We will show you some interesting attacks that can make a profit, and talk about the attacks that really took place that night when we went through the Jägermeister and carried out a brain storm. It was fun, but when we sobered up a bit, we talked to people who are engaged in SEO and really learned that a lot of people make money from these attacks.
I'm just a brainless mid-level manager, so I give up my seat and want to introduce you to Jeremy and Trey, who are much smarter than me. I should have a smart and funny introduction, but it’s not there, so I’ll show these slides instead.
The screen shows slides representing Jeremy Grossman and Trey Ford.
Jeremy Grossman, founder and CTO of WhiteHat Security, was named among the top 25 CTOs by InfoWorld in 2007, co-founder of the Web Application Security Consortium and co-author of cross-site scripting attacks.
Trey Ford is the director of architectural solutions at WhiteHat Security, with 6 years of experience as a security consultant for Fortune 500 companies, one of the developers of the PCI DSS payment card data security standard.
I think these pictures make up for my lack of humor. In any case, I hope you enjoy their performance, after which you will understand how these attacks are used on the Internet in order to make money.
We do not strive to impress you with what is shown on this slide, but simply explain what our company is doing. So, White Hat Sentinel, or “White Hat Sentinel” is:
- unlimited number of ratings - control and expert management of client sites, the ability to scan sites regardless of their size and frequency of changes;
- wide scope - authorized scanning of sites to detect technical vulnerabilities and user testing to detect logical errors of unreached business areas;
- elimination of false positive results - our task force checks the results and assigns the appropriate severity and rating of threats;
- development and quality control - the WhiteHat Satellite Appliance system allows us to remotely serve customer systems through access to the internal network;
- improvement and improvement - realistic scanning allows you to quickly and efficiently update the system.
So, we conduct an audit of any sites in the world, we have the largest team of web application pentesters, we carry out 600-700 evaluation tests weekly, and all the data that you see in this presentation are taken from our experience of performing this type of work.
On the next slide you see the top 10 most common types of attacks on world sites. Shows the percentage of vulnerability to certain attacks. As you can see, 65% of all sites are vulnerable to cross-site scripting, 40% allow information leakage, 23% are vulnerable to content spoofing. In addition to cross-site scripting, SQL injection and the notorious fake cross-site queries, which are not among our top ten, are common. But in this list there are attacks with esoteric names, for the description of which vague formulations are used and the specificity of which lies in the fact that they are directed against certain companies.

These are flaws in authentication, flaws in the authorization process, information leakage and so on.
The next slide talks about attacks on business logic. Quality Assurance QA teams usually ignore them. They test what the software should do, not what it can do, and then you can see anything. Scanners, all these White / Black / Gray Bohs, (white / black / gray boxes), all these multi-colored boxes are not able to detect these things in most cases, because they are simply fixated on the context of what the attack may be or what happens It seems when it happens. They have a lack of intelligence and they don’t know if anything worked at all or not.
The same goes for IDS intrusion detection systems and WAF application-level firewalls, which are also unable to detect flaws in business logic because HTTP requests look completely normal. We will show you that attacks related to the shortcomings of business logic arise quite naturally, there are no hackers, no metacharacters and other oddities; they look like regular processes. Most importantly, the bad guys love these kinds of things because the flaws of the business logic make them money. They use XSS, SQL, CSRF, but to carry out attacks of this type is becoming more difficult, and we see that over the past 3-5 years they became less. But they will not disappear by themselves, as buffer overflows will not go anywhere. However, the bad guys think how to use more sophisticated attacks, because they think that the “really bad guys” always strive to capitalize on their attacks.
I want to show you real tricks, and you can take them into your own arsenal to use in the right way to protect your business. Another goal of our presentation is that you might be wondering about ethics.

Online polls and polls
So, at the beginning of the discussion of the shortcomings of business logic, let's talk about online surveys. Online polls are the most common way to find out or influence public opinion. We will start with a profit of $ 0 and then consider the result of 5, 6, 7 months of using fraudulent schemes. Let's start with a very, very simple survey. You know that online polls are carried out by every new site, every blog, every news portal. Moreover, not a single niche is too large or too narrow, but we want to see public opinion in specific areas.
I would like to draw your attention to one survey conducted in Austin, Texas. Since the Austin Beagle won the Westminster Dog Show, Austin American Statesman decided to run an Austin's Best in Show online poll for dog owners in central Texas. Thousands of owners sent photos and voted for their favorites. As in many other polls, there was no prize other than the right to show off your pet.
For voting, an application of the Web 2.0 system was used. You clicked “yes” if you liked the dog and found out if it was the best dog in the breed or not. Thus, you voted on several hundred dogs posted on the site as candidates for the winner of the show.
With this method of voting, 3 types of cheating were possible. The first is countless votes when you vote for the same dog again and again. It is very simple. The second way is a negative multiple vote when you vote a huge number of times against a competing dog. The third method was that literally at the last minute of the contest you placed a new dog, voted for her, so that the opportunity to get negative votes was minimal, and you won by getting 100% positive votes.
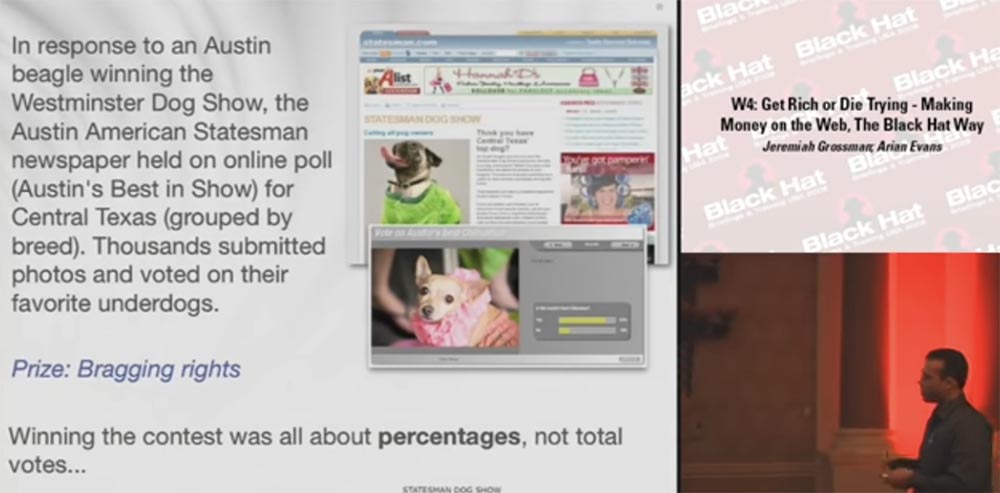
Moreover, the victory was determined as a percentage, and not by the total number of votes, that is, you could not determine which of the dogs scored the maximum number of positive ratings, only the percentage of positive and negative ratings for a particular dog was calculated. The dog with the best positive / negative ratio won.
Hansen's friend, Robert RSnake's colleague, asked him to help her chihuahua Tiny win the competition. You know Robert, he's from Austin. He, as a super-hacker, shut down the Burp proxy and took the path of least resistance. He used the technique of cheating No. 1, having driven it through the Burp cycle several hundred or thousands of requests, and this brought the dog 2000 positive votes and put her in 1st place.

Then he used the technique of cheating No. 2 against rival Taini, nicknamed Chuchu. In the last minutes of the contest, he cast 450 votes against Chuchu, which further strengthened Tiny's position in 1st place with a vote ratio of more than 2: 1, however, in the percentage of positive and negative reviews, Tinyi still lost. On this slide, you see the new face of a cybercriminal discouraged by this outcome.

Yes, it was an interesting scenario, but I think that my girlfriend did not like this performance. You just wanted to win the Austin chihuahua contest, but there was someone who was trying to “hack” you and do the same. Well, now I pass the word to Trey.
Creation of artificial demand and earnings on this
Trey Ford: The concept of “artificial DoS deficit” refers to several different interesting scenarios when we buy tickets online. For example, when booking a special place for a flight. This can apply to any type of ticket, for example, to some sporting event or concert.

In order to prevent the repeated purchase of scarce things, such as seats on the plane, physical items, user names, etc., the application blocks the object for a period of time to prevent conflicts. And here there is a vulnerability associated with the ability to reserve something in advance.
We all know about the timeout, we all know about the end of the session. But this particular logical flaw allows us to choose a place for the flight and then return to make a choice again without paying anything. Surely many of you often fly on business trips, but for me this is an essential part of the work. We tested this algorithm in many places: you select a flight, choose a place, and only after you are ready do you enter payment information. That is, after you have chosen a place, it is reserved for you for a certain period of time - from several minutes to several hours, and all this time no one else can reserve this place. Because of this waiting period, you have a real opportunity to reserve all the seats on the plane, simply by returning to the website and booking the places you want.
Thus, a DoS attack option appears: automatically repeat this cycle for each place on the plane.

We tested this with at least two of the largest airlines. You can find the same vulnerability with any other reservation. This is a great opportunity to raise prices for your tickets for those who want to resell them. For this, speculators simply need to book the remaining tickets without any risk of cash loss. In this way, you can “crash” e-commerce that sells high-demand products — video games, game consoles, iPhones, and so on. That is, the existing drawback of the online reservation or reservation system makes it possible for an attacker to earn money on this or harm competitors.
Decoding Captcha
Jeremy Grossman: Now let's talk about captcha. Everyone knows these annoying pictures that clog up the Internet and are used to combat spam. Potentially, you can also make a profit from captcha. Captcha is a fully automated Turing test that allows you to distinguish a real person from a bot. I found a lot of interesting things while studying the issue of using captcha.
Captcha was first used around 2000-2001. Spammers want to eliminate captcha in order to register for free email services Gmail, Yahoo Mail, Windows Live Mail, MySpace, FaceBook, etc. and send spam. Since captcha is used widely enough, a whole market of services has appeared that offers to circumvent the ubiquitous captcha. Ultimately, it makes a profit - an example is spamming. You can bypass the captcha in 3 ways, let's look at them.
The first is the flaws in the implementation of the idea, or the shortcomings in the use of captcha.
So, the answers to the questions contain too little entropy, such as "write, what is 4 + 1." The same questions can be repeated many times, while the range of possible answers is quite small.
The effectiveness of captcha is checked in this way:
- the test should be carried out in conditions when the person and the server are removed from each other,
the test should not be difficult for a person; - the question should be such that a person can answer it within a few seconds,
Only the person to whom the question is asked should answer; - the answer to the question should be difficult for the computer;
- knowledge of previous questions, answers or their combination should not affect the predictability of the next test;
- the test should not discriminate against people with visual or hearing impairments;
- the test should not have a geographical, cultural or linguistic bias.
As it turns out, creating the “right” captcha is quite difficult.
The second drawback of captcha is the ability to use optical character recognition OCR. A piece of code is able to read a captcha image no matter how much visual noise it contains, see what letters or numbers form it, and automate the recognition process. Studies have shown that most captcha can be easily cracked.
I will quote from specialists from the School of Computer Science at the University of Newcastle, UK. They say about the ease of cracking Microsoft CAPTCHAs: “our attack was able to ensure 92% segmentation success, this implies that the MSN captcha scheme can be cracked in 60% of cases by segmenting the image with its subsequent recognition.” Yahoo’s captcha hack was just as easy: “Our second attack succeeded in segmenting 33.4%. Thus, about 25.9% captcha can be cracked. Our research shows that spammers should never use cheap human labor to get around Yahoo’s captcha, rather they need to rely on a low-cost automated attack. "
The third way to bypass captcha is called "Mechanical Turk", or "Turk". We tested it against Yahoo CAPTCHA immediately after publication, and to this day we do not know, and no one knows, how to defend against such an attack.

This is the case when you have a bad guy who will run an adult site or an online game from where users request some kind of content. Before they can see the next picture, the site that the hacker owns will make a back-end request to an online system you know, say Yahoo or Google, grab the captcha from there and slip it into the user. And as soon as the user answers the question, the hacker will send the guessed captcha to the target site and show the user the requested image from his site. If you have a very popular site with a lot of interesting content, you can mobilize an army of people who will automatically fill out other people's captcha for you. This is a very powerful thing.
However, not only people try to circumvent captcha, this technique also uses business. Robert “RSnake” Hansen in his blog once talked with one Romanian “captcha solver”, who said that he can solve 300 to 500 captcha per hour at a rate of 9 to 15 dollars per thousand captcha solved.

He directly says that his team members work 12 hours a day, solving about 4800 captchas during this time, and depending on how difficult the captchas are, they can receive up to $ 50 per day for their work. This was an interesting post, but even more interesting are the comments that blog users left under this post. A message appeared immediately from Vietnam, where a certain Kwang Hung reported on his group of 20 people, who agreed to work for $ 4 for 1000 guessed captcha.
The following message was from Bangladesh: “Hello! I hope you are all right! We are a leading processing company from Bangladesh. Currently, 30 of our operators are able to solve more than 100,000 captcha per day. We offer excellent conditions and a low rate - $ 2 per 1000 guessed captcha from Yahoo, Hotmail, Mayspace, Gmail, Facebook, etc. We look forward to further cooperation. ”
Another interesting message was sent by a certain Babu: “I was interested in this work, please call me on the phone.”
So it is quite interesting. We can discuss how legal or illegal such an activity is, but the fact is that people really make money from it.
Gaining access to foreign accounts
Trey Ford: the next scenario we’ll talk about is making money by taking over someone else’s account.

Everyone forgets passwords, and for testing application security, password reset and online registration are two different focused business processes. There is a big gap between the simplicity of password reset and the simplicity of registration, so you should strive to simplify the process of password reset as much as possible. But if we try to simplify it, a problem arises, because the easier it is to reset the password, the less security.
One of the most high-profile cases concerned online registration using Sprint's user verification service. Two White Hat team members used Sprint to register online. There are a couple of things that you must confirm in order to prove that you are you, starting with such simple information as your mobile phone number. You need online registration for such things as managing a bank account, paying for services, and so on. Buying phones is very convenient if you can make it from someone else's account and then make purchases and do much more. One of the fraud options is to change the billing address, order delivery of a whole bunch of mobile phones to your address, and the victim will be forced to pay for them. Maniac pursuers also dream of such an opportunity: add GPS tracking function to their victims' phones and track their every movement from any computer.
So, Sprint offers some of the easiest questions to confirm your person. As we know, security can be ensured either by a very wide range of entropy, or by highly specialized issues. I will read to you part of the Sprint registration process, because the entropy here is very small. For example, there is such a question: “select the car brand registered at the following address”, and the options for the brands are indicated: Lotus, Honda, Lamborghini, Fiat and “none of the above.” Tell me, which of you guys has at least one of the above? As you can see, this difficult puzzle is just a great opportunity for a college student to get cheap phones.
The second question: “which of the listed people lives with you or lives at the address below”? It is very easy to answer this question, even if you do not know this person at all. Jerry Stifliin (Stifliin) - in this surname there are three letters "ah", we will return to this in a second - Ralph Argen, Jerome Ponicky and John Pace. In this listing, it is interesting that absolutely random names are given, and all of them are subject to the same regularity. If you calculate it, then it will not be difficult for you to determine the real name, because it differs from the randomly selected names by something characteristic, in this case, the three letters “i”. Thus, Stayfliin is clearly not a random name, and it’s easy to guess, this person is your goal. It is very, very simple.
The third question: “in which of the following cities have you ever lived or never used this city in your address?” - Lonmont (Longmont), North Hollywood (North Hollywood), Genoa (Genoa) or Butte (Butte)? We have three densely populated areas around Washington, so the answer is obvious - this is North Hollywood.
There are a couple of things you need to be careful with in Sprint's online check-in. As I said, you can be seriously hurt if an attacker can change the delivery address of your payment information. What really scares us is that we have the Mobile Locator service.
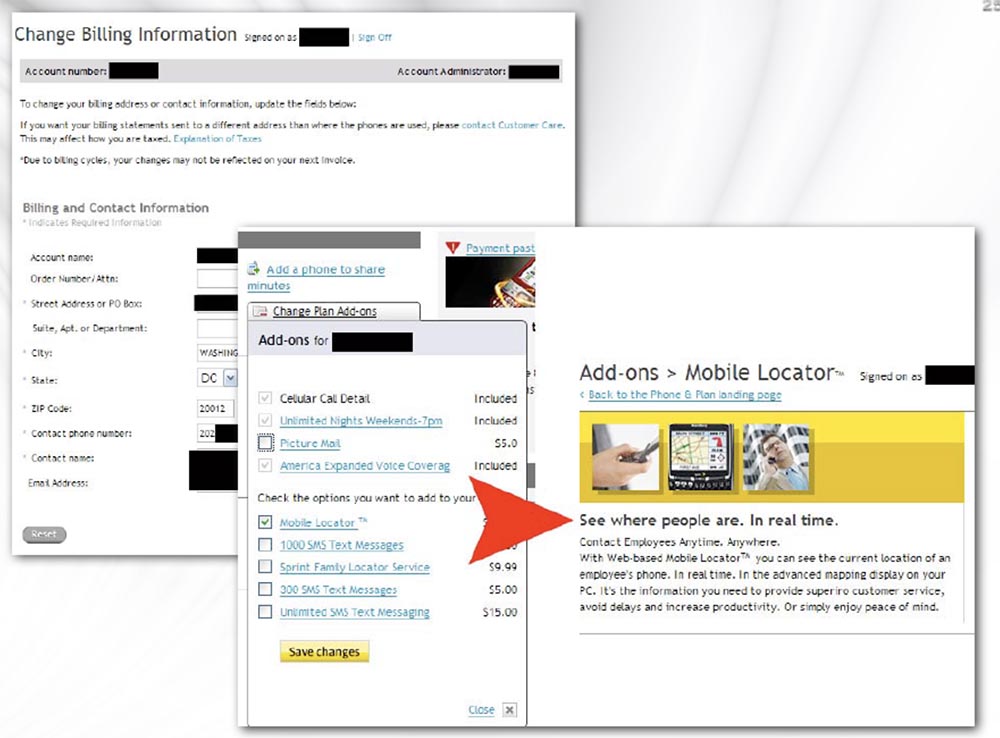
With it, you can track the movements of your employees, as people use mobile phones and GPS and you can see on the map where they are. So, in this process, other rather interesting things happen.
As you know, when resetting a password, the email address prevails over other methods of user verification and security questions. The following slide shows a lot of services that offer to specify your email inbox if the user is having difficulty logging into his account.
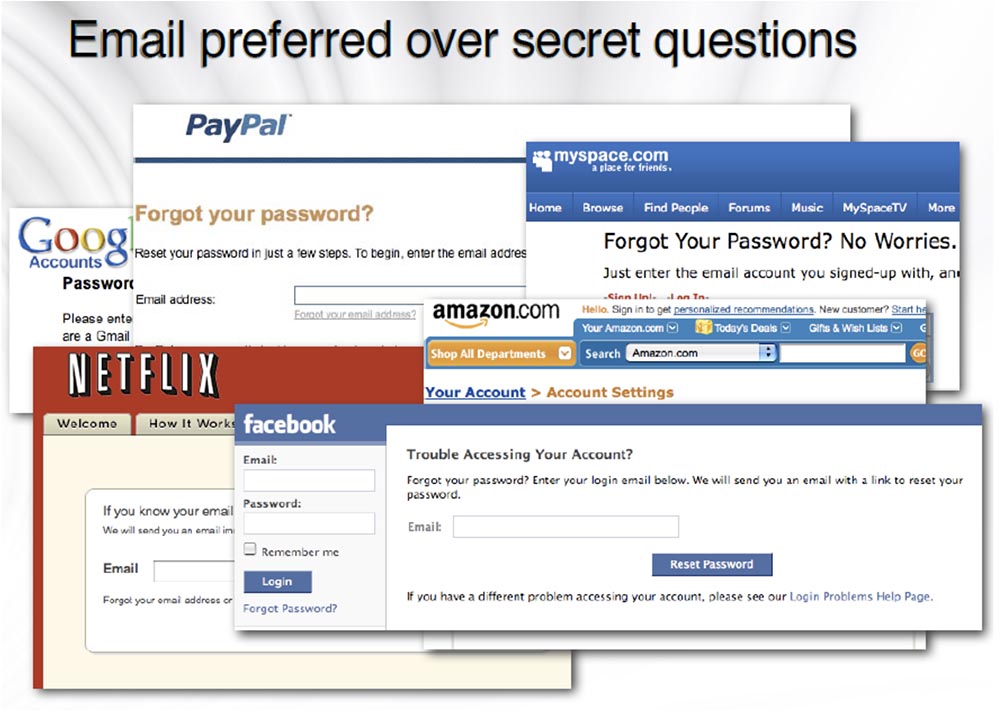
We know that most people use email and have an email account. Suddenly, people wanted to find a way to make money from it. You will always find out the victim's email address, enter it in the form, and you will have the opportunity to reset the password for the account that you want to manipulate. Then you use it on your network, and this mailbox will become your gold vault, the main place from where you can steal all the other accounts of the victim. You will receive the entire subscription of the victim, having taken possession of only one mailbox. Stop smiling, this is serious!
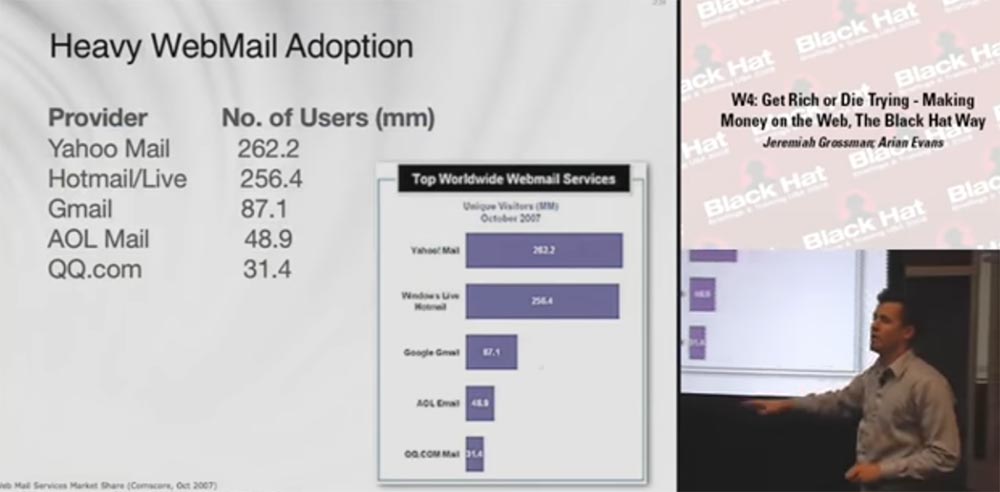
The next slide shows how many millions of people use the appropriate email services. People actively use Gmail, Yahoo Mail, Hotmail, AOL Mail, but you don’t need to be a super hacker to grab their accounts, you can keep your hands clean by using outsourcing. You can always say that there’s nothing to do with it, you didn’t do anything like that.
So, in China, the online service "Password Recovery" is based, where you pay to hack your account. For 300 yuan, this is approximately $ 43, you can try to reset the password of a foreign mailbox with a success rate of 85%. For 200 yuan, or $ 29, you will be successfully reset with a 90% mailbox password for your home mail service. One thousand yuan, or $ 143, costs hacking any company’s mailbox, but success is not guaranteed. You can also use outsourcing to crack passwords on the services 163, 126, QQ, Yahoo, Sohu, Sina, TOM, Hotmail, MSN, etc.
BLACK HAT USA Conference. Get rich or die: make money on the Internet using Black Hat. Part 2 (link will be available tomorrow)
A bit of advertising :)
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, cloud VPS for developers from $ 4.99 , a 30% discount for Habr users on the unique entry-level server analog that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share a server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?