Miner sites have learned to hide the browser on users' computers.
The Coinhive mining cryptocurrency affiliate program in users' browsers (and other JS miners) is getting more and more popular with attackers. Unsuspecting users go to the site - and do not pay attention that their CPU load increases dramatically (Coinhive mine Monero on the CryptoNight algorithm, which creates a large block in memory and prevents internal parallelism, therefore, mining eliminates the use of ASIC and is most effective on CPU).
The attackers continue to hack sites and place scripts for mining. The same goes with browser extensions. Recently, they have implemented the CryptoLoot miner even in the CookieScript.info script , which helps other websites show a warning about the use of cookies at the request of the European Union - this is the most popular free service of this kind, it is used by thousands of other websites, otherwise they face a fine from the EU up to $ 500,000.
It was possible to look at the activity of intruders with a grin: well, how much will they generate there in two minutes that the user spends on the site? The ephemeral nature of mining in the browser remained the main drawback of this type of malware. But experts at Malwarebytes Labs note that the owners of the mining botnets, unfortunately, have managed to eliminate this drawback. Now mining on users' computers continues after they leave the infected site. And even after closing the browser.
Tests were conducted in Google Chrome browser. The animation shows that when you close the browser with a regular site, the CPU usage immediately drops to about zero. But when you close a site with a built-in miner for some reason, the use of CPU remains at the same level of more than 60% (for masking, the miner does not correctly load the processor to the maximum).
The trick is that despite the visible closing of the browser window, in fact, Google Chrome is not closed, but remains in memory. The malware opens an invisible pop-up window like pop-under . Admittedly, this is a very competent technique.
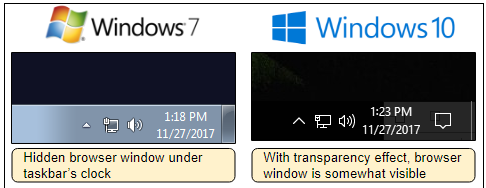
The coordinates of the pop-up window are chosen in such a way as to hide exactly behind the clock on the taskbar.
Animation 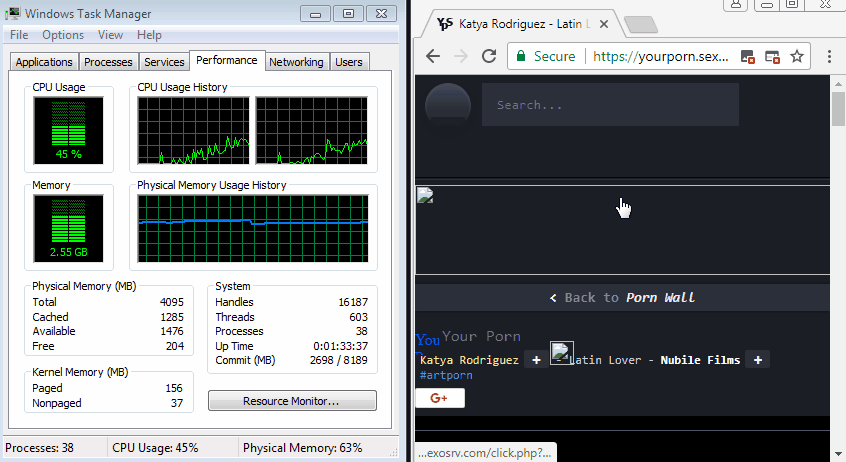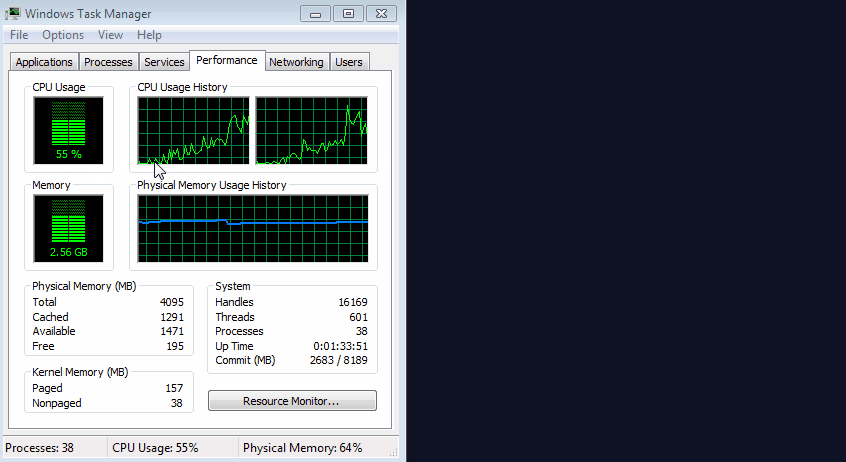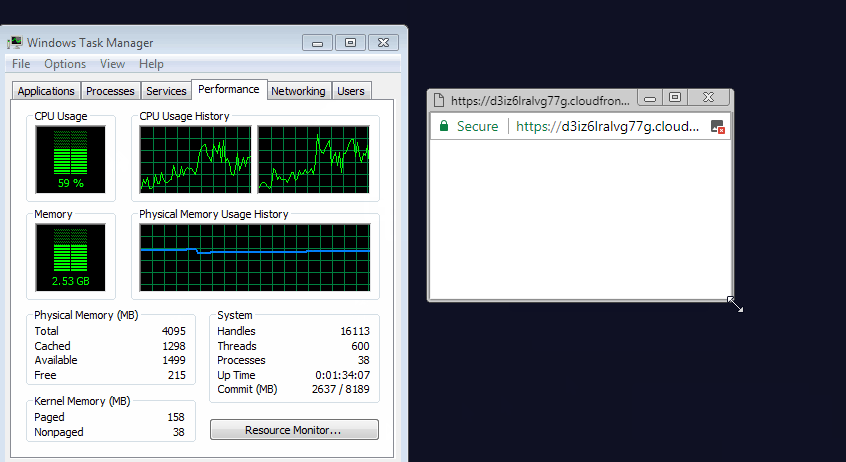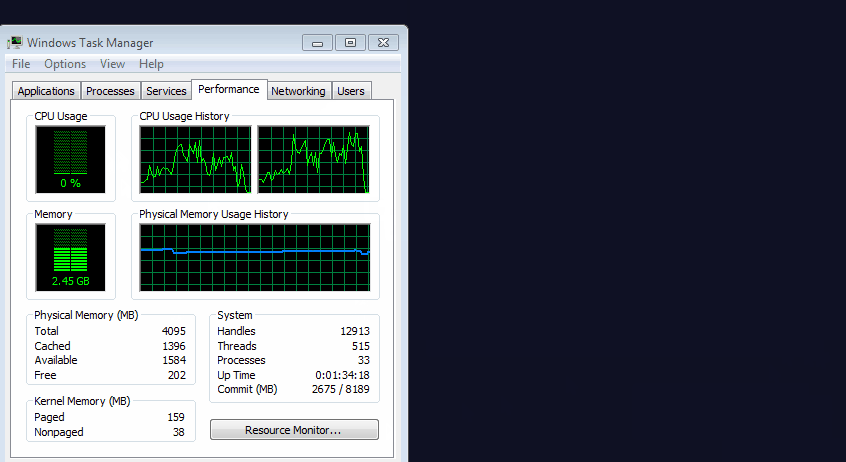

The coordinates of the window may vary slightly, depending on the screen resolution on the victim's computer, but it fits in behind the clock. True, there is one nuance. If the operating theme has a design theme with translucency, then the window is still slightly visible behind the panel (see the screenshot at the beginning of the article).
Security experts accidentally stumbled upon this trick when visiting one of the porn sites. It runs the ad network Ad Maven, which bypasses ad blockers and, in turn, loads resources from the Amazon cloud - this is one of the ways to get around the ad blocker. Although the malicious load itself .wasm does not load directly from AWS, but from an unauthorized hosting.
In the script code, you can notice some functions that are mentioned in the Coinhive miner's documentation . For example, there is a test for support of WebAssembly - with this technology, the browser makes the most of the resources of the hardware installed on the computer. If WebAssembly is not supported, the miner switches to a slower JavaScript version (asm.js).
As mentioned above, the miner does not drive the processor frequency by 100%, but loads it moderately in order to work imperceptibly for a long time.
Given this cunning behavior of malware, it is difficult to rely entirely on ad blockers. Now, after closing the browser, you need to check that the browser has disappeared from the taskbar, where the running processes hang. But if the badge is attached to the panel, it should not disappear anywhere. Therefore, just in case it is better, after closing the browser, to check that there are no running processes like chrome.exe and the like in the task manager. Although many users nowadays never close their browser at all. So the last method remains - to constantly monitor the CPU load, recommended by Malwarebytes Labs.
They also publish infection indicators to check that nothing extra has appeared on the site:
145.239.64.86,yourporn[.]sexy,Adult site
54.239.168.149,elthamely[.]com,Ad Maven popunder
52.85.182.32,d3iz6lralvg77g[.]cloudfront.net,Advertiser's launchpad
54.209.216.237,hatevery[.]info,Cryptomining site
Cryptonight WebAssembly module:
fd472bd04c01a13bf402775441b0224edef4c062031e292adf41e5a5897a24bc
Any more or less technically literate person is unlikely to be deceived in this way. At least not for long. But there are a huge number of users who do not know anything about crypto-miners in the browser, so such malware can become very popular.
All Articles