W3C implements a standard for storing bank card details in browsers (as passwords)
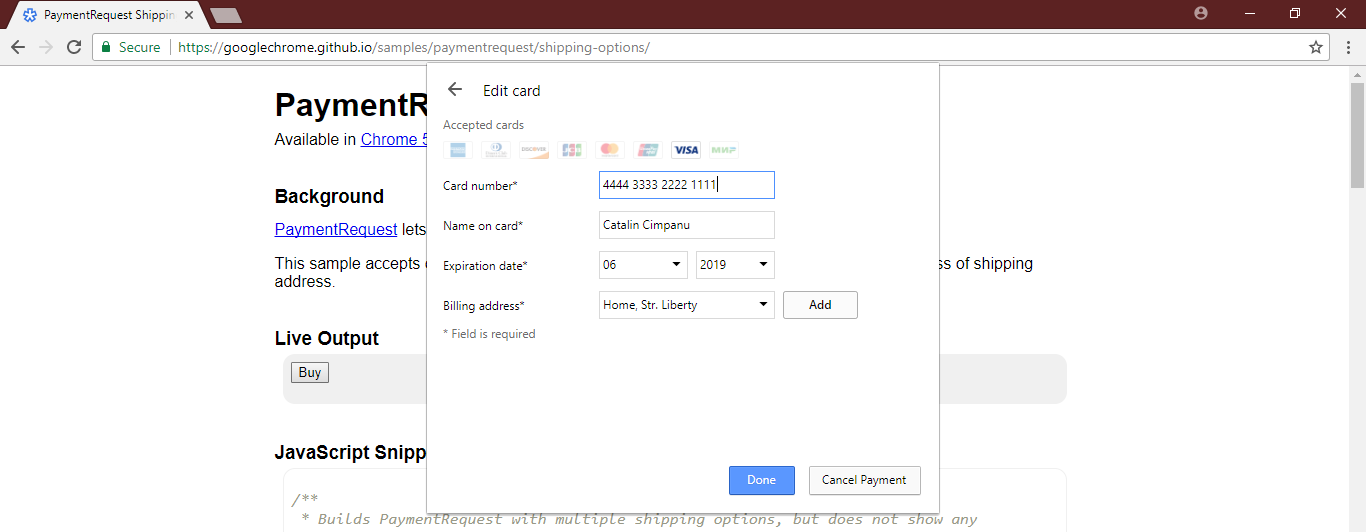
The W3C consortium is gradually bringing the new Payment Request API standard to the final stage, which should make it easier for users to purchase goods from online stores. You no longer have to manually enter your payment data with every purchase, because bank card details are stored in the browser and entered into the form automatically (except for the CVV code).
This is very convenient: payment by card is made literally with a few button presses. Well, fraud schemes will change. If earlier the attackers were looking for databases with credit cards on the servers of the stores, then now the malware will extract the cards directly from the browsers on the users' local machines.
On October 4, a draft Candidate Recommendation was published, comments for which are accepted until October 31, 2017.
Although the Payment Request API standard is not yet fully approved, it is already enabled by default in the following browsers :
- Chrome 61 in the desktop version
- Chrome for Android from version 53
- Chrome for iOS from version 62
- Opera 48
- Opera for Android from version 48
New interfaces are already implemented in the Edge browser , and in Firefox and Safari it is under development. However, to use autopay in Edge, you need to register a Microsoft Wallet account, so in reality not many users have it. Another thing - Chrome, which began to store the details of bank cards the very first among all browsers. In the version for Android, this feature is activated in August 2016, and in the desktop version it was turned on by default in September 2017, with the release of Chrome 61.
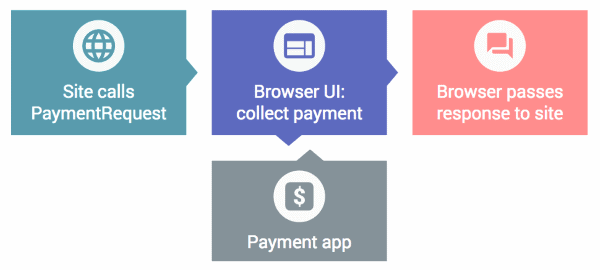
When a user places an order in an online store (clicks the “Buy” button), the store sends an API call to the user's browser, providing order information. The browser displays a pop-up window in which all the fields with payment details and delivery address are already filled in (if they were previously entered and stored in the browser). If the user confirms the information, the browser, rather than the website, contacts a payment operator such as Visa and Mastercard to conduct the transaction. When confirmation is received, the browser reports on the successful execution of the payment to the website of the store that sent the request - and he can proceed to checkout, packaging and sending the goods, knowing that the money has already been transferred to his bank account.
Support for storing bank details in their browser implementations is going to be implemented by Samsung and Facebook, since both companies are extremely interested in simplifying payments on the Internet.
On GitHub open repository with sample code , how to implement on the website different types of automatic payments through the Payment Request API. There is a page with demos . It shows the actual process of payment by the user, examples of client and server code .
At first glance, the scheme with the storage of payment details in the browser seems dangerous. But it was designed just to improve the protection of confidential data. After all, now the store does not receive information about customer card numbers. Accordingly, these databases with cards will no longer be stored in each store, which in the past has repeatedly led to data leaks. Now everything is in the hands of the user - and he himself bears for the safety of his bank cards, which are stored in his personal browser.
There is no need for payment systems like PayPal, which acted as an intermediary. Now such an intermediary will be the technology Payment Payment API and the browser.
Although in many respects the Payment Request API increases the overall security of e-commerce, new risks are emerging. It turns out that the browser knows too much: not only your saved passwords, but also financial information. Having access to the browser, now a stranger can make purchases in stores on your behalf. Moreover, browser developers are tempted to use the purchase history for their own purposes. For example, for accurate targeting of online advertising.
The question is: Do users trust the browser enough to store information about their bank cards in it?
All Articles