C, C ++ and DotNet decompile are the basics of reverse. Solving problems for reversing with r0ot-mi. Part 1

In this article, the first 5 tasks, we will learn the basics of disassembly, solve the problems of the initial reverse level, and also decompile the dotNet application.
Organizational Information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
C, GCC32
Consider the simplest case. This is the first reverse quest.
In tasks of this type, when the password is stored as a string, it can be found without using any special tools. Let's run the program and see what it displays.
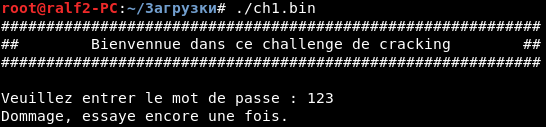
Fine. We have an invitation and a message about the wrong password. We look at the lines in the program file, and we find among them an invitation and a message about the wrong password. There should be a password nearby.

Thus, from the lines next to each other, there is one that looks like a password. Let's try it.

The task is completed. We give the password, we get 5 points.
ELFx86, Basic
We are asked to find a password.

We load the program into the IDA Pro debugger (I use version 7.0) and press F5 to decompile the program.
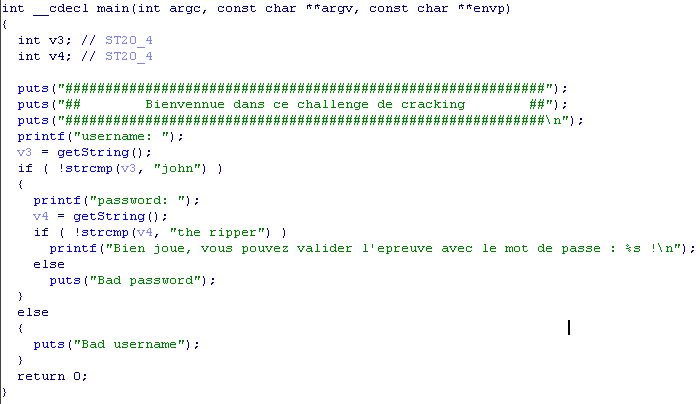
Thus, the entered name is compared with the string john, and the password is compared with the ripper.
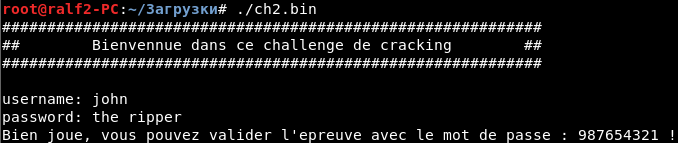
Thus, we correctly solved the task and get our password. We hand it over and earn another 5 points.

PEx86, 0 protection
This time we are given an exe-shnik.
Download it in IDA Pro.

The program does not store debugging information, so we do not see the usual function names like main. Let's look at the lines in the program, for this press + F12.
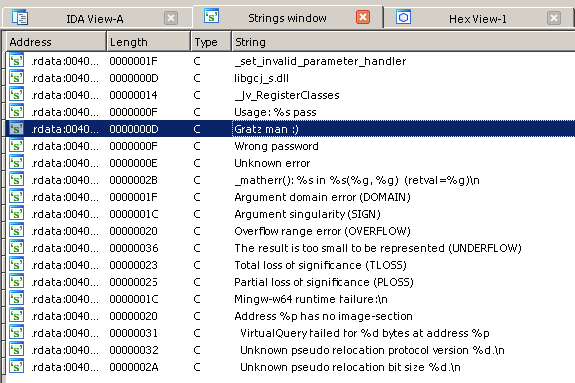
We see messages about entering the correct and incorrect passwords. Now we can find the block with this line in the code and see what condition precedes it. Double click on the line.
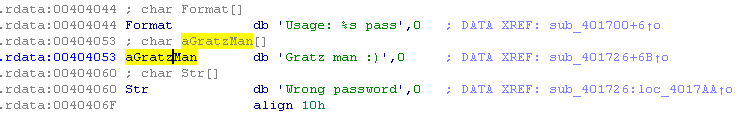
We are located in the rdata section. Let's find all the links in the code for this address. To do this, press X.

Thus, in the program code there is only one call to our line. We double-click and go to the code.

We are in the main program code. We are decompiling.
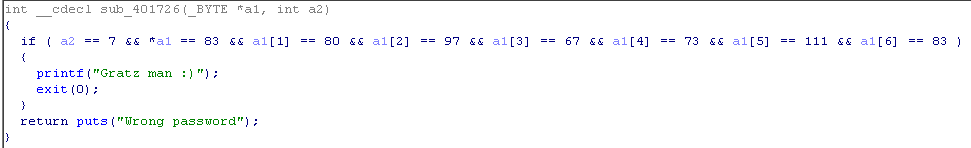
Here, a check of some number a2 and a line a1 takes place. Let's translate a numeric to a character.

To do this, press R. on the number. And our code has changed.

We now know the line, it remains to find out what the number is a2. Let's see all the links to this function.
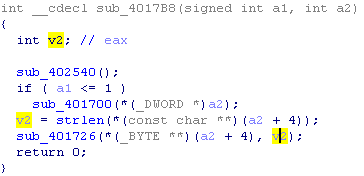
It is called only once.

As you can see, the length of the string is passed as the second parameter. Check the password found.

We give in and get 5 points.

ELF-C ++, 0 protection
We are offered to solve a program in C ++.
We open in IDA Pro and we pass to the place of a call of the message on the correct password. Let's color it green.

Let's make the graph smaller.

So we need to go through two conditions. Let's analyze them. In the first condition, the number of arguments is compared to 1. That is, the program must have more than one argument (the first is the name of the program).
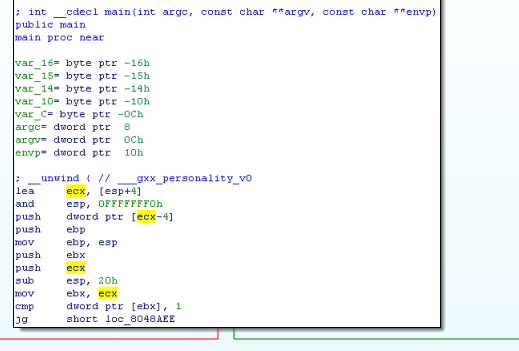
We analyze the second condition.
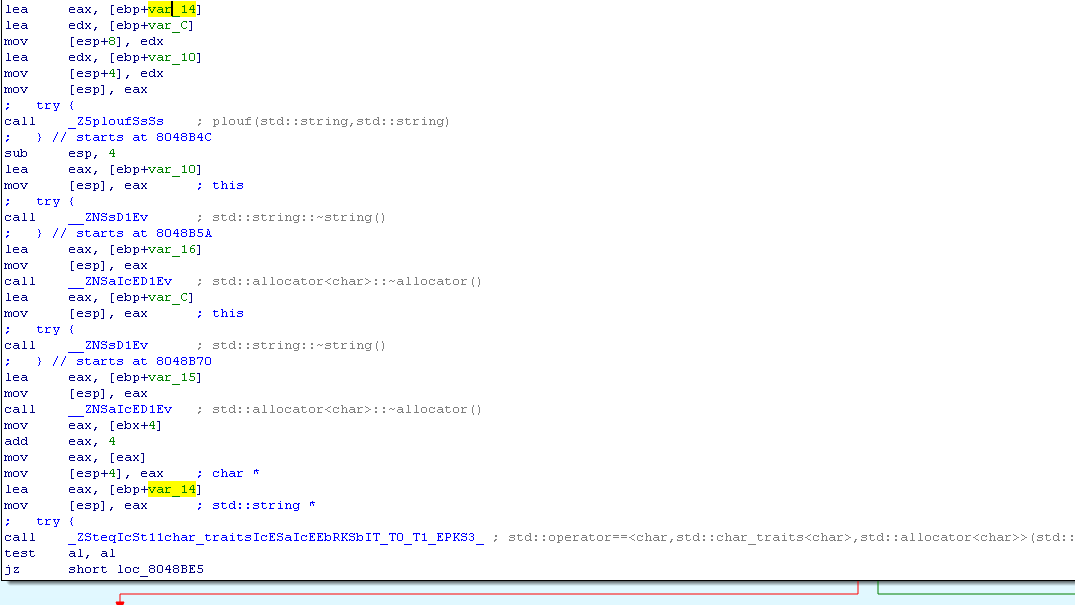
The string we entered is compared with the string that is passed as a parameter to the plouf function. We decompile it.
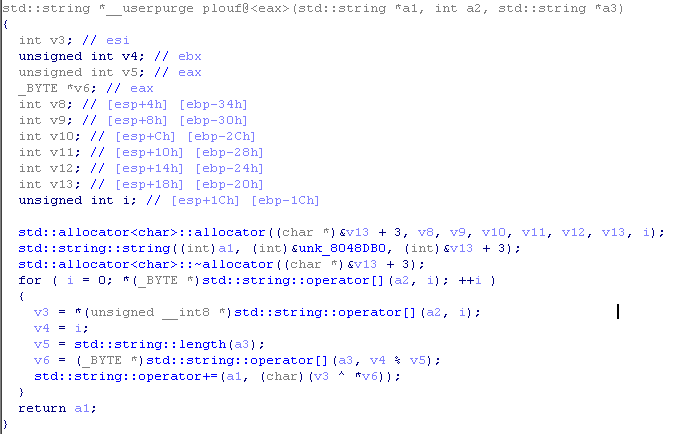
Parse the code. Actually a2 - is a string. Thus, the cycle runs from i = 0, until the i-th element of line a2 is 0 (that is, until it reaches the end of the line).
V3 = a2 [i]
V5 = length (a3)
V6 = a3 [i% v5]
That is, the line at address a1 will be equal to the two proxied lines a2 and a3. Let's go back to the main function and find these lines.
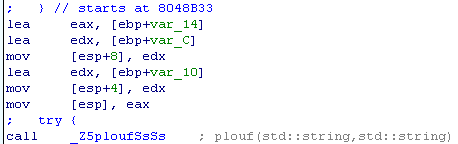
So we need to define the var_C and var_10 parameters. We will find them a little higher. These are the strings unk_8048BC4 and unk_8048DCC, respectively.
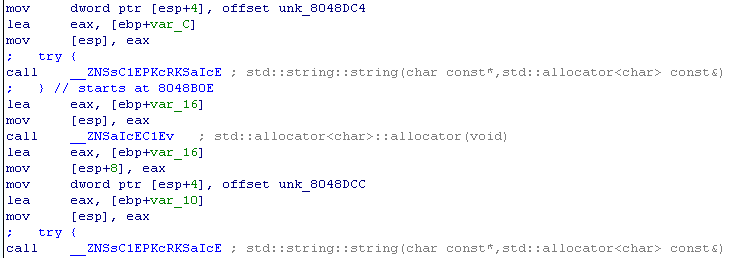
Find the value of the strings.
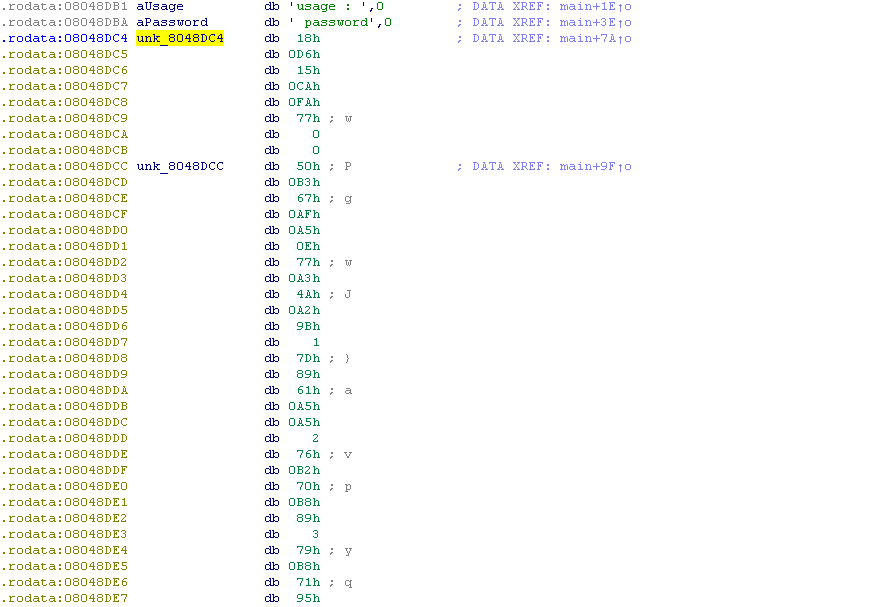
Well, we’ll write a code to proxify them.

We get the password.
PE-DotNet, 0 protection
In this assignment, we are offered to reverse the .NET application.

You can determine it using the file utility.
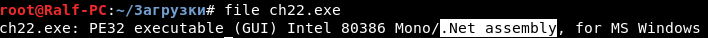
C # is a decompiled language, so we can get the original project. This can be done using dnSpy .
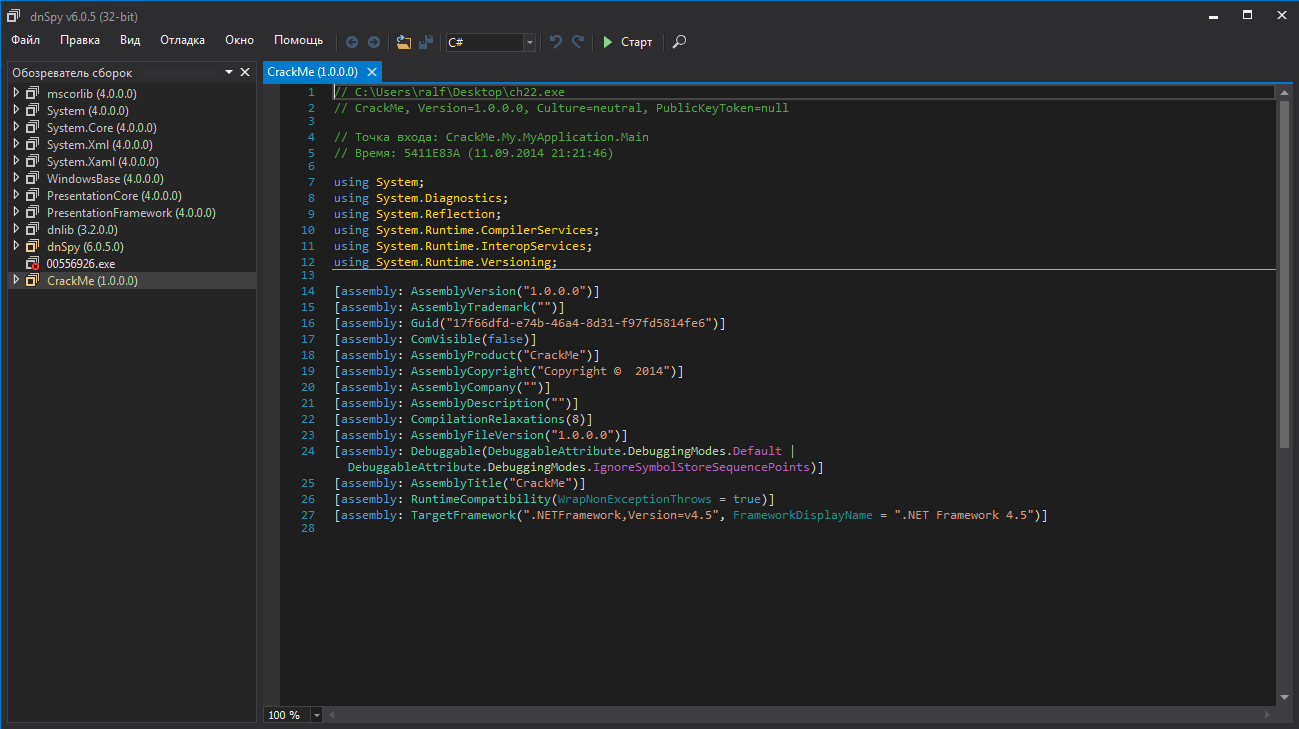
Let's open the CrackMe project and find functions and methods.

The Button1_Click method verifies the password at the click of a button.

In the source code we find the password. Check it out.

We hand it over.

That's all for now. To be continued ... You can join us on Telegram . There you can propose your own topics and vote on the choice of topics for the following articles.
All Articles