Self-made robot on Arduino opens safes bruteforce
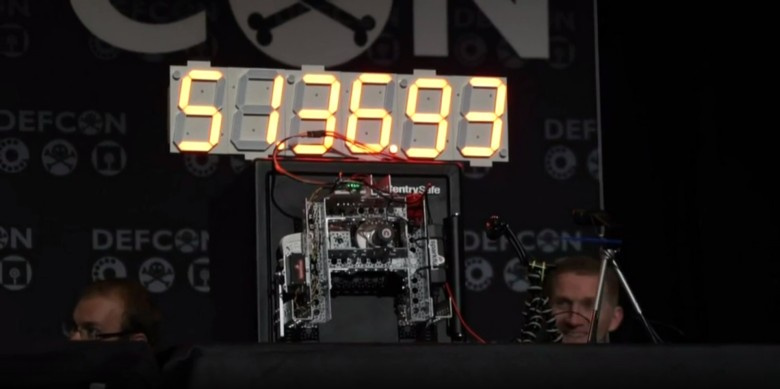
With the help of a cheap robot, a group of hackers right on the DEFCON conference scene opened the safe of one of the well-known manufacturers of safes - SentrySafe. After 30 minutes of buzzing, the robot picked up the right combination 51.36.93 - the door of the safe opened, and the audience of several hundred people exploded with enthusiastic applause .
In the combination lock of this model SentrySafe has a million combinations, that is, 100 × 100 × 100. It would take much longer than half an hour to go through such a number on a mechanical lock. But hackers have found a way to reduce the number of possible combinations, since it turned out that the last number is not at all taken into account when checking the combination. This is due to the fact that the manufacturer was trying to protect against standard methods of hacking the safe. Therefore, on the third code disk, he provided special notches for gripping the rod so that the cracker could not use the method of pushing the rod and listening to the moment when the rod passes into the groove. So, as it turned out, one of the notches, corresponding to the correct number, is about two to three millimeters narrower than the rest. The robot could easily determine it using sensors, taking a couple of simple measurements.
Thus, the number of possible combinations has decreased to 10 thousand (100 × 100). Then the hackers noticed that the design of the safe lock allows some error when entering the code if the person was mistaken for one digit. That is, in each of the three digits it was possible to triple the number of possible combinations. So, the number of possible combinations has decreased to 1000, and this has already been a robot (probably, a person could go through such a number of options in less than a day).
It turned out also that after entering each combination it is not necessary to return the dial of the dial to the starting position. This greatly helps to optimize the operation of the motor, which rotates the handle.
The BBC article says that some models of SentrySafe safes provide additional protection by installing an additional key lock, but the hackers managed to open these models with the Bic knob too.
On YouTube, there are enough videos with the opening of safes with all sorts of clever methods. Honestly, they resemble stories from the book of Richard Feynman "You are, of course, joking, Mr. Feynman!". The famous physicist and Nobel laureate was also fond of opening locks in safes.
In fact, very many safes, even expensive ones, which are claimed to be very safe - are opened very simply. Virtually nowhere is there a delay between attempts to enter a code. Some locks are opened with a magnet, they can be opened with a crowbar or an ax . There are other ways to open safes not in 30 minutes, but in seconds. Locks in such safes can be compared with cheap bicycle locks (that is, almost all bicycle locks).
In an interview with Wired, Nathan Seldle of SparkFun Electronics said that his passion for opening safes began last year when his wife presented him with this model of the SentrySafe safe for $ 120 with a closed lock. She bought it on Craigslist, the former owner locked the safe and forgot the code. It was a challenge for Nathan - and he designed the robot for brute force.

Nathan Seldi is fond of designing various devices and gadgets, so over the next four months, they and colleagues from SparkFun Electronics made a car to break into the safe from commercial and self-made parts printed on a 3D printer. The total cost of all parts was $ 200. This amount includes an Arduino fee of $ 20, a $ 40 motor, aluminum case parts and various parts printed on a 3D printer, including a coupling for coupling with a limb handle, several magnets to attach to the safe case and sensors that verify that the robot has successfully turned handle and when it passes through zero.
In fact, it takes 73 minutes to go through the entire thousand combinations. This is the maximum time, and on average the process takes 36 minutes, so at DEFCON the robot was not far from the average result.
This demonstration should be a lesson for manufacturers of safes and other safety equipment. They need to understand that their every product will be tested and tried to hack thousands of geeks like these guys from SparkFun. If there is any bug or vulnerability in security, such as a broken third digit on the lock, like here, it will definitely be discovered and told to the whole world.
All Articles