Miners, Diversers, and Cobalt: How We Provide Customers Secure Internet Access

Every security guard in his life has faced the fact that employees go to the Internet, bypassing proxies, download movies via torrent and use TeamViewer. In this post, we will talk a little about how we solve problems with organizing safe Internet access using the service model and share the hellish cases that we face with customers.
Not so long ago, we talked about the architecture of the Unified Cybersecurity Services Platform (EPSC), which is the core of the Solar MSS ecosystem of managed cybersecurity services. also includes service on protection against network threats - Unified Threat Management (UTM).
Each UTM manufacturer has its own set of functions. We have the following:
- firewall;
- intrusion prevention system;
- network antivirus;
- Web traffic filtering
- application usage control.
It often happens (this is especially true for banks or retail) that a company has a head office in which information security is at a more or less acceptable level, and there is also a branch network where everything is not so simple. Each office has its own system administrator and its own rattles. And one security guard is responsible for protecting this entire infrastructure. Well, or the information security department, but, in one way or another, they are remote specialists.
The following problems usually arise here: first, you need to somehow control the actions of each remote system administrator. Secondly, and even more importantly, it’s necessary to somehow roll out the unified settings of security features to all branches, and then verify that they are updated correctly and quickly. Many security guards in this situation also quite quickly come up with the idea of centralizing Internet access for all branches, which is also very difficult. To do this, you need to establish connectivity between all branches and the head office (or data center) and direct all traffic from the periphery to the center. It is quite expensive, plus the first and second questions remain unresolved.
Our business model is built to offer a solution to all these problems at once. We organize the connectivity of customer sites through a platform of virtualized information security services. As a result, all traffic from offices to the Internet and back goes through the UTM.
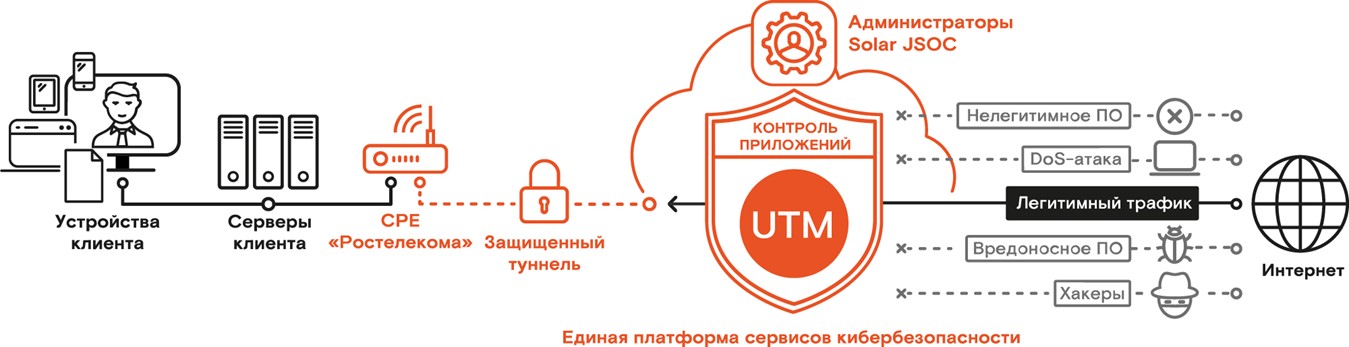
Thus, we get a centralized access to the Internet, uniform settings for all branches and a single point of control for information protection. This ensures that there are no situations when the system administrator once opened the remote administration ports and forgot to close them, and then the company was hacked through them. In parallel, this solves the problem of combining the organization’s branches into a single KSPD (we already spoke about the “goodies” of SD-WAN technology).
Additionally, this approach helps to reduce the risks of using prohibited applications in the company. Usually, after connecting the customer to the platform, we first look at the most popular applications and evaluate how much traffic they consume. This allows you to quickly identify the use of tools for remote administration, torrents, hacking tools and pirated software.
Mineil-minil, but did not mine
In one of the organizations, we identified a system administrator who used Kryptex - a mining guy,

In general, I do not follow the rates of cryptocurrencies, but, apparently, they are on the rise again - recently we again began to often encounter cases when administrators try to mine on corporate servers.
Pour files
An example from another opera. We connected the next customer to the platform, which officially allowed all its administrators to use TeamViewer. Actually, we don’t welcome such a practice, but now it is everywhere, and, in general, our business is to warn. And at some point we see that a connection is established to the workstation of one of the admins once a day through the little-known remote administration tool Splashtop.

They notified the customer - as expected, the actions were not authorized. We watched the sessions from the host: it turned out that at the time Splashtop was launched, a connection was established with an external file hosting service, where about 500 MB was transferred. Unfortunately, host logging was not configured, so it was not possible to quickly determine the cause of the incident. They began to analyze hard drives and found a compromise indicator - a hash of one of the files listed in our Threat Intelligence database. This file turned out to be the PassView utility, which is used to extract hidden passwords. Anti-virus defined it simply as undesirable software (not a virus) and did not take any action. And in the assembly of this utility turned out to be a remote administration tool - Splashtop.
Due to the lack of logs, it is not known how long the attacker was in the infrastructure, but with the last connection, many internal documents “including” the signature stamp “Particleboard” “left” the company.
Pseudoadmin local spill
According to our data , about 50% of all internal information security incidents are precisely leaks of confidential information. It must be said, for our many years of practice, we have encountered a huge number of internal violations. Often their identification is actually a search for a needle in a haystack: in the conditions of a small number of information sources, many routine tasks have to be solved, while in UTM, the web traffic filtering module helps to deal with leaks. So you can identify and / or block access to file hosting.
At one of our customers, administrators were allowed to use file hosting services, but the rest of the employees were not. When compiling the report, we drew attention to the fact that one of the administrators uploads much more information to external resources than the rest. We informed the customer - this fact surprised him a lot. The administrator claimed that he had not used file sharing at all this month.

They began to analyze the UTM logs and saw that under the administrator account authentication from two different hosts takes place. One of the users stole the administrator password and unloaded data sensitive for the organization without restrictions. It was not difficult to calculate the user: he logged in as the administrator and under his own from the same host.
Under the supervision of Solar JSOC
So yes, it would be foolish to abandon existing developments, therefore, the EPSC platform makes the most of the experience and knowledge of our SOC - for example, in terms of collecting and aggregating information on threats. It helps a lot to detect and prevent various incidents.
So, at the stage of a pilot connection with one of the customers, thanks to our database of compromise indicators accumulated during the investigation, we found that some hosts access IP addresses that belong to the hacker group Cobalt.

We studied these hosts — it turned out that for more than a year (just that!), Antivirus signatures were not updated and the machines were infected with a trojan. Fortunately, this was not a bank, so the company was saved only by the fact that they were banal to intruders.
Another company came to us to pilot because of problems with its firewall. Every two days he “fell” without declaring war. The customer could not identify the exact problem - he suggested that the blame was on the volume of traffic. But, since there is no money for a new firewall, we decided to consider the option of switching to a service model.
In the first 10 minutes after connecting to our platform, we saw an interesting and at the same time terrible picture: the four hosts of the organization scan the entire Internet at 445, 22, 3389 ports, and they are also accessing well-known C & C servers.

The customer was immediately notified, the hosts were blocked. In the course of the proceedings, it turned out that they belong to the contractor’s specialists who carry out some work on the customer’s site and use their personal laptops infected with a wide variety of malware. If an attack occurred from the customer’s public IP addresses, this would be, to put it mildly, a strong reputation blow.
Artyom Kildyushev, a group of expert presales for Solar JSOC products and services
All Articles