WIBAttack. Is the new SIM card vulnerability terrible?

[According to public information], on September 21, Ginno Security Lab published information about a vulnerability similar to Simjacker, which allows using one malicious SMS to take control of the mobile functions of the attacked device and thereby be able to send SMS, make calls, and find out information about IMEI and geolocation. The main problem is that the vulnerability is detected in the software of the SIM cards themselves and does not depend directly on the device. Any exploitation by an attacker will be invisible to the owner, since the interaction will be carried out directly with the WIB.
The vulnerable is SmartTrust's Wireless Internet Browser (WIB), which is used by the vast majority of carriers.
The scale claimed by the researchers is scary ... but let's try to figure out whether it is so new and so dangerous.
Wireless Internet Browser (WIB)
This software is used to provide users with a dynamic menu of SIM card functions. For example, when a person tries to request a balance from a mobile operator from the SIM toolkit. In fact, it’s a “wired” WAP browser, yes, that same good old web browser of our youth with WML (English Wireless Markup Language - “Markup Language for Wireless Devices”), working on OTA SMS (Over-the-air) .
OTA is a technology with a client-server architecture that allows the operator’s gateway to remotely control SIM card data by receiving special messages for downloading, activating services on a mobile device (for example, your horoscope subscription, debiting 100500 money per month). In this case, you need an Internet connection: Wi-Fi, 3G, LTE, etc.
The OTA-gateway of the operator through the Short Message Service Center (SMSC) sends service SMS to one or more devices.
The device interacts with the SIM card through the telephone processor operating system (RTOS, Baseband processor realtime operating system).
And yes, your phone has a second OS that has a higher priority mode of operation than Android / iOS.
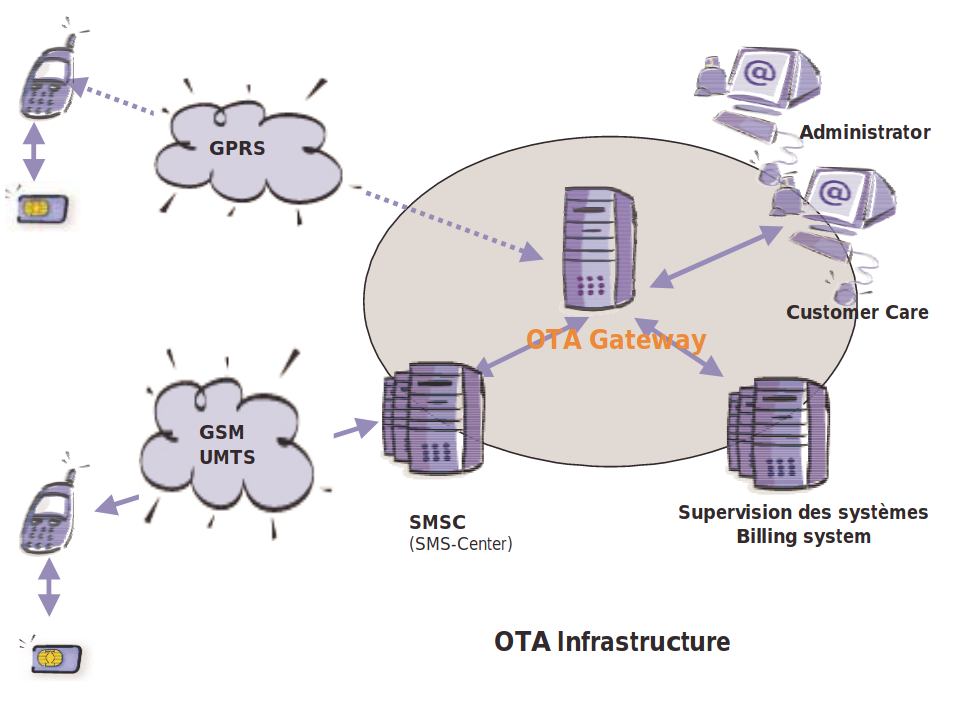
OTA Infrastructure
OTA Security Implementation
The OTA SMS protection level during transmission is determined by the first byte of the message (MSL header with a bit mask of active security mechanisms: encryption, counters, checksums). When the SIM card receives OTA SMS, the MSL from SMS (MSLsms) is compared with the MSL specified in the SIM card itself (MSLsim). If the value MSLsim> MSLsms, then the SIM card ignores OTA commands.
At the same time, different MSL headers can be set for different service applications of the SIM card. The target application is identified by the code in the TAR header (3-byte Toolkit Application Reference).
More details can be found here: 3GPP TS 23.048
Attack

Attack on WIB
- To exploit the vulnerability, an attacker must send a malicious OTA SMS.
- After receiving an SMS, the device will execute the APDU (application protocol data unit) ENVELOP COMMAND command to transfer the received TPDU (Transport Protocol Data Unit) from SMS from RTOS to the SIM card’s WIB browser. It is precisely because this procedure will occur at the RTOS level that the victim will not notice any activity.
- The WIB browser will execute the commands received in the TPDU and send the corresponding PROACTIVE COMMAND command to the device, for example, SETUP CALL, SEND SMS, PROVIDE LOCATION INFO.
- The device, following the command received from the SIM card, will perform the corresponding action.
OTA Vulnerability Conditions
So we got to the most interesting.
Below are a few conditions under which an attack is possible (any of):
- The MSL header of the SIM card or the target application is 0 or without activating KIc / KID encryption properties.
- If possible, rooting simcard: some SIM cards are used for KIc / KID DES keys, hacking of which was demonstrated by Dr. Karsten Nohl (Security Research Lab Berlin) at BlackHat 2013. Using rainbow tables, hacking takes about 2 minutes. With the key obtained, an attacker can sign an SMS. According to Nohl, about 750 million SIM cards for 2015 are affected by such vulnerabilities. You can read in more detail and interestingly:
SIM Cards Encryption Vulnerability: The Scope of the Problem | Kaspersky official blog
Rooting SIM cards, BlackHat 2013 - Cases of data leakage leading to the compromise of KIc / KID keys were previously known.
Summing up ... "is the devil so terrible?"
Despite the frightening statements, the vulnerability boils down to the use of weak encryption, leaks of corporate information and misconfiguration of security settings.
Also, the contribution of the Ginno Security Lab researchers is not entirely clear, even with the caveat that they knew about the vulnerability in 2015. Moreover, this vector was essentially considered by Karsten Nohl in 2013.
It is difficult to give a real estimate of the number of vulnerable devices at the moment. Judging by the comments on the topic A brief introduction to SIM-cards / Habr , our operators can do everything quite well: A brief introduction to SIM-cards / Comments .
PS In 2013, there was already a hype about the vulnerabilities found by Karsten. And also everything was full of news about the impending apocalypse. But like the apocalypse of 2012 ...

All Articles