 この記事では、 インテルタンパープロテクションツールキットが、 Scrypt暗号化ユーティリティの重要なコードと貴重なデータを、静的/動的リバースエンジニアリングと変更から保護する方法を示します。 Scryptは、実際に広く使用されている最新かつ最も安全なパスワードキー生成機能です。 ただし、 scrypt関数のパラメーターが改ざんされるリスクがあり、ユーザーパスワードの脆弱性が発生します。 ツールキットは、これらの脅威を減らすのに役立ちます。 問題のアプリケーションの脅威モデルを定義し、 改ざん防止ツールをアプリケーションに適用する細目を考慮して、さらに保護するためにリファクタリングする方法を説明します。
この記事では、 インテルタンパープロテクションツールキットが、 Scrypt暗号化ユーティリティの重要なコードと貴重なデータを、静的/動的リバースエンジニアリングと変更から保護する方法を示します。 Scryptは、実際に広く使用されている最新かつ最も安全なパスワードキー生成機能です。 ただし、 scrypt関数のパラメーターが改ざんされるリスクがあり、ユーザーパスワードの脆弱性が発生します。 ツールキットは、これらの脅威を減らすのに役立ちます。 問題のアプリケーションの脅威モデルを定義し、 改ざん防止ツールをアプリケーションに適用する細目を考慮して、さらに保護するためにリファクタリングする方法を説明します。
この記事の主な目標は、実際のアプリケーションで見つかった重要なコードセクションや貴重なデータに対する攻撃から保護するためのIntel Tamper Protection Toolkitの機能を実証することです。 ツールキットを使用すると、難読化によって静的および動的なリバースエンジニアリングに対抗し、実行時に整合性を監視することにより、保護されたアプリケーションに変更が加えられないようにすることができます。
ここでは、ツールキットの難読化に使用されるiprotと呼ばれるコンポーネントを1つだけ見て、それをScrypt暗号化ユーティリティバージョン1.1.6に適用します。 このユーティリティは、入力されたパスワードに基づいた単純な暗号化キー生成機能です。 彼女を支持する選択はいくつかの理由でなされました。 まず、その機能のコードには、アプリケーションでよく使用される機能(ファイルの読み取りおよび書き込み操作、メモリ割り当て、暗号化機能、システムコール)が含まれています。 第二に、特定の数学的装置が含まれています。 第三に、ユーティリティは非常にコンパクトですが、開発者が自分のアプリケーションを保護するプロセスで実際に遭遇する可能性のあるさまざまな問題を示すことができます。 最後に、 scryptは最新の安全なキー生成機能であり、実際に積極的に使用されています。たとえば、新しいscryptベースのディスク暗号化はAndroid 4.4に組み込まれています。
コードの難読化
以下のリストに示されている機微な関数のソースコードの例を検討し、動的ライブラリをコンパイルします。
#define MODIFIER (0xF00D) int __declspec(dllexport) sensitive(const int value) { int result = 0; int i; for (i = 0; i < value; i++) { result += MODIFIER; } return result; }
機密機能のソースコード
IDA Proを使用して、結果のライブラリをリバースエンジニアリングします。 この図は、ロジックと計算用データを使用したコード実行の順序を示しています。 したがって、ハッカーはコード内のMODIFIERの値を簡単に確認して変更できます。

逆アセンブルされたコードの実行順序
さまざまなコード難読化技術は、実装の詳細を隠し、リバースエンジニアリングを複雑にし、コードの変更を防ぐのに役立ちます。 コードの難読化は、コードを同じ機能に変換しながら、リバースエンジニアリングを行ってプログラムのロジックとデータを理解することが困難なコードにコードを変換するプロセスです。 難読化は、コード内の機密データの盗難、その変更を回避し、開発者の知的財産を保護するために使用されます。
Intelタンパープロテクションツールキット
Intel Tamper Protection Toolkitは、コードを難読化し、Microsoft Windows *およびAndroid *で実行可能ファイルの実行時にアプリケーションの整合性を検証するために使用される製品です。 Tamper Protection Toolkitを使用して、アプリケーションの貴重なコードとデータを静的および動的なリバースエンジニアリングと変更から保護できます。 このツールで保護された実行可能ファイルには、特別なブートローダーや追加のソフトウェアは不要で、Intelプロセッサーで実行できます。
Intel Tamper Protection Toolkit Betaは、 ここからダウンロードできます 。
この記事では、コードの重要なセクションを難読化し、起こりうる攻撃から暗号化ユーティリティを保護するために、次のIntel Tamper Protection Toolkitコンポーネントを使用します。
- iprot-自己変更および自己暗号化コードを作成する難読化ツール。
- 暗号ライブラリ -基本的な暗号操作のセットを備えたライブラリ:安全なハッシュアルゴリズム、メッセージ認証(認証)コード、および対称暗号。
難読化ツールは、動的ライブラリ(.dll)とエクスポート関数のリストを受け取ります。 出力は、難読化されたエクスポート機能を備えた動的ライブラリです。 アドレスから開始して、入力に送信された動的ライブラリのコードが解析され、特別な内部表現に変換されます。 ブランチ、トランジション、およびチャレンジも、達成可能な場合は、分解および変換されます。 コードを難読化するために、考慮すべき制限がいくつかあります。 コードは、メモリ、外部の到達不能な関数呼び出し、間接遷移、グローバル変数を使用して低レベルの作業を行うことはできません。
この記事では、コードを難読化するためにコードに変更を加える際に発生する落とし穴と、発生した問題を克服する方法について説明します。
iprotを使用して、前のセクションで説明した動的ライブラリを難読化します 。
iprot sensitive.dll sensitive -o sensitive_obf.dll
IDA Proを使用して難読化されたコードをリバースエンジニアリングしてみましょう。
sensitive PROC NEAR jmp ?_001 ?_001: push ebp push eax call ?_002 ?_002 LABEL NEAR pop eax lea eax, [eax+0FECH] mov dword ptr [eax], 608469404 mov dword ptr [eax+4H], 2308 mov dword ptr [eax+8H], -443981824 mov dword ptr [eax+0CH], 1633409 mov dword ptr [eax+10H], -477560832 mov dword ptr [eax+14H], 15484359 mov dword ptr [eax+18H], -1929379840 mov dword ptr [eax+1CH], -1048448 <….>
逆アセンブルされた難読化コード
難読化されたコードが元のコードとどのように異なるかは簡単にわかります。 IDA Proは、難読化されたコードの実行順序のスキームを表示できず、 MODIFIER値が消えました。 また、難読化されたコードは静的および動的な変更から保護されます。
パスワードキー生成機能
パスワードキー生成関数(英語PBKDF )は、ユーザーが入力したパスワードを暗号アルゴリズムで使用できるキー(バイナリデータセット)に変換するために使用されます。 PBKDFは、アプリケーションセキュリティの非常に重要なコンポーネントです。ユーザーが入力したパスワードは、エントロピーが不十分であるため、暗号化アルゴリズムで安全に使用できないためです。 これらの機能は、アプリケーションを保護するために広く使用されています。たとえば、ディスク上のデータを暗号化/復号化するために、PGPシステムのパスワードから暗号化キーが取得されます。 また、オペレーティングシステムはこれらの機能を使用して、ユーザーパスワード(認証)を検証します。
一般に、PBKDFの数式は次のとおりです。
y = F ( P 、 S 、 d 、 t 1 、...、 t n )
ここで、 yは関数によって生成されたキー、 Pはパスワード、 Sはソルト、 dは生成されたキーの長さ、 t 1 、...、 t nは、プロセッサクロック速度、関数の計算に必要なRAMの量などのハードウェアリソースの量によって決定されるパラメーターです。 S saltは、指定されたパスワードで異なるキーを作成するために使用されます。 パラメーターt 1 、...、 t nは、関数の計算に消費されるハードウェアリソースを決定する役割を果たし、計算を複雑にし、ハードウェアレベルで並列化を使用するブルートフォース攻撃に対する保護を追加するように構成できます。従来のGPU。

PBKDF使用スキーム
ユーザーパスワードを回復するには、次の2つの方法があります。
- 攻撃者は、リークの結果として取得した生成されたキーを使用してパスワードを回復します。
- 攻撃者は、キーによって生成された暗号化または署名されたデータを使用してパスワードを回復します。
前者の場合、 Intel Tamper Protection Toolkitは、生成するために実行されるコードを非表示にして、生成されたキーを使用することにより、キーの漏洩を防ぎます。
Intel Tamper Protection Toolkitの2番目のケースは防止できませんが、攻撃者がキーの生成に使用されるパラメーターを安全でないものに変更しなかったことを確認するのに役立ちます。
以下は、実際に使用されるパスワード生成キー生成関数の例です。
- パスワードベースのキー派生関数 (PBKDF2)。 これは、 y = F ( P 、 S 、 c )の形式の関数です。ここで、 cは、 P 、 Sの関数Fを計算するために必要なプロセッサー時間を制御するための反復回数です。 PBKDF2は、RAMが非常に少ないシステムに実装できるため、GPUを使用したブルートフォース攻撃が非常に効果的になります。 それにもかかわらず、多くの製品は引き続きPBKDF2を使用しています。
- bcrypt 。 この機能は、GPUを使用するこのタイプの攻撃に対して、より多くの固定量のRAMを使用するため、より耐性があります。
Colin Percivalが開発した最も現代的で安全な機能はscryptです。 次の数式があります。
y = F ( P 、 S 、 d 、 N 、 r 、 p )、
ここで、 yは関数によって生成されたキー、 dは生成されたキーの長さ、 Pはユーザーパスワード、 Sはソルト、 p 、 r 、およびNはキーを生成するために必要なプロセッサ時間とRAMの量を設定するためのパラメーターです。 パラメータN 、 r 、 p 、 dの値は開くことができ、通常はキーまたは暗号化されたデータとともに保存されます。
パラメーターN 、 r 、 pの値に応じて、同じキーの生成には、異なる量のプロセッサー時間とメモリーサイズが必要になる場合があります。 たとえば、パラメーターが〜100 msおよび〜20 MBを要求する場合、 scrypt関数に対する通常のGPUに対するブルートフォース攻撃は、少量のRAMを必要とし、GPU上の異なるパスワードの並列計算を可能にするPBKDF2ほど効果的ではありません。
暗号化暗号化ユーティリティ
Scrypt暗号化ユーティリティは、CTRモードのAESアルゴリズムと、入力ファイルを操作するためのユーザーパスワード用のscrypt関数によって生成されたキーを使用します。 実行するために必要なパラメーターと追加のパラメーターが含まれています。
必須は次のとおりです。
- scryptがキーを生成するために使用するパスワード 。
- モード :暗号化または復号化。
- 入力ファイル名 。
追加オプション:
- -tキーの生成に必要な秒単位の時間。
- -mは、キーの生成に使用されるRAM の割合です。
- -Mキーの生成に使用されるRAMのバイト数。
- 出力ファイルの名前 。
たとえば、コマンドでユーティリティを実行する
scrypt enc infile -t 0.1 -M 20971520
キーを生成するには、100msのプロセッサ時間と20MBのRAMが必要です。 このようなパラメーター値は、ブルートフォース攻撃の並列化を複雑にします。
以下の図は、ユーザーが暗号化のための入力ファイルの名前、パスワード、および必要なハードウェアリソースを決定するパラメーターを入力した場合のScryptユーティリティの操作を表しています。
暗号化中にユーティリティによって実行される手順を説明します。
- Scryptパラメーターを収集して変換します。 プログラムは、プロセッサー時間のパラメーターとキーの生成に必要なRAMの量を選択し、それらをscrypt関数が認識するパラメーターに変換します。
- 暗号化キーの生成。 scrypt関数は、ユーザーパスワードと前の手順で計算されたパラメーターN 、 r 、 pを使用して64バイトのキーを生成します。 dk 1キーの下位32バイトは、パラメーターN 、 r 、 p 、 ソルト 、および暗号化されたデータの認証コードを計算するために使用されます。 したがって、復号化のプロセスでは、入力したパスワードの正確性と暗号化されたデータの整合性を確認できます。 dk 2キーの上位32バイトは、CTRモードでAESアルゴリズムを使用して入力ファイルを暗号化するために使用されます。
- 暗号化パラメータの認証コードの計算。 このステップで、キーの生成に使用されるパラメーターN 、 r 、 pおよびsaltの認証(認証)コードが計算されます。
- CTRモードの32バイトAESブロックを使用したOpenSSL暗号化。 CTRモードで32バイトのAES暗号を使用して、 dk 2で入力メッセージを暗号化します。
- 暗号化されたデータの認証コードの計算。 最後に、 dk 1を使用して整合性を確保するために、認証コードが計算されてデータが暗号化されます。 出力ファイルには、暗号化されたデータ、パラメーターN 、 r 、 p 、暗号化中に使用されるソルト 、および暗号化されたデータとパラメーターの整合性を保証する認証コードが含まれます。

暗号化暗号化スキーム
考えられる脅威
暗号化モードでユーティリティの動作を分析し、脅威モデルを決定します。 パラメータN 、 r 、 p 、 saltの値、および中間ステップで取得された生成キーは重要なデータであり、リアルタイムの変更に対する保護が必要です。 たとえば、デバッグモードでは、攻撃者はブルートフォース攻撃に対する生成されたキーの抵抗を弱めるために、パラメータN 、 r 、 pの他の値を設定できます。
次の図は、ユーザーが暗号化されたテキストN 、 r 、 p 、 salt 、 認証コード 、およびパスワードを含む入力ファイルの名前を入力したときの復号化プロセスを示しています 。
復号化中にユーティリティによって実行される手順を説明します。
- 暗号化設定パラメーター。 復号化の入力ファイルには、暗号化されたデータ、認証コードhmac 1 、 hmac 2 、および暗号化中に使用されるパラメーターN 、 r 、 p 、 saltが含まれます。 このステップで、これらのパラメーターは入力ファイルから差し引かれ、鍵生成機能に転送されます。
- 暗号化キーの生成。 scrypt関数は、前の手順で取得したパスワードとパラメーターN 、 r 、 p 、 saltのキーを生成します。 このキーの下位32バイトと上位32バイトは、それぞれ図dk 1とdk 2に示されています。
- Scryptパラメータとパスワードの整合性をチェックします。 N 、 r 、 p 、 salt、およびpasswordの整合性は、認証コードを使用して検証されます。 パスワードが正しいことを確認するために、ユーティリティはdk 1を使用してパラメーターN 、 r 、 p 、 saltの認証コードを計算し、受信した値と値hmac 1を比較します。 一致する場合、パスワードは正しいです。
- 暗号化されたデータの整合性を確認します。 暗号化されたデータが変更されていないことを確認するために、データの認証コードがdk 1を使用して計算され、 hmac 2の値と比較されます。 一致する場合、データは破損していないため、次の手順で復号化できます。
- CTRモードのAESアルゴリズムによるOpenSSL 32バイトブロック復号化。 最後に、データはdk 2を使用してCTRモードで32バイトのAESブロックアルゴリズムを使用して復号化されます。 出力ファイルには、復号化されたデータが含まれています。

暗号解読スキーム
Windowsでのユーティリティの移植
この作業の目的は、 タンパープロテクションツールキットを使用して、Windows用のScrypt暗号化ユーティリティを保護することです。 ユーティリティの初期バージョンはLinux用に作成されているため、最初のタスクはWindowsに移植することです。
プラットフォーム固有のコードは、次の条件付きディレクティブの間に配置されます。
#if defined(WIN_TP) // Windows #else // Linux #endif // defined(WIN_TP)
WIN_TPプリプロセッサディレクティブは、Windows固有のコードを分離します。 WindowsでのアセンブリにはWIN_TPを定義する必要があります。そうしないと、Linuxコードがアセンブリに選択されます。
Microsoft * Visual Studio 2013開発環境を使用して、ユーティリティをビルドおよびデバッグします。 プロセス、スレッド、メモリおよびファイル管理、サービスインフラストラクチャ、ユーザーインターフェイスなど、Windows OSとLinux OSの一部のオブジェクトには違いがあります。 ユーティリティを移植するときには、これらすべての違いを考慮する必要がありました。 それらについて以下に説明します。
- ユーティリティは、コマンドライン引数を解析するためにgetopt()関数を使用します。 使用可能なプログラム引数のリストは上記のとおりです。 getopt()関数は、POSIX標準セットに従ってunitstd.hヘッダーファイルにあります。 開いているgetopt_portプロジェクトのget_opt()実装を使用します。 これを行うには、 getopt_portプロジェクトからプロジェクトにファイルgetopt.hおよびgetopt.cを追加します。
- POSIX APIで宣言されている残りのgettimeofday()関数は、ユーティリティによって使用され、 salsa oppsを測定し、ユーザープラットフォームで実行される1秒あたりの操作回数salsa20 / 8をカウントします。 ユーティリティはサルサoppsメトリックを使用して、パラメータN 、 r 、およびpのより安全な値を選択するため、 scryptアルゴリズムは、ブルートフォース攻撃を回避する最小回数でsalsa20 / 8操作を実行します。 gettimeofday()関数の実装をscryptenc_cpuperf.cファイルに追加しました。
- 構成アルゴリズムを開始する前に、ユーティリティはオペレーティングシステムに、POSIXセットからgetrlimit関数(RLIMIT_DATA、...)を呼び出してキーを生成することにより、キャプチャされる使用可能なRAMの量を要求します。 Windowsでは、プロセスデータセグメントの最大サイズ(初期化されたデータと初期化されていないデータ、および束)のハード制限と非ハード制限は4GBに設定されます。 これらはすべて、以下のコードに示されています。
/* ... RLIMIT_DATA... */ #if defined(WIN_TP) rl.rlim_cur = 0xFFFFFFFF; rl.rlim_max = 0xFFFFFFFF; if((uint64_t)rl.rlim_cur < memrlimit) { memrlimit = rl.rlim_cur; } #else if (getrlimit(RLIMIT_DATA, &rl)) return (1); if ((rl.rlim_cur != RLIM_INFINITY) && ((uint64_t)rl.rlim_cur < memrlimit)) memrlimit = rl.rlim_cur; #endif // defined(WIN_TP)
- さらに、 sysendian.hファイルでインライン関数を定義するためのディレクティブがMSVSコンパイラーに追加されました。
#if defined(WIN_TP) static __inline uint32_t #else static inline uint32_t #endif // WIN_TP be32dec(const void *pp);
- tarsnap_readpass(...)関数を移植して、ターミナルで非表示のパスワード入力を実行しました。 この関数は、ターミナルウィンドウの文字の表示をオフにし、パスワードを空白文字でマスクします。 パスワードはメモリに割り当てられたバッファに保存され、次のScrypt設定およびキー生成機能に送信されます。
/* , */ #if defined(WIN_TP) if ((usingtty = _isatty(_fileno(readfrom))) != 0) { GetConsoleMode(hStdin, &mode); if (usingtty) mode &= ~ENABLE_ECHO_INPUT; else mode |= ENABLE_ECHO_INPUT; SetConsoleMode(hStdin, mode); } #else if ((usingtty = isatty(fileno(readfrom))) != 0) { if (tcgetattr(fileno(readfrom), &term_old)) { warn("Cannot read terminal settings"); goto err1; } memcpy(&term, &term_old, sizeof(struct termios)); term.c_lflag = (term.c_lflag & ~ECHO) | ECHONL; if (tcsetattr(fileno(readfrom), TCSANOW, &term)) { warn("Cannot set terminal settings"); goto err1; } } #endif // defined(WIN_TP)
- オリジナルのgetsalt()関数は、擬似ランダムシーケンスを取得するために、Unix OSの一部である特殊ファイル/ dev / urandomを読み取ります。 Windowsでは、 Ivy Bridgeから始まるIntel XeonおよびCoreチップで利用可能なハードウェア乱数ジェネレーターからのrdrand()命令を使用します。 この場合、難読化ツールTamper Protectionを使用してgetsalt()関数を難読化することはできないため、標準C関数は擬似ランダムシーケンスの生成に意図的に使用されません。 この関数によって生成されるソルトはセクション3で保護オブジェクトとして分類されるため、 getsalt()関数は静的および動的な変更やリバースエンジニアリングから難読化ツールによって保護する必要があります。 以下は、 saltを生成するためにコードに加えられた変更です。
#if defined(WIN_TP) uint8_t i = 0; for (i = 0; i < buflen; i++, buf++) { _rdrand32_step(buf); } #else /* /dev/urandom. */ if ((fd = open("/dev/urandom", O_RDONLY)) == -1) goto err0; /* , buffer. */ while (buflen > 0) { if ((lenread = read(fd, buf, buflen)) == -1) goto err1; /* , buffer. */ if (lenread == 0) goto err1; /* */ buf += lenread; buflen -= lenread; } /* */ while (close(fd) == -1) { if (errno != EINTR) goto err0; } #endif // defined(WIN_TP)
Intel Tamper Protection Toolkitによるユーティリティ保護
次に、ユーティリティコードをリファクタリングして、脅威モデルで定義されたすべての重要なデータを保護します。 このようなデータの保護は、 iprotツールを使用してコードを難読化することにより実現されます。これにより、セットからコンパイラーが難読化されます。 また、合理性の原則に従い、重要なデータを作成、処理、使用する機能のみを難読化します。
難読化ツールがダイナミックライブラリを入力として受け取り、コマンドラインで指定された保護された関数のみを含むバイナリファイルを生成することは既にわかっています。 そのため、重要なデータを操作するすべての関数を動的ライブラリ内に配置して、さらに難読化するようにします。 コマンドライン引数の解析、パスワードの読み取りなどの残りの機能は、メインの実行可能ファイルに保護されないままにします。
保護されたユーティリティの新しい構造を次の図に示します。 このユーティリティは、メインの実行可能ファイルと、難読化されるダイナミックライブラリの2つの部分に分かれています。 メインの実行可能ファイルは、コマンドライン引数の解析、パスワードの読み取り、および入力ファイルのメモリへのロードを行います。 , scryptenc_file , scryptdec_file , ( N , r , p , ).
, , Scrypt HMAC scrypt : N , r , p . HMAC , scrypt_ctx_enc_init , scrypt_ctx_dec_init , scryptenc_file scryptdec_file , . , . scrypt_ctx_enc_init scrypt_ctx_dec_init scrypt : , .
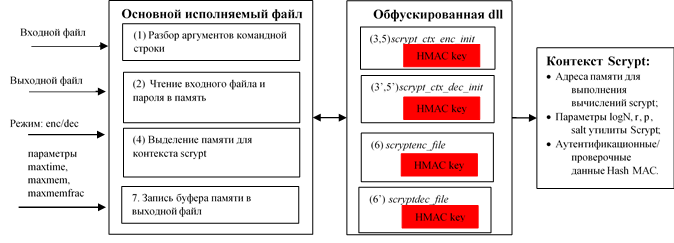
Scrypt
, : .
:
- getopt() . .
- / .
- scrypt_ctx_enc_init scrypt ( N , r , p ), maxmem , maxmemfrac maxtime , . HMAC ( -) , , scrypt . , , scrypt .
- , .
- scrypt_ctx_enc_init . scrypt , HMAC. , scrypt HMAC. , . , -, , .
- scryptenc_file , . scrypt ( N , r , p ), . , scrypt . . , scrypt . , , .
:
- getopt() .
- / .
- scrypt_ctx_dec_init , . , , scrypt .
- , .
- scrypt_ctx_dec_init . , .
- scryptdec_file , . scrypt ( N , r , p ), . , scrypt . , .
OpenSSL AES CTR Intel Tamper Protection Toolkit crypto library . OpenSSL , crypto library iprot . AES scryptenc_file scryptdec_file / . ( scrypt_ctx_enc_init , scrypt_ctx_dec_init , scryptenc_file scryptdec_file ) scrypt . iprot .
Tamper Protection . iprot . , : scrypt , HMAC HMAC . HMAC - . , , scrypt , , scryptenc_file scryptdec_file . iprot , .
scrypt_ctx_enc_init scrypt . buf_p scrypt_ctx_enc_init . ( null ), , . scrypt , HMAC scrypt . .
// : scrypt if (buf_p == NULL) { // scrypt // <...> // HMAC itp_res = itpHMACSHA256Message((unsigned char *)ctx_p, sizeof(scrypt_ctx)-sizeof(ctx_p->hmac), hmac_key, sizeof(hmac_key), ctx_p->hmac, sizeof(ctx_p->hmac)); *buf_size_p = (r << 7) * (p + (uint32_t)N) + (r << 8) + 253; }
buf_p , scrypt_ctx_enc_init . HMAC, , , . , buf_p , HMAC . , , .
// : scrypt if (buf_p != NULL) { // HMAC itp_res = itpHMACSHA256Message( (unsigned char *)ctx_p, sizeof(scrypt_ctx)-sizeof(ctx_p->hmac), hmac_key, sizeof(hmac_key), hmac_value, sizeof(hmac_value)); if (memcmp(hmac_value, ctx_p->hmac, sizeof(hmac_value)) != 0) { return -1; } // scrypt: // ctx_p->addrs.B0 = … // HMAC itp_res = itpHMACSHA256Message( (unsigned char *)ctx_p, sizeof(scrypt_ctx)-sizeof(ctx_p->hmac), hmac_key, sizeof(hmac_key), ctx_p->hmac, sizeof(ctx_p->hmac)); }
, , : (. indirect jump ) . C , -, . - memcmp , iprot . -, memcmp , memset , memmove , . , .
, , double , . , , pickparams salsa20/8 double 32768. , .
double opslimit; #if defined(WIN_TP) // unsigned char d_32768[] = { 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0xE0, 0x40}; unsigned char d_32768[sizeof(double)]; d_32768[0] = 0x00; d_32768[1] = 0x00; d_32768[2] = 0x00; d_32768[3] = 0x00; d_32768[4] = 0x00; d_32768[5] = 0x00; d_32768[6] = 0xE0; d_32768[7] = 0x40; double *var_32768_p = (double *) d_32768; #endif /* salsa20/8. */ #if defined(WIN_TP) if (opslimit < *var_32768_p) opslimit = *var_32768_p; #else if (opslimit < 32768) opslimit = 32768; #endif
16- , double , double . , double2hex 16- double .
iprot , :
iprot scrypt-dll.dll scryptenc_file scryptdec_file scrypt_ctx_enc_init scrypt_ctx_dec_init -c 512 -d 2600 -o scrypt_obf.dll
. . , , .
| |
. : . 512- 2600- . . , , . , .
, Intel Tamper Protection Toolkit , Github.
謝辞
Scrypt .
参照資料
- K. Grasman. getopt_port on github
- C. Percival. The scrypt encryption utility
- C. Percival. “Stronger key derivation via sequential memory-hard functions”.
- C. Percival, S. Josefsson (2012-09-17). “The scrypt Password-Based Key Derivation Function”. IETF.
- N. Provos, D. Mazieres, J. Talan Sutton 2012 (1999). “A Future-Adaptable Password Scheme”. Proceedings of 1999 USENIX Annual Technical Conference: 81–92.
- W. Shawn. Freebsd sources on github
: , ,
{Roman.Kazanstev, Denis.Katerinskiy, Thaddeus.C.Letnes}@intel.com