Firstly , they integrated clicker into harmless applications - cameras and image collections - that performed the declared functions. As a result, users and information security experts had no clear reason to consider them as a threat.
Secondly , all malware was protected by the commercial Jiagu packer, which complicates detection by antiviruses and makes code analysis difficult. Thus, the Trojan was more likely to avoid detection by the built-in protection of the Google Play directory.
Thirdly , virus writers tried to disguise the Trojan as well-known advertising and analytical libraries. After adding to the host programs, it was embedded in the Facebook and Adjust SDKs present in them, hiding among their components.
In addition, the clicker attacked users selectively: he did not perform any malicious actions if the potential victim was not a resident of one of the countries of interest to attackers.
The following are examples of applications with the Trojan embedded in them:

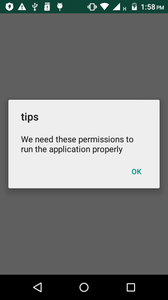
After installing and starting the clicker (hereinafter, its modification Android.Click.322.origin will serve as an example), it tries to access the notifications of the operating system by showing the following request:
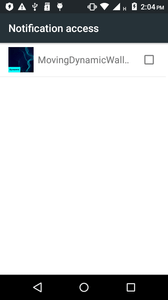
If the user agrees to grant him the necessary permissions, the Trojan will be able to hide all notifications about incoming SMS and intercept message texts.
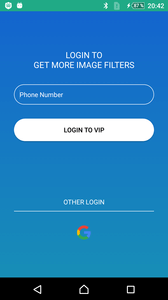
Next, the clicker sends to the control server the technical data about the infected device and checks the serial number of the victim’s SIM card. If it corresponds to one of the target countries, Android.Click.322.origin sends information about the phone number attached to it to the server. At the same time, for users from certain states, the clicker shows a phishing window where he offers to enter the number or log in to his Google account:
If the victim’s SIM card does not belong to the country of interest to the attackers, the Trojan does not take any action and stops the malicious activity. Studied clicker modifications attack residents of the following states:
- Austria
- Italy
- France
- Thailand
- Malaysia
- Germany
- Qatar
- Poland
- Greece
- Ireland
After transmitting the information about the number Android.Click.322.origin expects a command from the managing server. The Trojan sends jobs to the Trojan that contain website addresses for download and JavaScript code. This code is used to control the clicker through the JavascriptInterface interface, display pop-up messages on the device, perform clicks on web pages and other actions.
After receiving the address of the site, Android.Click.322.origin opens it in an invisible WebView, where the previously adopted JavaScript with parameters for clicks is also loaded. After opening a site with a premium service, the Trojan automatically clicks on the necessary links and buttons. Then he receives verification codes from SMS and independently confirms the subscription.
Despite the fact that the clicker does not have the function of working with SMS and access to messages, he bypasses this limitation. This happens as follows. The Trojan service monitors notifications from the application, which by default is assigned to work with SMS. When a message arrives, the service hides the corresponding system notification. Then he extracts from him information about the received SMS and transmits it to the Trojan broadcast receiver. As a result, the user does not see any notifications about incoming SMS and does not know what is happening. He learns about subscribing to the service only when money starts to disappear from his account, or when he goes to the message menu and sees SMS related to the premium service.
After Doctor Web experts contacted Google, the detected malicious applications were removed from Google Play. All known modifications of this clicker are successfully detected and deleted by Dr.Web for Android anti-virus products and therefore do not pose a threat to our users.
Read more about Android.Click.322.origin