
Here's a Docker security guide. Feedback is welcome, as it is rather a collection of excerpts from various resources, and not all of them have been thoroughly checked. The recommendations are divided into three categories:
- Necessary measures inside the host operating system when working with Docker;
- Instructions related to the assembly configuration file and creating containers;
- Security tools that can integrate with specific Docker Enterprise features.
Various resources have become the basis for leadership, many of which are listed below. It cannot be called exhaustive, but it covers all the basics. Additional information can be found in the description of CIS tests (the link is given at the end of this manual), as well as in the documentation for Docker.
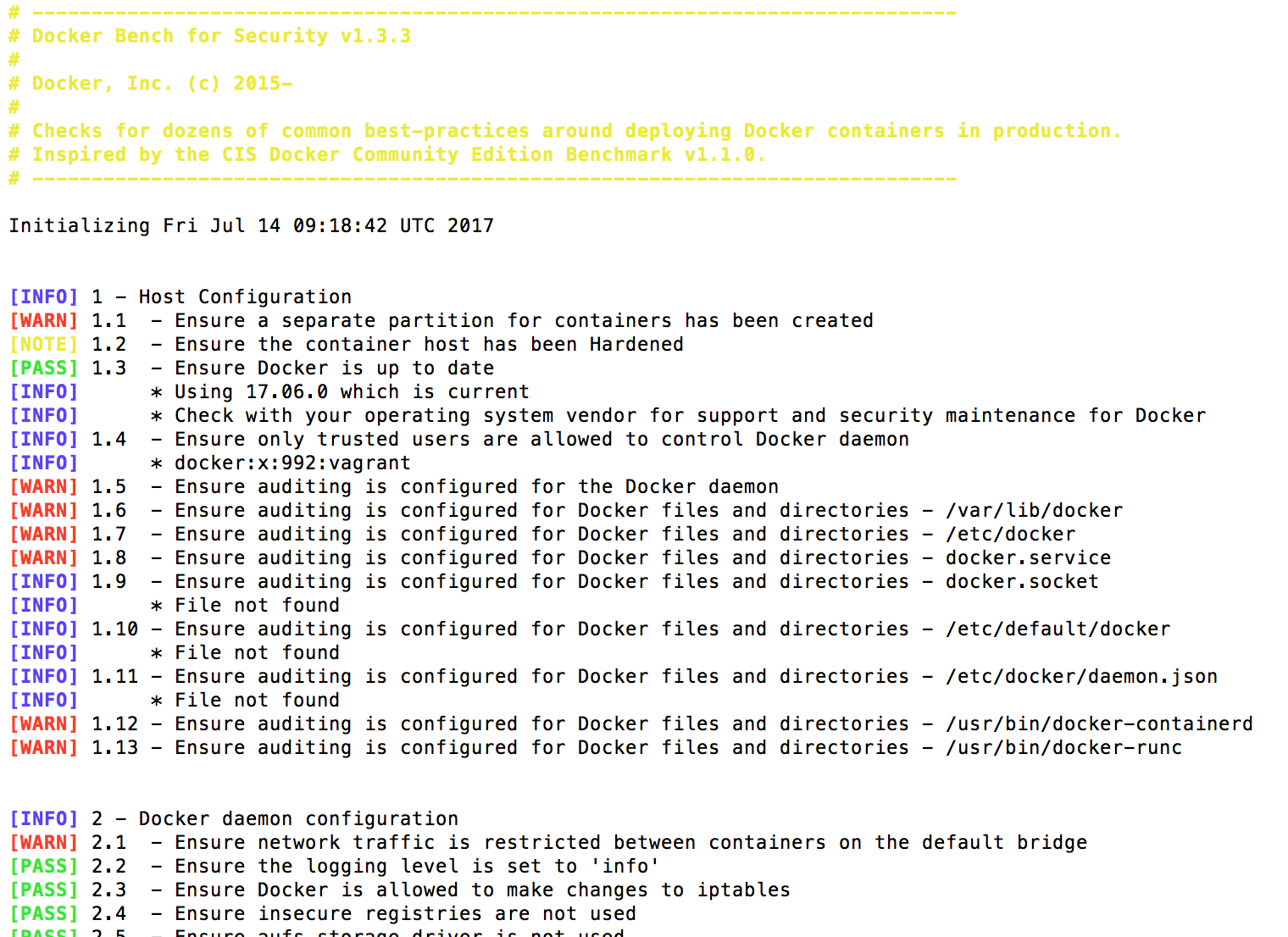
Docker security benchmark
Docker Bench for Security automatically checks your Docker for compliance with the most common best practices. The script is a good heuristic security test, but it should not be considered as a comprehensive analysis tool.
Host OS
Obviously, the Docker container cannot be protected if the host system itself is not protected. Therefore, you must follow the best practices in the field of operating system security. In addition, it would be prudent to conduct a vulnerability analysis in addition to the following recommendations.
Audit rules
Create and use audit rules for files associated with Docker using
auditctl
. For example, you can add
-w /usr/bin/dockerd -k docker
to
/etc/audit.rules
and restart the audit service.
FIPS mode
Enabling FIPS mode forces cryptographic tools to switch to the algorithms introduced in FIPS (American Federal Information Processing Standards - approx. Transl.) , Thus complying with federal and industry standards and requirements. If the host OS supports FIPS mode, you can enable it by running the following commands:
sed -i 's/GRUB_CMDLINE_LINUX="/GRUB_CMDLINE_LINUX="fips=1 /g' /etc/default/grub grub2-mkconfig -o /boot/grub2/grub.cfg && reboot
You must also enable FIPS in the Docker Engine:
mkdir -p /etc/systemd/system/docker.service.d 2>&1; echo -e "[Service]\n Environment=\"DOCKER_FIPS=1\"" > /etc/systemd/system/docker.service.d/fips-module.conf; systemctl daemon-reload; systemctl restart docker
See the Docker and Red Hat documentation for more information.
Docker secrets
Confidential data should be kept as secrets. You can start the corresponding service using the docker service create command:
docker service create --label com.docker.ucp.access.label=/prod --name nginx --publish 443 --secret source=orcabank_prod_mobile.ca.pem.v1,target=ca.pem nginx
See the documentation for details.
Docker configuration file
The following settings can be added to the
/etc/docker/daemon.json
configuration
/etc/docker/daemon.json
:
-
"icc":false
- disables the exchange of data between containers to avoid unnecessary information leakage. -
log-level: "info"
- captures all logs except debugging. { "log-driver": "syslog", "log-opts": { "syslog-address": "udp://1.2.3.4:1111" } }
- connects remote logging, forwards them to the specified address. Only works if the syslog daemon is running. TCP and UDP are accepted as options. Connection for each specific container is also possible. To do this, a special flag is set when starting Docker (--log-opt syslog-address=ADDRESS
).-
"userns-remap": "Your_User"
- prevents privilege escalation by isolating the namespace for a specific user.
Transport Security
Only users with access to the TLS client credentials should be able to connect to the Docker daemon (if remote access is necessary).
Authorization Plugins
Decide which users are allowed to execute which commands and create the appropriate authorization plugin for Docker. Then run the Docker daemon and add the plugin to it:
dockerd --authorization-plugin=PLUGIN_ID
To learn more about creating authorization plugins, see the documentation .
Daemon options
The Docker daemon works with a set of default parameters.
-
--live-restore
- this option helps reduce container downtime during system shutdown or reboot. It becomes easier to patch or update them with minimal downtime; -
--userland-proxy=false
- when hairpin NATs are available or used, the proxy in user space becomes a redundant service, which only increases the number of possible attack vectors; -
--no-new-privileges
- prevents containers from obtaining additional privileges using suid or sguid; -
--seccomp-profile /path/to/profile
- if you have your own seccomp profile, you can use it with this flag. Learn more about Seccomp and Docker here .
Configuring containers and assembly files
User Creation
Make sure that a user has been created for the container and run it under that user (DO NOT run the container under the root).
Remote access
Deny remote access to the daemon. If it is still necessary, protect it with certificates.
Isolate username space
It is especially important to make sure that the username space in Docker is isolated, because by default it is shared with the host name space. In some cases, this can be used to elevate privileges or even to go outside the container. You can isolate a user namespace by editing the configuration file (as described above in the Docker Configuration File section). An additional mention of this problem is due to its importance.
Healthcheck
Healthcheck (Health Check) is a powerful tool for checking container integrity. It is configured in the Dockerfile using the
HEALTHCHECK
. Healthcheck allows you to verify that the container is working properly. In the example below, a health check ends with 0 if the server is running, and 1 if it "crashed":
HEALTHCHECK CMD curl --fail http://localhost || exit 1
SELinux
If SELinux is supported by the host operating system, create or import a SELinux policy and run Docker in daemon mode with SELinux enabled:
docker daemon --selinux-enable
In this case, Docker containers can be launched with security settings, for example:
docker run --interactive --tty --security-opt label=level:TopSecret centos /bin/bash
Network interfaces
By default, Docker listens on all network interfaces. Since in most cases traffic is expected on only one of them, such an approach unreasonably increases the risk of an attack. Therefore, when starting a container, you can bind its ports to specific interfaces on the host:
docker run --detach --publish 10.2.3.4:49153:80 nginx
Cached Image Versions
When downloading images, make sure that the local cache matches the contents of the repository. Otherwise, you may receive an outdated version of the image or an image containing vulnerabilities.
Network bridge
The default network model,
docker0
, is vulnerable to attacks like ARP-spoofing and MAC-flooding. To solve this problem, create a network bridge in accordance with your specifications, as described here .
Docker socket warning
Never throw a Docker socket inside a container. Otherwise, the container will be able to execute Docker commands and, therefore, communicate with the host operating system and control it. Do not do this.
Configuring Docker Enterprise
Docker trust
Docker Trust allows you to generate keys that can be used to verify the cryptographic integrity of images. Docker Trust keys can be used to sign Docker images with private keys, which are verified by public keys on Notary Server. More information here . Enabling Docker Trust in Enterprise Engine is described in detail in this section of the documentation .
Vulnerability Scan
Docker Enterprise has a built-in vulnerability scanner that makes it possible to download the CVE database for offline-scanning vulnerabilities in images. Regular scanning of images helps to make them safer: the user immediately receives warnings about vulnerabilities found. For more information on how to do this, see here .
Note perev. : There are also Open Source-vulnerability scanners in Docker-images, see examples at the end of the article.
LDAP and UCP Integration
Universal Control Plane can be integrated with LDAP. The result will be a simplified authentication system to avoid unnecessary duplication. Read more about this in the article Integrate with an LDAP directory .
Other materials
For more information on Docker's best security practices, go to docs.docker.com . We also recommend downloading Center for Internet Security tests for Docker .
Bonus from the translator
As a logical complement to this article, we are publishing a list of 10 popular Open Source security tools in Docker . It was borrowed from another article (authored by Bill Doerrfeld of Doerrfeld.io).
NB : For more on many of the projects mentioned here, see also the article “ 33+ Kubernetes Security Tools ”.
- Docker Bench for Security is a script already mentioned at the very beginning of the article that checks Docker containers for compliance with common security practices.
- Clair is probably the most popular utility for static analysis of vulnerabilities in a container. It uses numerous CVE vulnerability databases (including trackers of leading Linux distributions such as Red Hat, Debian, Ubuntu). It offers an API for developers and a simple opportunity to expand functions (through the addition of "drivers"). It is used in the popular public registry of container images (similar to the Docker Hub) - Quay.io.
- Cilium is a kernel-level network security solution based on BPF network packet filtering technology.
- Anchore is a CVE -based utility for analyzing image contents for security vulnerabilities. In addition, it allows you to apply custom policies (based on various data including white / black lists, file contents, etc.) to assess the security of containers.
- OpenSCAP Workbench is an entire ecosystem for creating and maintaining security policies across platforms. For checking containers, it offers the
oscap-docker
utility. - Dagda is a utility for scanning Docker containers for vulnerabilities, trojans, viruses and malware. CVE databases include OWASP dependency checks, Red Hat Oval database, Exploit Database exploit repository.
- Notary is a framework for signing Docker images, originally created by Docker Inc (and then turned over to CNCF for development). Its use allows you to delegate roles and distribute responsibilities among containers, as well as verify the cryptographic integrity of images.
- Grafaes is a metadata API designed to manage internal security policies. As an example, it improves the performance of container security scanners. Shopify uses this API to manage metadata across its 500,000 images.
- Sysdig Falco - a utility for Kubernetes that monitors the behavior of the system: activity in containers, on hosts, on the network. Allows you to configure continuous checks in the infrastructure, detect anomalies and send alerts to any Linux system calls.
- The Banyanops Collector is another tool for static image analysis of Docker containers. Allows you to "look" into the image files, collecting the necessary data, applying the necessary policies, etc.
Another good selection of practical tips on making Docker safer can be found in this Aqua Security article . Many of her tips overlap with those already mentioned above, but there are others. For example, the authors propose organizing monitoring of activity in containers and indicate what to look for when using Docker Swarm.
For those who wish to dive into this topic in more detail last year, the book “ Docker Security: Quick Reference ” was published , fragments of which are freely available here .
Finally, for practical acquaintance with some aspects of Docker security: Seccomp profiles and using Linux kernel capabilities in containers, you can go through the corresponding laboratory work on the Play with Docker * resource - see the Security section.
* We talked about this resource two years ago, and in November 2018, a very interesting (from a security point of view) story happened to it. In short, specialists from CyberArk Software Ltd. managed to crack it: to achieve the ability to execute commands outside the containers, i.e. on the host system. A great illustration of security issues in Docker, right? Read all the details of what happened here .
PS from the translator
Read also in our blog:
- " Vulnerable Docker VM - a virtual puzzle game by Docker and pentesting ";
- “ 19% of the most popular Docker images do not have a password for root ”;
- “ 33+ Kubernetes Security Tools ”;
- “ Docker and Kubernetes in security-demanding environments ”;
- “ 9 Best Security Practices at Kubernetes ”;
- “ OPA and SPIFFE are two new projects at CNCF for cloud application security .”