Training Cisco 200-125 CCNA v3.0. Day 32. Password Recovery, XMODEM / TFTPDNLD and Cisco License Activation
Today we’ll talk about restoring passwords for routers and switches, updating, reinstalling, and recovering IOS and about the Cisco licensing system for the IOSv15 operating system. These are very important topics regarding network device management.

How can I recover my password? You may ask why this might be necessary. Suppose you configured the device and set all the necessary passwords: on VTY, on the console, on privileged mode, on Telnet and SSH connections, and then forgot these passwords. It is possible that the company employee who installed them quit and didn’t give you the notes, or you bought an eBay router and don’t know the passwords that the former owner set, so you can’t access the device.
In such situations, “hacker” tricks should be used. You crack a Cisco device and reset passwords, but this is not a real hack if the device belongs to you. Three things are needed for this: Break Break sequence, configuration register, and system reboot.
You use the switch, turn off the power of the router and then turn it on so that the router starts to reboot, “cisco-guides” call it the word “bouncing”. At the time of unpacking the IOS image, you need to apply a boot interrupt, that is, connect to the device through the console port and run Break Sequence. The key combination that Break Sequence launches depends on the terminal emulation program that you use, that is, for Hyperterminal, the download is interrupted by one combination, for SequreSRT by the other. Under this video, I provide the link www.cisco.com/c/en/us/support/docs/routers/10000-series-routers/12818-61.html , where you can see all the keyboard shortcuts for different terminal emulators, different compatibility and different operating systems.
When using boot interrupt, the router will start in ROMmon mode. ROMmon is similar to the BIOS of a computer, it is an elementary basic OS that allows you to execute basic service commands. In this mode, you can use the configuration register. As you know, during the boot process, the system checks for boot settings, and if they are not, it loads with the default settings.
Normally, the value of the router configuration register is 0x2102, which means starting the boot configuration. If you change this value to 0x2142, then during Break Sequence the boot configuration will be ignored, since the system will not pay attention to the contents of the non-volatile NVRAM and the default configuration will be loaded, which corresponds to the settings of the router “out of the box”.
Thus, to boot with the default settings, you need to change the value of the configuration register to 0x2142, which literally tells the device: “please ignore the boot configuration at any boot!”. Since this configuration contains all passwords, booting with the default settings, you get free access to privileged mode. In this mode, you can reset passwords, save changes, reboot the system and get full control over the device.
Now I will launch Packet Tracer and show what I just talked about. You see the network topology, consisting of a router in which you need to reset the passwords, switch and laptop. In all the video tutorials, I clicked on the device icon in Packet Tracer, went to the CLI console tab and configured the device. Now I want to do something different and show how this is done on a real device.
I will connect the serial port of the RS-232 laptop with a console cable to the console port of the router, in the program it is a blue cable. I do not need to configure any IP addresses, because they are not needed to communicate with the console port of the router.
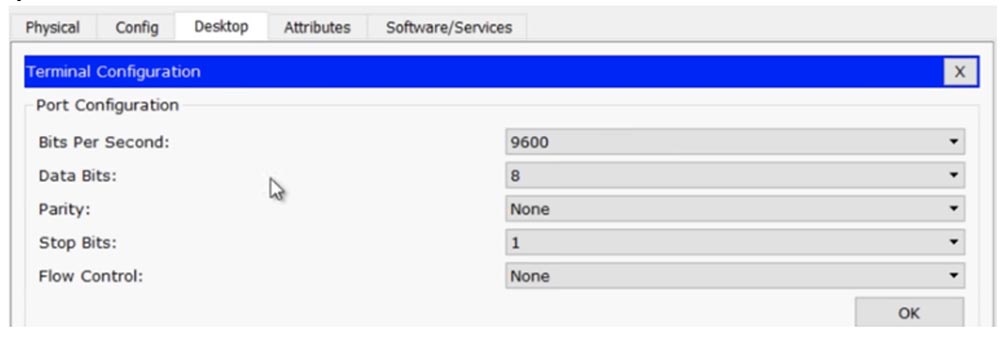
In the laptop, I go to the Terminal tab and check the parameters: transmission speed 9600 bps, information bits - 8, no parity, stop bits - 1, flow control - no, and then click OK, which gives me access to the router console. If you compare the information in both windows - the CLI of the R0 router and on the laptop Screen Laptop0, it will be exactly the same.
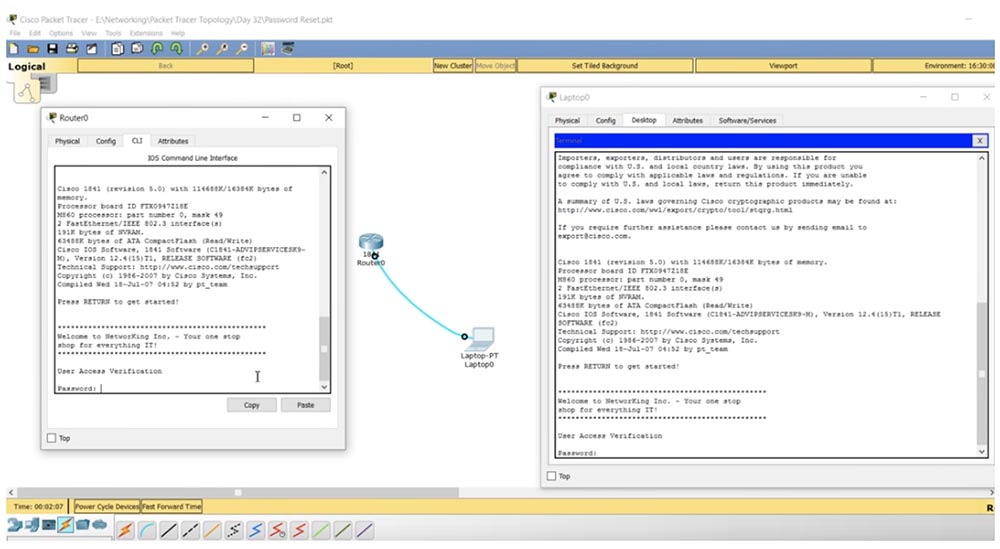
Packet Tracer allows you to do such things, but in practice we will not use the console window of the CLI router, but will only work through the computer terminal.
So, we have a router on which it is necessary to reset the password. You go to the laptop terminal, check the settings, go to the router settings panel and see that access is blocked by a password! How to get there?
I go to the router, to the tab where it is shown as a physical device, click on the power switch and immediately turn it on again. You see that a message appeared in the terminal window about the self-extracting of the OS image. At this point, you should use the key combination Ctrl + C, it is used to switch to rommon mode in the Packet Tracer program. If you are logged in through Hyperterminal, you need to press Ctrl + Break.
You see that a line with the heading rommon 1 appeared on the screen, and if you enter a question mark, then the system will give a series of prompts which commands can be used in this mode.
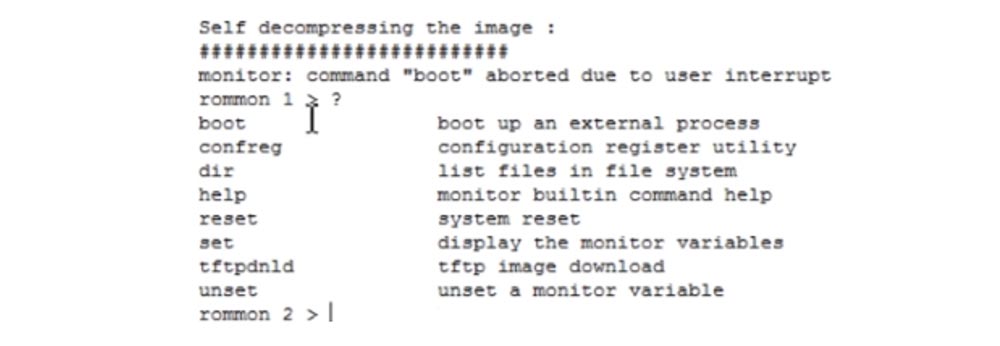
The boot parameter starts the internal boot process, confreg launches the register configuration utility, and we are interested in this particular command. I type in the terminal line confreg 0x2142. This means that upon rebooting, the information stored in the NVRAM flash memory will be ignored and the router will boot with the default settings, like a completely new device. If I typed the confreg 0x2102 command, the router would use the last saved boot parameters.
Next, with the reset command, I reboot the system. As you can see, after downloading it, instead of prompting you to enter a password, as last time, the system simply asks if I intend to continue the configuration dialog. Now we have a router with default settings, without any user configuration.

I enter no, then enter, and switch from user mode to privileged mode. Since I want to view the boot configuration, I use the show startup-config command. You see the host name of the NwKing router, the welcome banner, and the password for the console. Now I know this password and can copy it so as not to forget, or I can change it to another.
What I need first of all is to load the launch configuration into the current router configuration. To do this, I use the copy startup-config running-config command. Now our current configuration was the previous configuration of the router. You see that after that the name of the router on the command line has changed from Router to NwKingRouter. Using the show run command, you can view the current configuration of the device, where it can be seen that the password for the console is the word “console”, we did not use enable password, this is correct. You need to remember that recovery “kills” privileged mode and you again find yourself in user-mode command line.
We can still make changes to the registry, and if the password were secret, that is, the enable secret function would be used, obviously you could not decrypt it, so you can return to global configuration mode with the config t command and set a new password. To do this, I type the command enable secret enable or I can use any other word as a password. If you type show run, you will see that the enable secret function is turned on, the password now does not look like the word “enable”, but as a string of encrypted characters and you can not worry about security, because you just set and encrypt the new password.

Here's how to reset your router password. Pay attention to one important thing: if you enter the show version command, show version, you will see that the value of the configuration register is 0x2142. This means that even if I use the copy running to startup command and reboot the router, the system will load the default settings again, that is, the router will return to the factory settings. We do not need this at all, because we reset the password, got control over the device and want to use it in working mode.
Therefore, you need to enter the global configuration mode Router (config) # and enter the config-register 0x2102 command and only after that use the command to copy the current configuration to the copy run start download. You can also copy the current settings to the boot configuration using the write command. If you now type show version, you will see that the value of the configuration register is now 0x2102, and the system reports that the changes will take effect the next time the router is rebooted.
Therefore, we initiate a reboot with the reload command, the system reboots, and now we have all the configuration files, all the settings, and we know all the passwords. This is how the router password recovery is performed.
Let's look at how to implement the same procedure for the switch. The router has a switch that allows you to turn the power off and on again, but the Cisco switch does not have such a switch. We must connect to the console port with a console cable, then disconnect the power cable from the back of the switch, after 10-15 seconds insert it back and immediately press and hold the MODE button for 3 seconds. This will automatically switch the switch to ROMmon mode. In this mode, you must initialize the file system on a flash and rename the config.text file, for example, to config.text.old. If you simply delete it, the switch will “forget” not only passwords, but also all previous settings. After that, you overload the system.

What happens to the switch? At the time of reboot, it refers to the config.text configuration file. If it does not find this file in the device’s flash memory, it loads iOS with the default settings. This is the difference: in the router, you must change the register settings, and in the switch, just change the name of the boot settings file. Let's see how this happens in the Packet Tracer program. This time I connect the laptop with a console cable to the console port of the switch.
We do not use the CLI switch console, but simulate a situation where the switch settings can be reached only using a laptop. I use the same settings for the laptop terminal as in the case of the router, and by pressing “Enter”, I connect to the console port of the switch.
In Packet Tracer, I cannot disconnect and turn on the power cable, as is the case with a physical device. If I had a password for the console, I could reload the switch, so I enter the enable password enable command to set the local access password to privileged console mode.
Now if I go into the settings, I will see that the system asks for a password that I do not know. So, you need to initiate a system reboot. As you can see, the system does not accept the reload command that came from the user's device in user mode, so I have to use privileged mode. As I said, in real life, I would just unplug the switch’s power cable for a few seconds to cause a reboot, but since this is not possible in the program, I must delete the password and reboot right from here. You understand why I'm doing this, right?
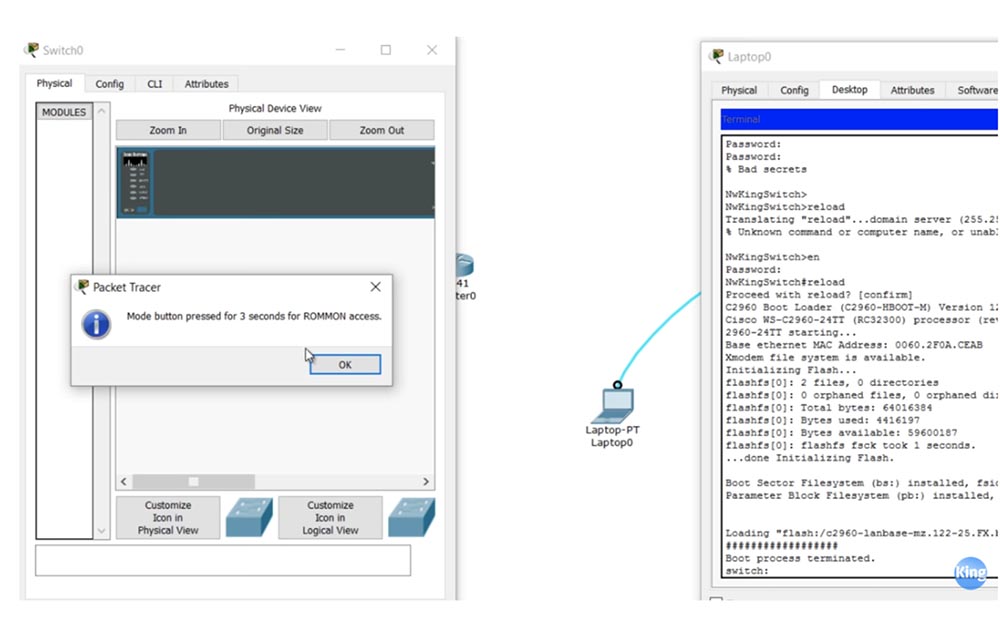
So, I switch from the CLI tab to the “Physical device” tab, and when the device starts rebooting, I hold the virtual MODE button for 3 seconds and go into ROMmon mode. You see that the information in the switch CLI window is the same as in the window on the laptop screen. I go to the laptop, in the window of which the ROMmon switch mode is displayed, and enter the flash_init command. This command initializes the file system to flash, after which I enter the dir_flash command to view the contents of the flash memory.
Two files are located here - the IOS file with the extension .bin and the config.text file, which we must rename. To do this, I use the rename flash: config.text flash: config.old command. If you now use the dir_flash command, you can see that the config.text file has been renamed to config.old.

Now I enter the reset command, the switch reboots and after booting the system goes to the default settings. This is evidenced by a change in the device name on the command line from NwKingSwitch to just Switch. The rename command exists in a real device, but it cannot be used in Packet Tracer. Therefore, I use show running conf, as you can see, the switch uses all the default settings, and I enter the more flash: config.old command. Here's the hack: you just have to copy the current device configuration displayed on the screen, go into global configuration mode and paste the copied information. Ideally, absolutely all settings are copied from us, and you see that the device name has changed and the switch has switched to normal operation mode.
Now it remains to copy the current configuration to the boot configuration, that is, create a new config.text file. The easiest way is to simply rename the old file back to config.text, i.e. copy the contents of config.old to the current configuration and then save it as config.text. This is how the switch password is restored.
Now we’ll look at how to back up and restore the Cisco IOS operating system. Backing up is copying the IOS image to the TFTP server. Next I will tell you how to transfer the system image file from this server to your device. The third topic is system recovery in ROMmon mode. This may be necessary if your colleague accidentally deleted iOS and the system stopped loading.

We will look at how to get a system file from a TFTP server in ROMmod mode. There are 2 ways to do this, one of them is xmodem. Packet Tracer does not support xmodem, so I’ll briefly describe what it is and then show with Packet Tracer how the second method is used - system recovery via TFTP.
The diagram shows the device Router0, which is assigned an IP address 10.1.1.1. This router is connected to a server with an IP address of 10.1.1.10. I forgot to assign an address to the router, so now I will do it quickly. Our router is not connected to the laptop, so the program does not allow you to use the CLI console, and I will have to fix it.
I connect the laptop to the router with a console cable, the system asks for the password for the console, and I use the word console. In global configuration mode, I assign the appropriate IP address and subnet mask 255.255.255.0 to the f0 / 0 interface and add the no shutdown command.
Next, I type the show flash command and see that there are 3 files in memory. The file number 3 is the most important, this is the file of the iOS router. Now I need to configure the TFTP server, so I click on the Server0 device icon and open the SERVICES tab. We see that the TFTP server is turned on and it contains files of many Cisco operating systems, including IOS for our c1841 router - this is the third order file in the list. I need to remove it from the server, because I'm going to copy another IOS file here from our router Router0. To do this, I select the file and click Remove file, and then go to the console tab of the laptop.

From the console of the router, I enter the command copy flash tftp <source file name> <destination address / host name>, then copy and paste the operating system file name.

Next, in the command, you need to specify the address or name of the remote host to which this file should be copied. Just as when saving the boot configuration of the router, you need to be careful here. If you mistakenly copy not the current configuration to the boot, but rather the boot to the current, then after rebooting the device, lose all the settings made. Similarly, in this case, the source and destination should not be confused. So, first we indicate the name of the file to be copied to the server, and then the IP address of this server is 10.1.1.10.

You see that the file transfer has begun, and if you look at the list of TFTP files, you can see that instead of the deleted file, a new IOS file of our router appeared here. This is how IOS is copied to the server.
Now we return to the router settings window on the laptop screen and enter the copy tftp flash command, specify the address of the remote host 10.1.1.10 and the source file name Source filename, that is, the IOS that you want to copy to the router’s flash: c1841-ipbase-mz.123 -14.T7.bin. The following is the name of the destination file Destination filename, which in our case will be exactly the same as the source name. After that, I press Enter, and the new IOS file is copied to the flash memory of the router. You see, we now have two operating system files: the new one at number 3 and the previous original at number 4.
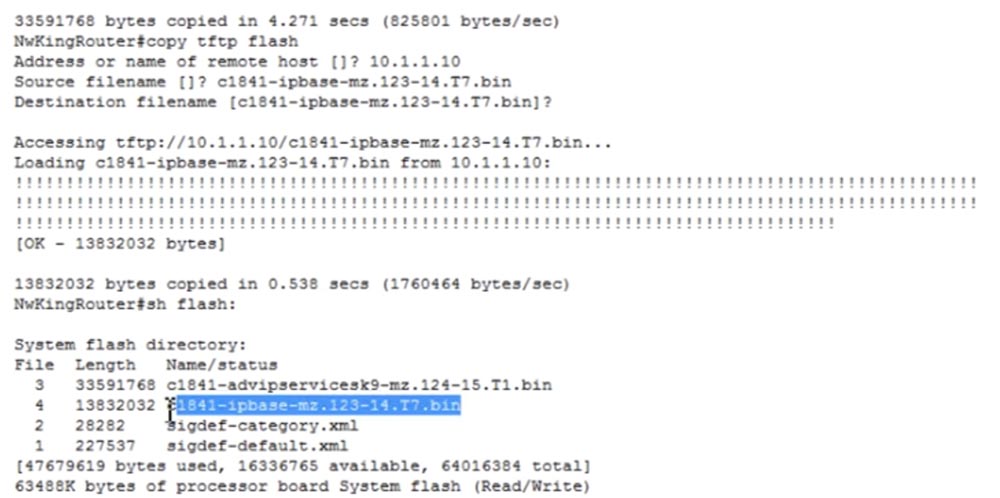
In the IOS designation, the version is important for us - in the first file at number 3 it is 124, and in the second at number 4 it is 123, that is, the older version. In addition, advipservicesk9 indicates that this version of the system is more functional than ipbase, as it allows the use of MPLS and the like.
Another scenario is that you mistakenly deleted the flash - I type the delete flash command and specify the name of the IOS file to be deleted.
But before that, I want to say that now, by default, the system file number 3 will be used during boot, that is, c1841- advipservicesk9-mz.124-15.T1.bin. Suppose, for some reason, I want the next file to use file number 4 - c1841-ipbase-mz.123-14.T7.bin. To do this, I go into global configuration mode and type the boot system flash command: c1841-ipbase-mz.123-14.T7.bin.
Now, at the next boot, this file will be used as the default OS, even if we have two operating systems stored in flash.
Let's go back to uninstalling the OS and type the delete flash command: c1841-ipbase-mz.123-14.T7.bin. After that, delete the second OS with the delete flash command: c1841-advipservicesk9-mz.124-15.T1.bin, so that the router will lose both operating systems.
If you type show flash now, you can see that now we don’t have any OS at all. What will happen if I give a reboot command? You see that after entering the reload command, the device immediately enters ROMmon mode. As I said, when booting, the device searches for the OS file and, if it is absent, switches to the base rommon OS.
Packet Tracer xmodem, . xmodem . SecureCRT, , , , xmodem. , xmodem, . , , xmodem, . xmodem , 1-2 .
TFTP- . , Packet Tracer xmodem, tftp tftpdnld, , TFTP-. , . ? , rommon IOS. IP- , IP_ADDRESS=10.1.1.1, IP_SUBNET_MASK=255.255.255.0, DEFAULT_GATEWAY=10.1.1.10, TFTP_SERVER=10.1.1.10 TFTP_FILE= 1841- advipservicesk9-mz.124-15.T1.bin.
, , tftpdnld, , . «», , - , .

, , boot, . , , . , .
Cisco IOS.
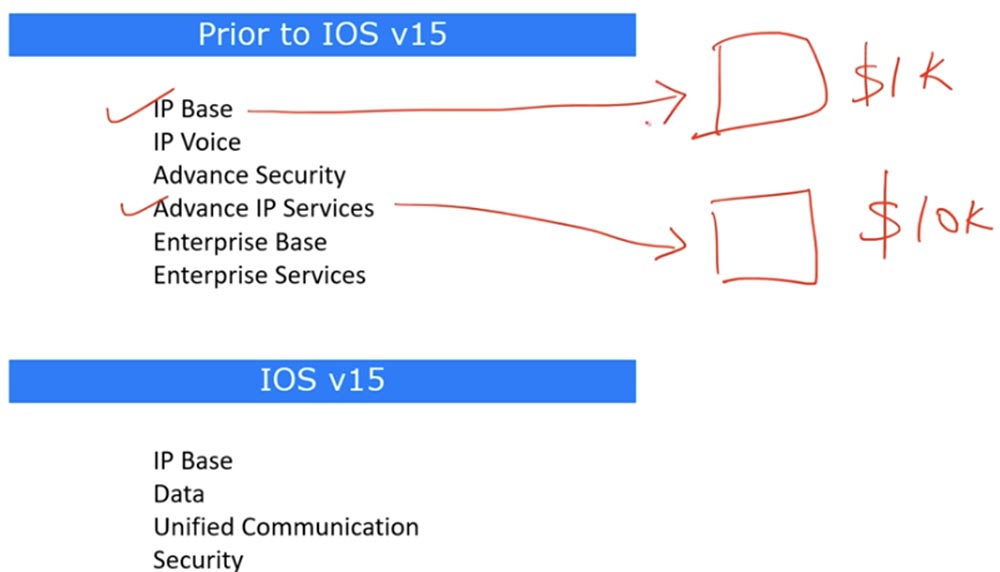
15 , 12, 15 , , 13 14. , Cisco, IOS IP Base , , 1000$. «» .
, , Advance IP Services, , , 10 . , . , . , «» 9 . , . , , . Cisco , , IOS 15, .
IOS, , 12.4, , , . , Windows Home, Windows Professional, Windows Enterprise ..
15 – Cisco IOSv15, . , .
IP Base , , Cisco. , Data, Unified Communication Seurity, . Data, , , Cisco . - TFTP , Data . , , IPSec, VPN, ., Security.
Packet Tracer , . CLI show version. , 15.1, , . , .

, ipbase , security data , .
You can use the show license all command to view detailed license information. In addition, you can view the details of a valid license using the show license detail command. License functions can be viewed using the show license features command. This is a summary of the Cisco licensing system. You go to the company’s website, buy the necessary license, and insert the license file into the system. This can be done in global configuration mode using the license install command.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

How can I recover my password? You may ask why this might be necessary. Suppose you configured the device and set all the necessary passwords: on VTY, on the console, on privileged mode, on Telnet and SSH connections, and then forgot these passwords. It is possible that the company employee who installed them quit and didn’t give you the notes, or you bought an eBay router and don’t know the passwords that the former owner set, so you can’t access the device.
In such situations, “hacker” tricks should be used. You crack a Cisco device and reset passwords, but this is not a real hack if the device belongs to you. Three things are needed for this: Break Break sequence, configuration register, and system reboot.
You use the switch, turn off the power of the router and then turn it on so that the router starts to reboot, “cisco-guides” call it the word “bouncing”. At the time of unpacking the IOS image, you need to apply a boot interrupt, that is, connect to the device through the console port and run Break Sequence. The key combination that Break Sequence launches depends on the terminal emulation program that you use, that is, for Hyperterminal, the download is interrupted by one combination, for SequreSRT by the other. Under this video, I provide the link www.cisco.com/c/en/us/support/docs/routers/10000-series-routers/12818-61.html , where you can see all the keyboard shortcuts for different terminal emulators, different compatibility and different operating systems.
When using boot interrupt, the router will start in ROMmon mode. ROMmon is similar to the BIOS of a computer, it is an elementary basic OS that allows you to execute basic service commands. In this mode, you can use the configuration register. As you know, during the boot process, the system checks for boot settings, and if they are not, it loads with the default settings.
Normally, the value of the router configuration register is 0x2102, which means starting the boot configuration. If you change this value to 0x2142, then during Break Sequence the boot configuration will be ignored, since the system will not pay attention to the contents of the non-volatile NVRAM and the default configuration will be loaded, which corresponds to the settings of the router “out of the box”.
Thus, to boot with the default settings, you need to change the value of the configuration register to 0x2142, which literally tells the device: “please ignore the boot configuration at any boot!”. Since this configuration contains all passwords, booting with the default settings, you get free access to privileged mode. In this mode, you can reset passwords, save changes, reboot the system and get full control over the device.
Now I will launch Packet Tracer and show what I just talked about. You see the network topology, consisting of a router in which you need to reset the passwords, switch and laptop. In all the video tutorials, I clicked on the device icon in Packet Tracer, went to the CLI console tab and configured the device. Now I want to do something different and show how this is done on a real device.
I will connect the serial port of the RS-232 laptop with a console cable to the console port of the router, in the program it is a blue cable. I do not need to configure any IP addresses, because they are not needed to communicate with the console port of the router.

In the laptop, I go to the Terminal tab and check the parameters: transmission speed 9600 bps, information bits - 8, no parity, stop bits - 1, flow control - no, and then click OK, which gives me access to the router console. If you compare the information in both windows - the CLI of the R0 router and on the laptop Screen Laptop0, it will be exactly the same.

Packet Tracer allows you to do such things, but in practice we will not use the console window of the CLI router, but will only work through the computer terminal.
So, we have a router on which it is necessary to reset the password. You go to the laptop terminal, check the settings, go to the router settings panel and see that access is blocked by a password! How to get there?
I go to the router, to the tab where it is shown as a physical device, click on the power switch and immediately turn it on again. You see that a message appeared in the terminal window about the self-extracting of the OS image. At this point, you should use the key combination Ctrl + C, it is used to switch to rommon mode in the Packet Tracer program. If you are logged in through Hyperterminal, you need to press Ctrl + Break.
You see that a line with the heading rommon 1 appeared on the screen, and if you enter a question mark, then the system will give a series of prompts which commands can be used in this mode.

The boot parameter starts the internal boot process, confreg launches the register configuration utility, and we are interested in this particular command. I type in the terminal line confreg 0x2142. This means that upon rebooting, the information stored in the NVRAM flash memory will be ignored and the router will boot with the default settings, like a completely new device. If I typed the confreg 0x2102 command, the router would use the last saved boot parameters.
Next, with the reset command, I reboot the system. As you can see, after downloading it, instead of prompting you to enter a password, as last time, the system simply asks if I intend to continue the configuration dialog. Now we have a router with default settings, without any user configuration.

I enter no, then enter, and switch from user mode to privileged mode. Since I want to view the boot configuration, I use the show startup-config command. You see the host name of the NwKing router, the welcome banner, and the password for the console. Now I know this password and can copy it so as not to forget, or I can change it to another.
What I need first of all is to load the launch configuration into the current router configuration. To do this, I use the copy startup-config running-config command. Now our current configuration was the previous configuration of the router. You see that after that the name of the router on the command line has changed from Router to NwKingRouter. Using the show run command, you can view the current configuration of the device, where it can be seen that the password for the console is the word “console”, we did not use enable password, this is correct. You need to remember that recovery “kills” privileged mode and you again find yourself in user-mode command line.
We can still make changes to the registry, and if the password were secret, that is, the enable secret function would be used, obviously you could not decrypt it, so you can return to global configuration mode with the config t command and set a new password. To do this, I type the command enable secret enable or I can use any other word as a password. If you type show run, you will see that the enable secret function is turned on, the password now does not look like the word “enable”, but as a string of encrypted characters and you can not worry about security, because you just set and encrypt the new password.

Here's how to reset your router password. Pay attention to one important thing: if you enter the show version command, show version, you will see that the value of the configuration register is 0x2142. This means that even if I use the copy running to startup command and reboot the router, the system will load the default settings again, that is, the router will return to the factory settings. We do not need this at all, because we reset the password, got control over the device and want to use it in working mode.
Therefore, you need to enter the global configuration mode Router (config) # and enter the config-register 0x2102 command and only after that use the command to copy the current configuration to the copy run start download. You can also copy the current settings to the boot configuration using the write command. If you now type show version, you will see that the value of the configuration register is now 0x2102, and the system reports that the changes will take effect the next time the router is rebooted.
Therefore, we initiate a reboot with the reload command, the system reboots, and now we have all the configuration files, all the settings, and we know all the passwords. This is how the router password recovery is performed.
Let's look at how to implement the same procedure for the switch. The router has a switch that allows you to turn the power off and on again, but the Cisco switch does not have such a switch. We must connect to the console port with a console cable, then disconnect the power cable from the back of the switch, after 10-15 seconds insert it back and immediately press and hold the MODE button for 3 seconds. This will automatically switch the switch to ROMmon mode. In this mode, you must initialize the file system on a flash and rename the config.text file, for example, to config.text.old. If you simply delete it, the switch will “forget” not only passwords, but also all previous settings. After that, you overload the system.

What happens to the switch? At the time of reboot, it refers to the config.text configuration file. If it does not find this file in the device’s flash memory, it loads iOS with the default settings. This is the difference: in the router, you must change the register settings, and in the switch, just change the name of the boot settings file. Let's see how this happens in the Packet Tracer program. This time I connect the laptop with a console cable to the console port of the switch.
We do not use the CLI switch console, but simulate a situation where the switch settings can be reached only using a laptop. I use the same settings for the laptop terminal as in the case of the router, and by pressing “Enter”, I connect to the console port of the switch.
In Packet Tracer, I cannot disconnect and turn on the power cable, as is the case with a physical device. If I had a password for the console, I could reload the switch, so I enter the enable password enable command to set the local access password to privileged console mode.
Now if I go into the settings, I will see that the system asks for a password that I do not know. So, you need to initiate a system reboot. As you can see, the system does not accept the reload command that came from the user's device in user mode, so I have to use privileged mode. As I said, in real life, I would just unplug the switch’s power cable for a few seconds to cause a reboot, but since this is not possible in the program, I must delete the password and reboot right from here. You understand why I'm doing this, right?

So, I switch from the CLI tab to the “Physical device” tab, and when the device starts rebooting, I hold the virtual MODE button for 3 seconds and go into ROMmon mode. You see that the information in the switch CLI window is the same as in the window on the laptop screen. I go to the laptop, in the window of which the ROMmon switch mode is displayed, and enter the flash_init command. This command initializes the file system to flash, after which I enter the dir_flash command to view the contents of the flash memory.
Two files are located here - the IOS file with the extension .bin and the config.text file, which we must rename. To do this, I use the rename flash: config.text flash: config.old command. If you now use the dir_flash command, you can see that the config.text file has been renamed to config.old.

Now I enter the reset command, the switch reboots and after booting the system goes to the default settings. This is evidenced by a change in the device name on the command line from NwKingSwitch to just Switch. The rename command exists in a real device, but it cannot be used in Packet Tracer. Therefore, I use show running conf, as you can see, the switch uses all the default settings, and I enter the more flash: config.old command. Here's the hack: you just have to copy the current device configuration displayed on the screen, go into global configuration mode and paste the copied information. Ideally, absolutely all settings are copied from us, and you see that the device name has changed and the switch has switched to normal operation mode.
Now it remains to copy the current configuration to the boot configuration, that is, create a new config.text file. The easiest way is to simply rename the old file back to config.text, i.e. copy the contents of config.old to the current configuration and then save it as config.text. This is how the switch password is restored.
Now we’ll look at how to back up and restore the Cisco IOS operating system. Backing up is copying the IOS image to the TFTP server. Next I will tell you how to transfer the system image file from this server to your device. The third topic is system recovery in ROMmon mode. This may be necessary if your colleague accidentally deleted iOS and the system stopped loading.

We will look at how to get a system file from a TFTP server in ROMmod mode. There are 2 ways to do this, one of them is xmodem. Packet Tracer does not support xmodem, so I’ll briefly describe what it is and then show with Packet Tracer how the second method is used - system recovery via TFTP.
The diagram shows the device Router0, which is assigned an IP address 10.1.1.1. This router is connected to a server with an IP address of 10.1.1.10. I forgot to assign an address to the router, so now I will do it quickly. Our router is not connected to the laptop, so the program does not allow you to use the CLI console, and I will have to fix it.
I connect the laptop to the router with a console cable, the system asks for the password for the console, and I use the word console. In global configuration mode, I assign the appropriate IP address and subnet mask 255.255.255.0 to the f0 / 0 interface and add the no shutdown command.
Next, I type the show flash command and see that there are 3 files in memory. The file number 3 is the most important, this is the file of the iOS router. Now I need to configure the TFTP server, so I click on the Server0 device icon and open the SERVICES tab. We see that the TFTP server is turned on and it contains files of many Cisco operating systems, including IOS for our c1841 router - this is the third order file in the list. I need to remove it from the server, because I'm going to copy another IOS file here from our router Router0. To do this, I select the file and click Remove file, and then go to the console tab of the laptop.

From the console of the router, I enter the command copy flash tftp <source file name> <destination address / host name>, then copy and paste the operating system file name.

Next, in the command, you need to specify the address or name of the remote host to which this file should be copied. Just as when saving the boot configuration of the router, you need to be careful here. If you mistakenly copy not the current configuration to the boot, but rather the boot to the current, then after rebooting the device, lose all the settings made. Similarly, in this case, the source and destination should not be confused. So, first we indicate the name of the file to be copied to the server, and then the IP address of this server is 10.1.1.10.

You see that the file transfer has begun, and if you look at the list of TFTP files, you can see that instead of the deleted file, a new IOS file of our router appeared here. This is how IOS is copied to the server.
Now we return to the router settings window on the laptop screen and enter the copy tftp flash command, specify the address of the remote host 10.1.1.10 and the source file name Source filename, that is, the IOS that you want to copy to the router’s flash: c1841-ipbase-mz.123 -14.T7.bin. The following is the name of the destination file Destination filename, which in our case will be exactly the same as the source name. After that, I press Enter, and the new IOS file is copied to the flash memory of the router. You see, we now have two operating system files: the new one at number 3 and the previous original at number 4.

In the IOS designation, the version is important for us - in the first file at number 3 it is 124, and in the second at number 4 it is 123, that is, the older version. In addition, advipservicesk9 indicates that this version of the system is more functional than ipbase, as it allows the use of MPLS and the like.
Another scenario is that you mistakenly deleted the flash - I type the delete flash command and specify the name of the IOS file to be deleted.
But before that, I want to say that now, by default, the system file number 3 will be used during boot, that is, c1841- advipservicesk9-mz.124-15.T1.bin. Suppose, for some reason, I want the next file to use file number 4 - c1841-ipbase-mz.123-14.T7.bin. To do this, I go into global configuration mode and type the boot system flash command: c1841-ipbase-mz.123-14.T7.bin.
Now, at the next boot, this file will be used as the default OS, even if we have two operating systems stored in flash.
Let's go back to uninstalling the OS and type the delete flash command: c1841-ipbase-mz.123-14.T7.bin. After that, delete the second OS with the delete flash command: c1841-advipservicesk9-mz.124-15.T1.bin, so that the router will lose both operating systems.
If you type show flash now, you can see that now we don’t have any OS at all. What will happen if I give a reboot command? You see that after entering the reload command, the device immediately enters ROMmon mode. As I said, when booting, the device searches for the OS file and, if it is absent, switches to the base rommon OS.
Packet Tracer xmodem, . xmodem . SecureCRT, , , , xmodem. , xmodem, . , , xmodem, . xmodem , 1-2 .
TFTP- . , Packet Tracer xmodem, tftp tftpdnld, , TFTP-. , . ? , rommon IOS. IP- , IP_ADDRESS=10.1.1.1, IP_SUBNET_MASK=255.255.255.0, DEFAULT_GATEWAY=10.1.1.10, TFTP_SERVER=10.1.1.10 TFTP_FILE= 1841- advipservicesk9-mz.124-15.T1.bin.
, , tftpdnld, , . «», , - , .

, , boot, . , , . , .
Cisco IOS.

15 , 12, 15 , , 13 14. , Cisco, IOS IP Base , , 1000$. «» .
, , Advance IP Services, , , 10 . , . , . , «» 9 . , . , , . Cisco , , IOS 15, .
IOS, , 12.4, , , . , Windows Home, Windows Professional, Windows Enterprise ..
15 – Cisco IOSv15, . , .
IP Base , , Cisco. , Data, Unified Communication Seurity, . Data, , , Cisco . - TFTP , Data . , , IPSec, VPN, ., Security.
Packet Tracer , . CLI show version. , 15.1, , . , .

, ipbase , security data , .
You can use the show license all command to view detailed license information. In addition, you can view the details of a valid license using the show license detail command. License functions can be viewed using the show license features command. This is a summary of the Cisco licensing system. You go to the company’s website, buy the necessary license, and insert the license file into the system. This can be done in global configuration mode using the license install command.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 - 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB - from $ 99! Read about How to Build Infrastructure Bldg. class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
All Articles