Sometimes an organization, quite unexpectedly for itself, can detect initially implicit information systems of personal data (PD). For example, a company is considered a personal data operator if its website has feedback forms, registration / authorization and other forms of data collection by which it is possible to identify the subject.

Control and supervision regarding compliance with the requirements of the federal law “On Personal Data” is carried out by the regulators:
- Roskomnadzor regarding protection of the rights of subjects of personal data;
- FSB of Russia in terms of fulfilling requirements in the field of cryptography;
- FSTEC of Russia in terms of compliance with requirements to protect information from unauthorized access and leakage through technical channels.
Since the Federal Law “On Personal Data” is only the basis of legal support for the protection of personal data, its requirements were further specified in acts of the Government of the Russian Federation and the Ministry of Communications, and other regulatory and methodological documents of regulators.
Federal authorities regulating activities in the field of personal data processing
|
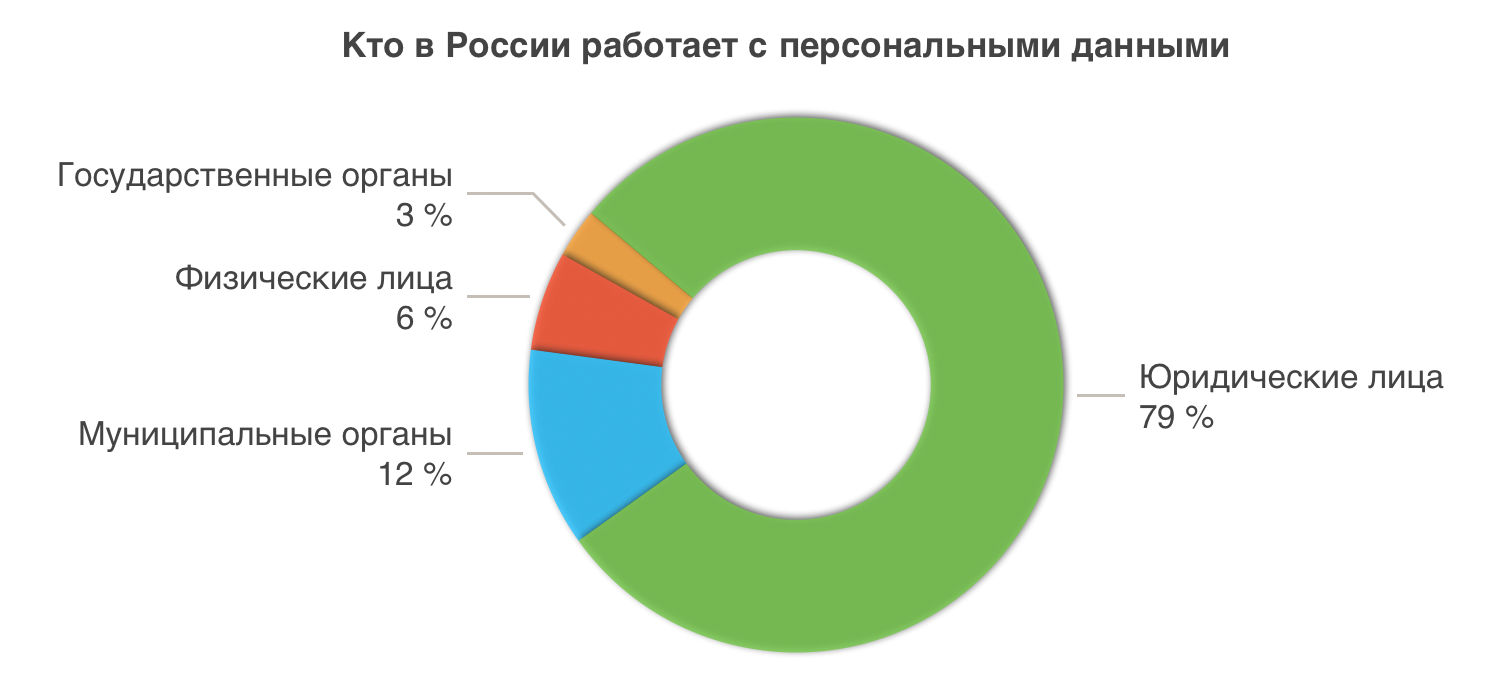
Types of personal data
According to the Federal Law-152, personal data is any information related to a specific person (based on such information) (a personal data subject). For example: name, date and place of birth, address, marital, social, property status, education, etc.
Personal data is divided into several categories:
SpecialPD related to racial, ethnicity, political views, religious or philosophical beliefs, state of health, intimate life |
BiometricPD, which characterize the physiological and biological characteristics of a person, on the basis of which it is possible to establish his identity and which are used by the operator to establish the identity of the subject of personal data |
OtherPD related to a directly or indirectly determined or determined individual, and not related to the above categories |
Publicly availablePD received from publicly available sources in which data was published with the written consent of the personal data subject |
- collection
- record
- systematization
- accumulation,
- storage,
- clarification (update, change),
- extraction
- using,
- transmission (distribution, provision, access),
- depersonalization
- blocking
- removal
- destruction of personal data.
Responsibility for Violations
According to Article 24 of the Federal Law-152, persons are liable for violation of the law in accordance with the legislation of the Russian Federation.
When checking the company, the regulators are guided by the Federal Law-152 and a number of by-laws. The audit can be both planned and unscheduled - on the facts of violations, as well as to control the previously issued order to eliminate them.
Persons who violate the requirements for the protection of PD may face not only civil and disciplinary, but also administrative and even criminal liability.
How to meet the requirements of FZ-152?
So, a company or organization that processes personal data or other restricted information should protect this information in accordance with the law. This not only requires serious expertise, knowledge and experience, but also involves technical difficulties and considerable costs.
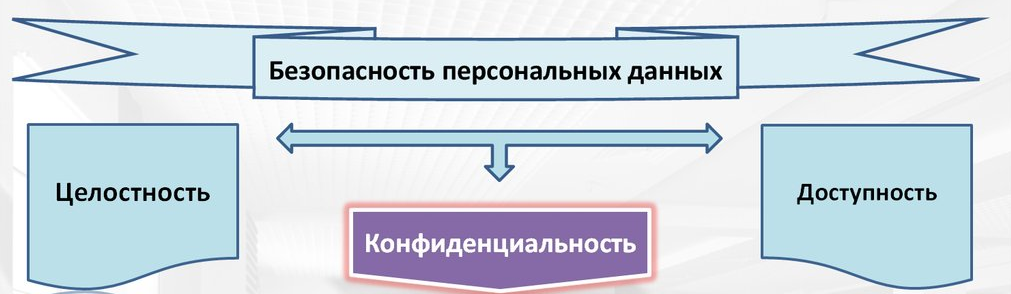
According to the official definition approved by the FSTEC, “... Security of personal data is the state of protection of personal data, characterized by the ability of users, technical means and information technologies to ensure the confidentiality, integrity and availability of personal data when they are processed in personal data information systems ...”
In order to fulfill the organizational, legal and technical requirements of FZ-152, independently, you need to study not only the law itself, but also its by-laws, to figure out exactly what measures need to be taken. Outsourcing specialists can study the processes of personal data processing in the company, draw up the necessary documents, implement security measures, etc.
Integrated information security system includes:
- Intrusion Prevention Tools (IDS).
- Firewalling (FW).
- Protection against malware.
- A system for monitoring and recording security events.
- The system of cryptographic protection of communication channels (encryption).
- Virtual environment protection tools, system of protection against unauthorized access (NSD), identification and access control.
- Security analysis / vulnerability identification system, etc.
In addition, integrated information security involves not only technical, but also organizational measures.
Cloud FZ-152: implementation features
A number of Russian providers provide cloud infrastructure services for the deployment of information systems in accordance with the requirements of federal legislation regarding PD. When placing client systems in the cloud, the provider assumes the solution of many IS issues, including those related to the protection of personal data. When migrating to the cloud, it will protect the IT infrastructure, and this will remove some of the responsibilities from the client. For example, a provider complies with the requirements of Federal Law 152 regarding the protection of a virtualization environment.
Providers can also provide customers with expert support in solving the data protection problem: determine the required level of security and, in accordance with this, offer an implementation option; develop documentation to meet the requirements of the legislation of the Russian Federation.
A secure cloud will help optimize the organization’s costs by reducing the cost of creating and maintaining an IT infrastructure and internal information protection system. As a rule, qualified experts provide comprehensive technical support and support, including consulting and the development of a package of documents for certification in regulatory authorities, and the platform for the provision of services meets stringent technical standards and meets the necessary organizational requirements. Customers can take advantage of the services of preparing the necessary documentation and protecting the ISPD at the application and operating system level.
Risk and vulnerability management processes, incident investigation, internal and external security audits, as well as regular monitoring and testing of the network, information security systems and processes are also provided. Qualified specialists provide round-the-clock support of IT infrastructure.
Together, these measures ensure compliance with federal legislation regarding the protection of personal data.
Certified platform
IBS DataFort provides such a service based on the certified DF Cloud platform . All the technical part, administration and virtualization tools of this platform comply with the standards and requirements of FZ-152.

Secure Cloud Architecture IBS DataFort.
The platform provides guaranteed protection for ISPDN (up to the 1st security level inclusive), GIS (up to the 1st security level inclusive) and secure data storage in the Tier III data center. The platform uses certified firewalls, intrusion detection and prevention tools (IDS / IPS), communication channel encryption (GOST VPN), anti-virus protection, anti-unauthorized access protection, virtualization environment protection, and vulnerability scanning tools.
The FZ-152 cloud is also a suitable solution for those who place high demands on confidentiality and data protection, want to strengthen their business reputation or gain such a competitive advantage as a confirmed high level of information security.
How to “move” to such a cloud? Is “seamless migration” possible? Quite. For example, IBS DataFort safely transfers ISPDn to its secure cloud, minimizing downtime and impact on the company's business processes (including from foreign sites).
Bringing IT infrastructure in accordance with Federal Law-152
The process of bringing the client’s IT infrastructure in accordance with the requirements of Federal Law-152 begins with an audit and assessment of the current level of security.
An audit of a client’s IT infrastructure includes an examination of PD processing and protection processes and an examination of a customer’s ISPD. A survey report is prepared with a detailed description of PD processing processes from a technical point of view.
The work also includes modeling threats and violators and drawing up an act to determine the level of security for ISPDn. Based on the results of the audit, a private statement of work is compiled for the ISPDn security system and defines the requirements for the designed system.
A set of policies, instructions, regulations and other documents for the protection of personal data is being developed. At the same time, specialists are trying to optimize the costs of the customer for the implementation of protective equipment.
IBS DataFort provides documentation preparation and ISPD protection services to comply with federal legislation on the protection of personal data and can help in the preparation and certification (ISPD, GIS, AS).
Certification is carried out by independent auditors licensed by the FSTEC and the FSB of Russia. Passing such certification confirms reliable protection of personal data of partners and customers of the company from external threats, comprehensive compliance with the requirements of regulators. It is important that customers get the convenience of a “one-stop shop”: everything is provided by one company - IBS DataFort.
For the personal data operator, this means a willingness to inspect Roskomnadzor, FSTEC and the FSB, eliminating the risks of blocking resources, and the absence of claims and sanctions from the regulator.
Such a service is relevant for many categories of customers of the state and corporate segments and can be claimed by personal data operators who want to bring their activities in accordance with the law. IP placement in the closed segment of the provider’s infrastructure, certified according to all necessary standards and requirements, eliminates the need for the customer to independently organize all work.