Android program to control the "smart" vibrator stored audio files without the knowledge of the girls

Mobile application Lovense Remote for remote control of the vibrator
A small scandal broke out around the Hong Kong company Lovense, which is engaged in the production of sex toys and distributes the mobile application Lovense Remote for remote control. One of the users of Reddit noticed that the program without the knowledge of the girl keeps a history of the use of a vibrator. Moreover, in the local program folder on the smartphone, you can find a six-minute audio file recorded during the last session.
Of course, this behavior caused confusion among users. In the Reddit comments. The girls say that they did give permission to use the camera and microphone, but it was understood that they would be used only for the chat embedded in the program and sending voice commands, and not for constantly recording all the sounds they make in the process of ... working with gadget Unauthorized actions of the program were confirmed by several people in the thread.
One of the users, who introduced himself as a representative of Lovense , acknowledged the incorrect behavior of the application, which he called a "minor bug." He said that the bug is only in the Android version of the application, and no audio files are sent to the company's servers. Temporary audio files are recorded and stored exclusively locally. On the same day, an update of the application was released, in which they fixed the bug.
In a comment to The Verge , Lovense confirmed that the person on the forum is indeed the official representative of the company and his words are true: “As was said, we do not store audio files on our servers. In order for the sound function [voice control and audio clip transfer] to work, we need to create an audio file in the local cache. It is assumed that this file should be deleted after each session, but due to a bug in the latest version of the Android application, it was not deleted, the company said in a statement. “Because of this bug, the sound file was stored on the device until the next session, when it was overwritten by a new audio file in the cache.”
Everything looks so that the actions of the company were really unintentional, they look like a small technical error. However, this does not negate the fact that the girl's boyfriend or another stranger who got access to her smartphone, could easily listen to or copy himself quite intimate sounds. Now, many companies are concerned about the distribution of intimate photos and videos for the purpose of pornography, and so an intimate sound is also quite suitable for these purposes. In other words, the leakage of such personal content is an immediate threat to the information security and privacy of the user.
It should be noted that this is not the first case of leakage of this kind of confidential data from gadgets of the company Lovesense. Just a month ago, it became known about the vulnerability of another gadget of a company called Hush (a device of incomprehensible functionality, such as a butt plug, something like a plug in the bathroom). Like many other sex toys, it works via Bluetooth Low Energy (BLE) protocol. It turned out that this gadget can be hacked .
A hacker named Simone Margaritelli (Simone Margaritelli), known in the community as evilsocket, wrote the BLE-BLEAH scanner ( source code on Github ) and published instructions for cracking BLE-gadgets.
The scanner is extremely easy to use. It is enough to run it with the
-t0
flag - and it proceeds to continuously scan all the BLE gadgets around.

If among them you find something interesting, then you can connect to the device.

After that, arbitrary commands can be sent to the device, which it will execute. The demo video below shows how a gadget receives a
vibrate:20;
command from a laptop through a BLEAH scanner
vibrate:20;
. In this case, the device thinks the team comes from the Lovense Remote mobile app, the same app that is used to control the aforementioned vibrator and other Lovense sex toys.
Hackers disassembled this Java application and disassembled commands for management.
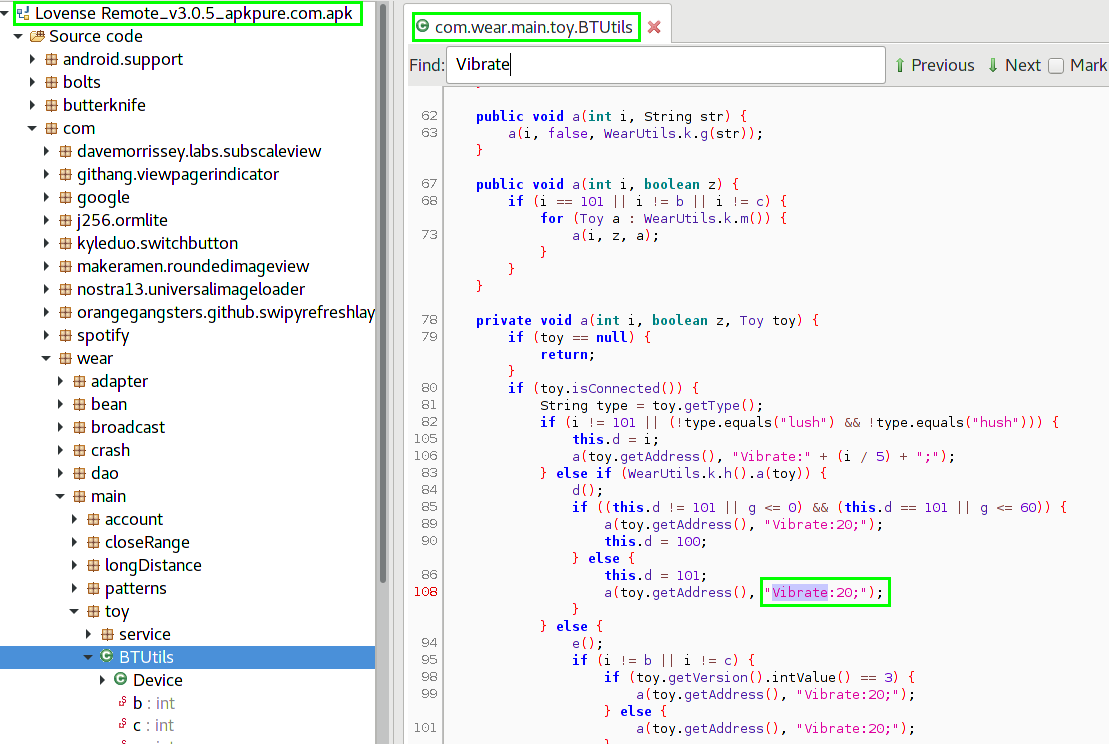
Lovense Remote application source code
It is clear that in the case of a sex toy, unaccounted remote control can be of some danger: for example, an attacker can thus quickly discharge the battery of the gadget and ruin the user all the fun.
In another case, users of the We-Vibe Bluetooth vibrators filed a collective lawsuit for $ 3.75 million against the Canadian company Standard Innovation, that the mobile application for managing the gadget recorded personal information. The manufacturer agreed to pay compensation (the amount will be divided among all who complete and submit the questionnaire, a maximum of $ 199 for each girl).
All Articles