WikiLeaks has posted documentation on ELSA, a CIA tool for spying on laptops with WiFi
June 28, 2017 WikiLeaks has published another batch of documents about the hacking tools of the CIA. This time the 42-page ELSA project user manual ( pdf ) is declassified. This system is designed to determine the physical location of computers running Windows 7 (32 and 64 bits), which are equipped with a WiFi module.
Document version 1.1.0 is dated September 27, 2013, that is, this is a relatively old manual. It is not known whether the CIA now uses such methods or they have implemented some more advanced technology.
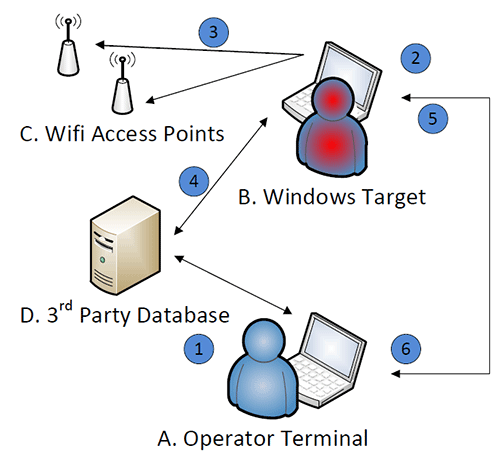
The system works very simple. It records the identifiers of WiFi access points, which are located near the victim's computer, and transfer metadata to third-party databases, from which they receive the coordinates of these access points. Based on the information received, ELSA calculates the latitude, longitude and indicates the accuracy of geolocation.
The documentation states that the relevant access point databases work to support geolocation services in Firefox, Opera, Chrome, and Internet Explorer browsers, in accordance with the W3C specifications. The accuracy of geolocation directly depends on the accuracy of the information in these third-party databases. To check whether the database coverage and information about the coordinates of the hot spots correspond to reality, the guide recommends that you visit the area of interest, open maps.google.com in the browser - and click the button to determine your location. If the browser correctly determines the coordinates of the agent via WiFi, then the coverage is good.
At the time of writing, Firefox, Opera, and Chrome browsers used Google's base for geolocation, and IE sent requests to Microsoft servers.
ELSA polls these services via HTTPS and saves the result in an encrypted file using 128-bit AES encryption.
The key element of the ELSA system is a tab that should be installed on a computer running Windows 7 belonging to the surveillance object. There the DLL is injected into some existing process. In the future, the trojan can either poll legal third-party databases for geolocation, or return raw data to the operator, so that it performs geolocation on its own.
Trojan collects system information about WiFi access points in the range according to the schedule set by the operator. Data collection is possible even if the victim’s computer has not established a connection with any access point in reality - Windows still keeps track of the surrounding hotspots, and this information is available to the Trojan. Thus, monitoring the movements of the victim’s computer is ongoing.
In the settings, you can specify that he calculates the coordinates himself as soon as the victim connects to the Internet. Then the saved log is transferred to the operator’s computer. To disguise, the default Trojan does not attempt to connect independently with the operator’s computer, but only passively writes data to the disk. To get the log, the operator must go to the victim's computer himself, using other backdoors and exploits - and take the log.
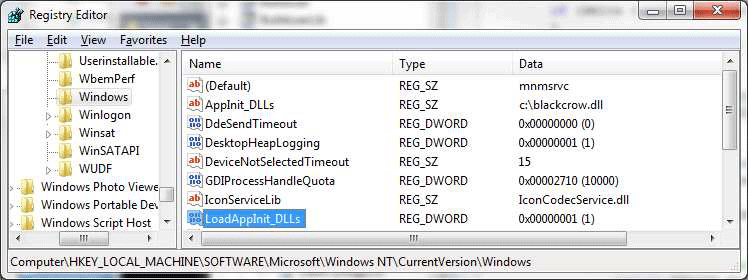
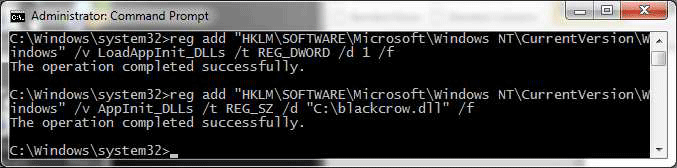
The settings indicate the maximum size of the log. Upon reaching the limit, the old entries are erased, giving way to more recent entries. The log is permanently stored on the disk, so that information is not lost during computer reboots.
In addition to the basic WiFi metadata (i.e. access point names), the trojan can be configured to collect additional metadata, such as MAC addresses, SSIDs, and signal strength information from each access point. This allows you to more accurately calculate the coordinates of the victim.
ELSA package
| Directory | File name | Notes |
|---|---|---|
| server / windows | patcher.exe | Windows configuration tool |
| server / windows | processor.exe | Windows decryption tool |
| server / windows | tool-x64.dll | Implant for Windows x64 |
| server / windows | tool-x86.dll | Implant for Windows x86 |
| server / windows | installDllMain.vbs | VBScript file for randomly placing the ELSA task in the task scheduler |
| server / windows | uninstallDllMain.vbs | VBScript file for deleting ELSA task from task scheduler |
| server / windows | sha1-windows-images.txt | Hashi SHA1 files from the bundle |
| server / windows | classifications-windows.txt | Classification of files from a set |
| docs | Elsa User Manual.pdf | This guide |
CIA experts emphasize that snooping through WiFi has certain advantages, because it does not require a GPS module or a cellular communication module on the device, a fairly regular WiFi interface, which is present in virtually every device today. By its nature, the ELSA system is best suited for spying on laptops, because constantly monitoring the coordinates of a stationary computer does not make sense, and Windows 7 is not used on smartphones. Obviously, the CIA has developed other tabs for iOS and Android, and it’s much easier to follow Metadata from the carrier.
The developer of the tool is the CIA Engineering Development Group. This unit is part of DDI (Directorate for Digital Innovation), see CIA organizational chart . It develops, tests, and maintains all CIA software.
All Articles