Only Kaspersky Anti-Virus blocks the CIA utility.
 The site WikiLeaks has published a new set of CIA documents from the Vault 7 collection. This time the hacker tool called Dumbo , which is designed to interfere with cameras and microphones on a computer running Microsoft Windows, is declassified. The tool works with devices installed directly on a PC, as well as with wireless (Bluetooth, WiFi) or connected via cable. You can pause their work or erase the record.
The site WikiLeaks has published a new set of CIA documents from the Vault 7 collection. This time the hacker tool called Dumbo , which is designed to interfere with cameras and microphones on a computer running Microsoft Windows, is declassified. The tool works with devices installed directly on a PC, as well as with wireless (Bluetooth, WiFi) or connected via cable. You can pause their work or erase the record.
Dumbo is an auxiliary program for the work of the CIA division called PAG (Physical Access Group). This unit is engaged in physical intrusions, hacks, normal operations with physical access to equipment, etc. For example, if you need to install listening equipment, bugs on a computer, TV, phones, etc. in an apartment or office. PAG is a special division of the Cyber Intelligence Center CCI (Center for Cyber Intelligence).
Dumbo helps to hide the fact of physical invasion, that is, cover the tracks. In general, there is nothing impressive about this program. To work, it requires physical access to the computer.
Honestly, it is a very specialized tool for a specific application in the operations of special services. Even if WikiLeaks had put binary files, drivers and other program files in open access, hardly anyone would have found a practical use for it. On this occasion, in the user manual of July 6, 2015 there is a remark that the need to develop such a tool was formulated by the intelligence community (it includes representatives of the NSA, CIA, FBI and other organizations) and is enshrined in document 2015-OPS0001013. The goal is to suspend the operation of webcams and delete video recordings that may compromise the work of the PAG agents. Well, if necessary, qualified programmers made such a simple "tool" for the bosses.
The program runs on the victim's computer from a USB flash drive with SYSTEM privileges. The main executable file of the Dumbo 3.0 version is called GUI.exe , and it includes:
- scanner.sys driver for 32-bit Windows XP;
- executable file wscupd.exe to create a blue screen on computers under 32-bit Windows;
- executable file wermgr.exe to create a blue screen on computers under 64-bit Windows.
The tool works on 32-bit Windows XP, Windows Vista and newer versions of Windows. At the same time, 64-bit Windows XP and older versions of Windows are not supported.
The program interface is perfectly simple. The CIA agent inserts a USB flash drive, then launches cmd.exe , and from there launches GUI.exe , adding the
-n
option if necessary (do not automatically disable the network adapter and Bluetooth on the computer). The program is loaded, and then displays four options:
- System information
- Network
- Camera and microphone
- Exit Options
The first is clear - this is information about the system.
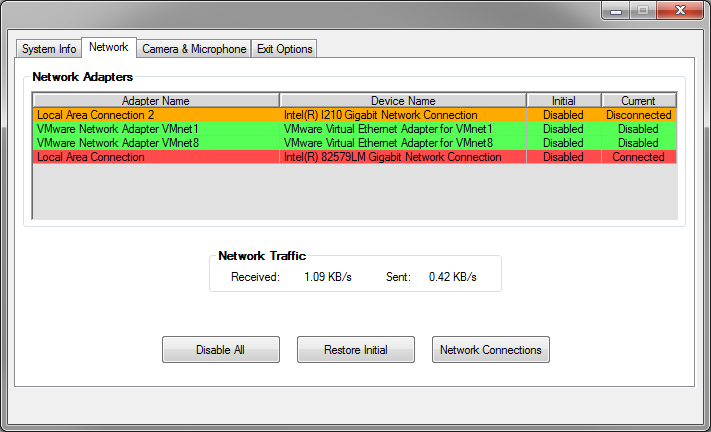
In the “Network” section, a list of network adapters is displayed, the initial status of the adapter (before Dumbo captures the processes in the system) and the current status, incoming and outgoing traffic. From here you can disable the adapters or return them to their original state.
The main tab "Camera and microphone" contains the main functionality of the program. From here, the agent gets access to management options for processes running on the computer and access to the file table with write permission (and their statuses).
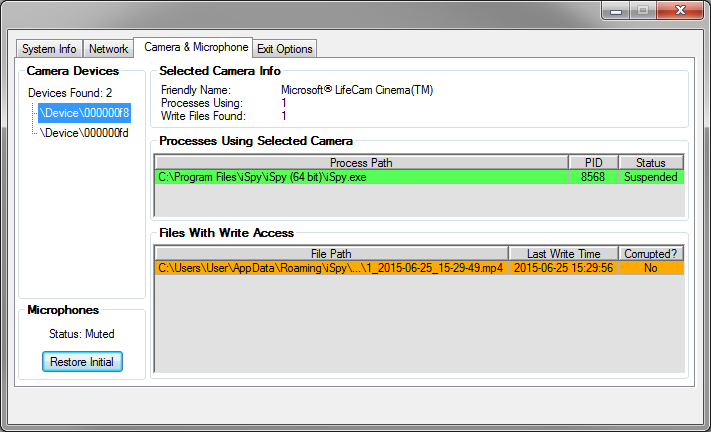
Accordingly, the agent can pause / resume or delete the process. Files can be accessed in two ways: either damage (fill with random data) or damage and delete (fill with random data, and then erase).
Exit options - either through a timer (after which the system returns to its normal state), or through a blue screen. It is assumed that the victim will return to the computer, see the blue screen and will not be surprised that the surveillance system, the webcam and the microphone have not recorded anything about what is happening in his absence.

There is one interesting point. A special item on Kaspersky Anti-Virus is registered in the Dumbo user documentation. It is noted that this particular antivirus prevents the installation of the driver necessary for the correct operation of Dumbo under Windows XP.
"Good job, Kaspersky."
WikiLeaks continues to declassify the CIA's hacking tools. The total number of documents has already exceeded 8700 pieces. Unfortunately, Julian Assange still does not upload binary files of exploits and hacker programs themselves, but is limited only to documentation.
All Articles