Social engineering came out on top in the ways of stealing money from accounts and cards of individuals. With the help of psychological tricks, fraudsters mislead customers for the purpose of profit. The classic scheme of such fraud is when the bank’s security service supposedly calls the victim.

However, the arsenal is not limited to persuasion. We have collected five popular fraudulent tools with which we “diverted” money from your colleagues and acquaintances in 2019. No theory - only real cases.
All major banks have anti-fraud systems that analyze transactions, look for anomalies and fraudulent patterns.
The development of intruder tools and systems that oppose them is similar to the evolution of armor and shell - this is an endless process. For obvious reasons, the article will not describe what and how exactly banks can calculate, but it is important to understand: like fire, it is better to prevent fraud.
In the Tinkoff Stories in the mobile application, we regularly talk about how not to fall for the tricks of inventive attackers, and also launch several thematic projects at once, including the animated series.
Basic scheme
Fraudsters are represented by the bank’s security service and report an attempt to debit funds from the client’s account. To cancel an unauthorized operation, they are asked to give the full card number and confirmation codes from SMS. In fact, at that moment they either enter your bank account or make transactions on the Internet - then they will ask for another validity period and a three-digit code on the back of the card.
If before there were typical portraits of such victims, the most common of which are people of advanced age, now the edges are erased. Neither gender nor age now affects the ability to withstand diverse patterns of tricks.
IVR
The obvious minus of the standard scenario for scammers is the inevitable struggle with the fears of customers, their questions, which often arise. For example, in the same SMS it is written that no one should be given a code.
However, technology does not only help decent citizens. The swindler says that the confirmation code cannot be communicated to anyone - this coincides with the text of the SMS and inspires confidence in the victim.
The fraudster asks to enter the code in tone mode after switching to IVR (interactive voice menu), which says in a standard announcer's voice that you need to enter the code in tone mode after the signal.
Remote access
A scammer’s call usually takes the client by surprise. The caller is introduced by a bank employee and reports the detection of malware on the client’s device. To resolve it, you must provide access to the device. The victim needs to download a remote access program to his smartphone - TeamViewer, Anydesk or another.

After installation, the bank employee is asking the client to name the code displayed in the application. A fraudster enters this code into a program on his device. After the victim provides all the permissions (if necessary, downloads the addon for full control), the attacker receives, depending on the OS and the smartphone manufacturer of the victim:
- Android (for example, Samsung) - full remote access to the client device. A fraudster makes payments from a client device, since transaction confirmation codes come to him.
- iOS and some Android devices (e.g. Nexus) - access to view. The fraudster manages the client’s actions (“Click here, and now - here”). As a result, the client transfers the funds to the fraudster himself.
Scam number spoofing
Some attackers call from simple sims bought by a handful from the subway. In this case, the victim receives a call from the bank’s false employees from a number with typical prefixes 926, 916 and others.
Other scammers, in pursuit of converting calls to stolen money, turn to the telecommunication services of substituting a phone number.
Technically, number substitution is possible due to the exploitation of vulnerabilities in telephone connection protocols, such as SIP and ISDN PRI, which do not provide a mechanism for monitoring the authenticity of the message sender.

A beautiful number of the type 8 (495) xxx-xx-xx that appears on the smartphone screen dulls the victim's alertness.
Cash-in to a secure account
A bank customer receives a call allegedly from a bank security service. During the conversation, it turns out that the client’s account is in danger and funds can be withdrawn from him any minute.
Scammers ask for a card number and a verification code to enter their personal account to help the client. Having gained access to a huge amount of information (data on operations, accounts, balances), fraudsters easily rub their trust, removing the last doubts (“Scammers cannot know so much about me,” the client thinks).
A trained victim is declared that the only way to save money is to withdraw it to a safe account. Further, two scenarios are possible.
Translation The client is offered to independently transfer funds to a secure account. Fraudsters with the help of psychological pressure convince to make a transfer to the drop account. Drop is a person who draws up a regular debit card for a small fee, then transfers it to scammers who use it to cash out stolen money.
ATM Fraudsters can use cash-in ATMs for their own purposes.
The client is informed that they urgently need to go to the nearest ATM and withdraw all the money. For especially large victims (and scammers at this moment see how much money is in the accounts) they can even call a taxi.
After withdrawing money, the victim is asked to deposit cash into the scam account. They intimidate with fines and penalties, and on the other hand, they lure them with promises to compensate inconveniences with monetary compensation. In the end, fraudsters gain the upper hand, and the client replenishes their account with freshly withdrawn cash.
Forwarding on the victim's number
Banks are not asleep and, having revealed a suspicious transaction, are in a hurry to contact customers.
Typically, false security relies on their persuasion skill: they set the client against real bank employees and inspire the need to confirm transactions. It may look like a syur, but such are the realities.
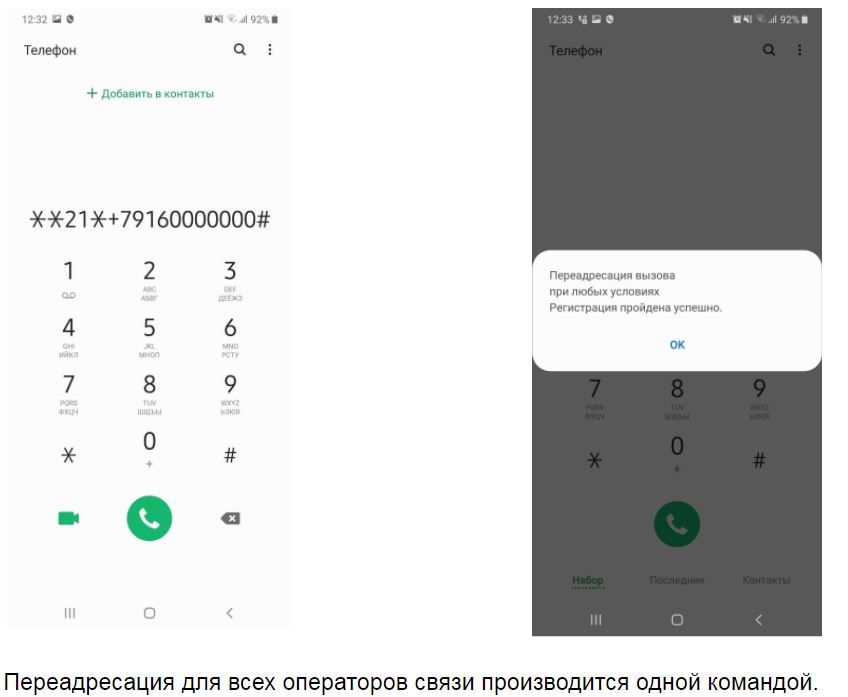
But some scammers rely more on technological solutions. Instead of complex processing, the client is asked to dial a sequence of characters on the phone, which in reality is a USSD command to enable the forwarding of the victim's incoming calls to the number of fraudsters. In addition, they request identification data, according to which they will try to impersonate a client when calling this security service.
Conclusion
Fraudsters can use several funds from this list at once. Therefore, it is important to be on guard for any calls from the bank and not to rush to trust the caller. He may threaten fines from the bank and entice bonuses for fulfilling his requirements.
Therefore, you need to remember that real bank employees will never ask:
- Tell them the transaction confirmation code.
- Install programs on a smartphone, especially with remote access functionality.
- Run USSD commands on the phone.
- Transfer or deposit your money into an account of third parties through an ATM.
In the next article - even more about how to confront scammers who are waiting for you literally at every step: in social networks, investments, on message boards and dating sites.
And now you can get acquainted with the materials www.tinkoff.ru/secure .