private key and kp public key. From the public key with the same SHA-256 with inversion, we get the address in the blockchain.
If you want to send 2FA codes every time from a new account, the code for creating an account will need to be added to the server:
import Mnemonic from 'bitcore-mnemonic' this.passphrase = new Mnemonic(Mnemonic.Words.ENGLISH).toString() … import * as bip39 from 'bip39' import crypto from 'crypto' adamant.createPassphraseHash = function (passphrase) { const seedHex = bip39.mnemonicToSeedSync(passphrase).toString('hex') return crypto.createHash('sha256').update(seedHex, 'hex').digest() } … import sodium from 'sodium-browserify-tweetnacl' adamant.makeKeypair = function (hash) { var keypair = sodium.crypto_sign_seed_keypair(hash) return { publicKey: keypair.publicKey, privateKey: keypair.secretKey } } … import crypto from 'crypto' adamant.getAddressFromPublicKey = function (publicKey) { const publicKeyHash = crypto.createHash('sha256').update(publicKey, 'hex').digest() const temp = Buffer.alloc(8) for (var i = 0; i < 8; i++) { temp[i] = publicKeyHash[7 - i] } return 'U' + bignum.fromBuffer(temp).toString() }
In the demo application, we simplified it - created one account in the web application, and send the codes from it. In most cases, this is more convenient for the user: he knows that the service sends 2FA codes from a specific account, and can name it.
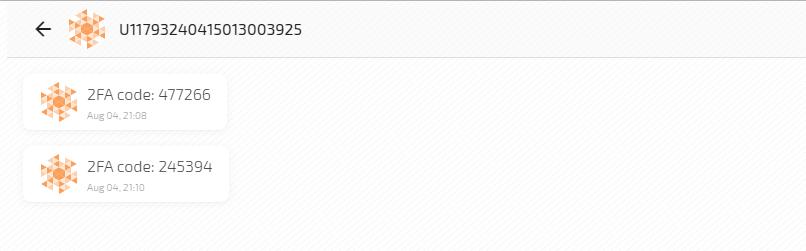
2 Generation of 2FA Codes
The 2FA code needs to be generated for each user login. We use the speakeasy library, but you can choose any other.
const hotp = speakeasy.hotp({ counter, secret: account.seSecretAscii, });
Verify the validity of the 2FA code entered by the user:
se2faVerified = speakeasy.hotp.verify({ counter: this.seCounter, secret: this.seSecretAscii, token: hotp, });
3 Submit 2FA Code
To send a 2FA code, you can use the blockchain node API, the JS API library, or the console. In this example, we use the console - this is the Command Line Interface, a utility that simplifies interaction with the blockchain. To send a message with a 2FA code, you need to use the
send message
command of the console.
const util = require('util'); const exec = util.promisify(require('child_process').exec); … const command = `adm send message ${adamantAddress} "2FA code: ${hotp}"`; let { error, stdout, stderr } = await exec(command);
An alternative way to send messages is to use the
send
method in the JS API library.
4 user interface
The user needs to be given the opportunity to enter the 2FA code, this can be done in various ways depending on the platform of your application. In our example, this is Vue.
The source code of the demo application of two-factor authorization on the blockchain can be viewed on GitHub . The Readme has a link to the Live demo to try.