The Adventures of the Elusive Malvari: Versatile Defense (Final Thoughts)

This article is part of the Fileless Malware series. All other parts of the series:
- The Adventures of the Elusive Malvari, Part I
- The Adventures of the Elusive Malvari, Part II: Secret VBA Scripts
- The Adventures of the Elusive Malvari, Part III: Intricate VBA Scripts for Laughter and Profit
- The Adventures of the Elusive Malvari, Part IV: DDE and Word Document Fields
- The Adventures of the Elusive Malvari, Part V: More DDE and COM Scriptlets
- The Adventures of the Elusive Malvari: Multilateral Defense (Final
thoughts) - we are here
I think we can all agree that hackers have a lot of tricks and methods to covertly enter your IT infrastructure and go unnoticed there while they steal your digital assets. The key conclusion of this series is that signature-based malware detection is easily bypassed even by simple approaches, some of which I presented in this series.
I understand very well the security researchers who often call virus scanners useless, but you shouldn’t just throw them away because of this. Still, there are still a lot of malware written by lazy script kiddy hackers that will be blocked by these scanners.
The best ideology in the fight against file-free malware and stealthy exploitation methods is to supplement the standard perimeter protection — port scanners and malware detectors — with secondary lines of defense and have plans for responding and recovering when the inevitable happens, including an attack response program .
I mean the concept of multilateral defense (Defense In-Depth, or DiD) . This is a very practical approach to dealing with advanced hackers who laugh at perimeter security and file signature scanning software.
Does DiD have problems? Of course. The same security professionals who first lost faith in traditional protection measures are now promoting a white list of applications that may be useful to you, especially after the fact of the initial penetration.
As we have seen, the codeless attack methods that I demonstrated earlier in this series can even be used to bypass such a whitelist. This is already falling under the new trend of hacking techniques that undermine faith in legitimate tools and traditional software and use it for their evil purposes.
Stay tuned and stay tuned for future posts.
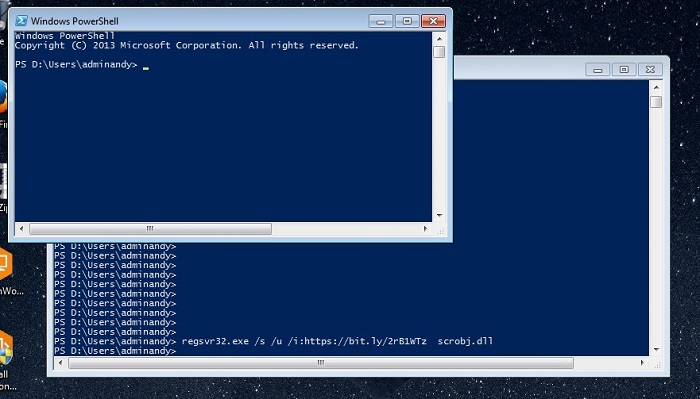
Question: Can you bypass the Windows security features by secretly passing commands to regsvr32.exe? The answer is yes
Serious about data security
In my opinion, in-depth protection is minimization of harm: we take the worst outcome as a maximum and step by step turn it into something that is no longer too scary for us or will cost too much for the attackers.
Imagine that a hacker entered the network, but because of the ideal restrictive permission policies in your company , you prevented him from gaining access to sensitive data. Or hackers got access to confidential data, but your amazing user behavior analysis technology detected intruders and disabled accounts before dumping millions of credit cards was drained. Or maybe the hacker got access to your clients' email addresses, but your operational violation response plan, which includes real-time monitoring of unusual file activity, allowed you to reach regulatory authorities and victims in record time, thereby avoiding fines and anti-advertising .
Common sense protection
Deep defense is, rather, a set of recommendations and a certain philosophy, that is, some practical steps and solutions to make life easier.
If I personally had to describe such an approach to defense and turn it into three effective points, here would be what I would recommend in the first place:
- Assess risks by taking an inventory of what you need to protect. Identify personal and other sensitive data, which is usually scattered throughout the file system. You must find out who works with them and who really needs to have access to them. Caution: this is not so easy to do as it may seem, but if you have the right tools , then you can handle it;
- Protect data. Now that you’ve found the data, limit the potential damage to future violations: reduce too broad and global group-based access, simplify permission structures, and avoid direct user rights. Minimize the overall potential risk by deleting obsolete data and archiving data that is no longer needed actively in the work;
- Maintain a safe state by automating the workflows of providing access, regular verification and certification of rights, as well as data storage based on policies;
- Finally, constantly monitor unusual user and system behavior .
All Articles