Nobody wants to tell Apple about iPhone vulnerabilities

Screenshot of the survey, which was conducted by Jonathan Zdzierski, a former jailbreaker, and now a security specialist. He recently went to work at Apple and deleted his Twitter account.
In August 2016, Apple solemnly opened a reward program for the vulnerabilities found . Such programs have long been active in almost all large IT companies. Long resisted the payment of rewards to Microsoft, but she also surrendered in 2013, running Microsoft Bounty Programs . Perhaps, Apple remained the last among the producers of mass products, who do not pay hackers, so the news about the beginning of the payment of remuneration was favorably received by the community.
The only problem is that over the past year we have not heard of any cases for someone to get money from Apple. Perhaps they are simply forbidden to talk about it. Or maybe they prefer to sell exploits on the black market at a much higher price.
Why did Apple take so long and not introduce a vulnerability payout program? His version was expressed by a former employee of the company who worked in the security department, in the Motherboard commentary : “Apple does not like to release things - including the payment program for vulnerabilities - until it brings them to perfection. They are perfectionists. ” The employee wished to keep his name in obscurity, because he was violating a non-disclosure agreement (NDA).
In fact, if you strive to bring the project to the ideal - there is a chance to never release it.
But after the scandal with the FBI, it became clear that it was impossible to continue. Recall that then the FBI for a long time demanded that Apple hack the encryption system on the terrorist’s phone, but Apple refused to do so in order to protect the rest of its users from interception. In the end, the FBI agents coped with the task without the help of Apple, paying for the services of a third-party hacking company, which had a 0day-exploit for iOS. Intelligence agencies paid a very large amount for this exploit. Presumably more than $ 1.3 million The newspaper The New York Times then wrote that hackers did not report to Apple information about the bug in the system, because they had no incentive to do so. I mean, there was no financial incentive — Apple did not pay for reporting vulnerabilities.
The Apple Company made the right conclusions and in August launched a program of financial incentives. True, she acted here in her own way, not like everyone else. Although the announcement of the program was public, but otherwise Apple continued to operate secretly. The terms of the program are not publicly available, and participation in it is possible only by invitation.
We know about the amount of rewards from the presentation of the head of Apple’s security department, Ivan Krstic. As was shown on one of the slides, the maximum reward is $ 200 thousand paid for hacking into components of the Secure Boot firmware. The minimum is $ 25 thousand for exiting the process from the sandbox and access to personal user data.
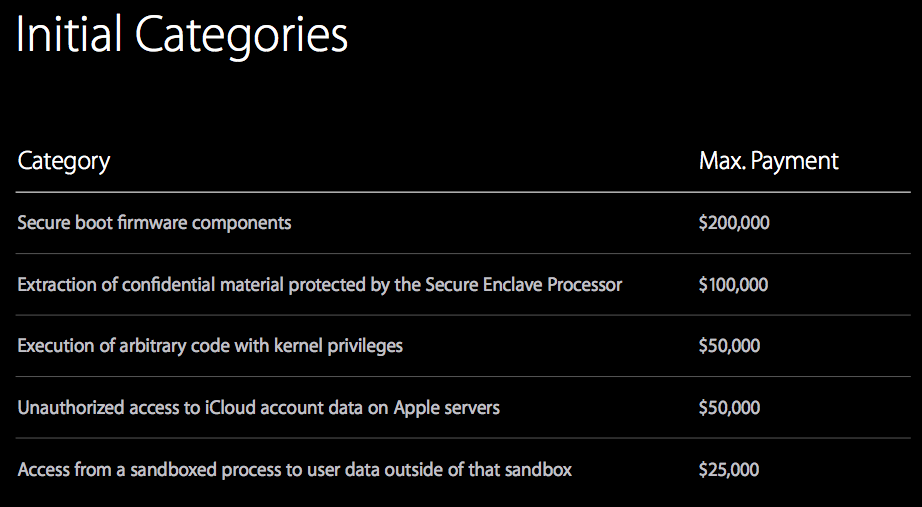
Slide from the presentation of Ivan Krstic
There is an opinion that even $ 200 thousand is not a high enough amount for 0day to iOS. These exploits are quite rare, so their cost is much higher on the black market. For example, shortly after the presentation of Krstic, Zerodium increased its pricing for the purchase of exploits for iOS. So, for the most valuable thing - a remote jailbreak iOS 10, they already pay $ 1.5 million instead of the previous $ 500 thousand.
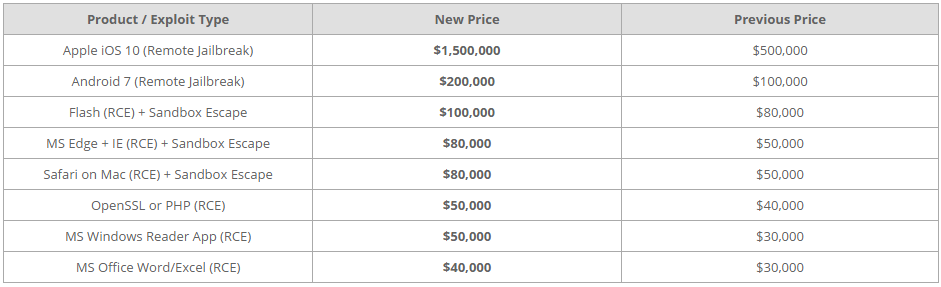
New Zerodium Pricing
Well, where will you sell the jailbreak - to Apple for $ 200 thousand or to Zerodium for $ 1.5 million? This is probably a rhetorical question. Few confuse that Zerodium cooperates with special services and security agencies of different countries, and its exploits can be used for state espionage and other not very beautiful things.
By the way, it’s far from the fact that if Apple raises the prices of exploits to the gray market level, this will solve the problem. Here the economy works as follows. If Apple raises prices, then 0day for iOS will become even more rare - and prices in the gray market will increase even more. That is, we will return to where we started. Although de facto unclosed bugs will really become smaller. In general, this is the main goal of payment programs for vulnerabilities.
Currently, 0day-vulnerability buyers can be divided into three groups:
- Apple itself.
- Crime: the mafia, criminal groups and so on.
- Big players, including state security services: NSA, Mossad, GRU, ISIL (banned in Russia), and so on.
Apple has a lot of money in banks. Through secretive subsidiaries, it offshore over $ 200 billion . This money is quite possible to use. Apple can easily increase the reward for exploits so much so that crime (mafia, criminal groups) will not be able to deal with it. But she will never be able to compete with the secret services, whose resources are practically unlimited and are not limited to money. These guys will always have their exclusive 0day at their disposal, no matter what you do or what reward you are given for disclosing vulnerabilities.
All Articles