WannaCry stopped Honda conveyors

WannaCry did not finish his dirty work. June 21, 2017 Honda Motor Co. reported that she had to stop the conveyor at the Sayama plant (Japan) for one day after WannaCry cryptographer was discovered on computers, whose global epidemic had passed and seemed to end last month.
The plant in northwest Tokyo did not work on Monday, June 19th. On ordinary days, the Accord, Odyssey Minivan sedan and Step Wagon compact multi-purpose cars are produced here, with a daily production capacity of about 1,000 cars.
Honda representatives said: on Sunday, it was discovered that the virus had hit corporate networks in Japan, North America, Europe, China and other regions, although the company took action to protect computers in mid-May, when the global WannaCry epidemic occurred.
A company representative did not explain how the WannaCry version got into the network 37 days after the domain was registered that launched a “stop-crane” to spread the malware. Perhaps, the system administrators of the company blocked traffic to this domain. Another possibility is that a new version of a cryptographer has been discovered on the network. However, they all use the same vulnerability in Windows, and the IT department should have closed this vulnerability as early as May.
Production at other Honda plants did not suffer, and Sayama resumed on Tuesday.
It should be noted that in May, in the wake of the epidemic, other automakers, including Renault SA and Nissan Motor Co., suffered from a cryptographer. This alliance stopped production at its plants in Japan, the UK, France, Romania and India. Production in Togliatti continued normally.
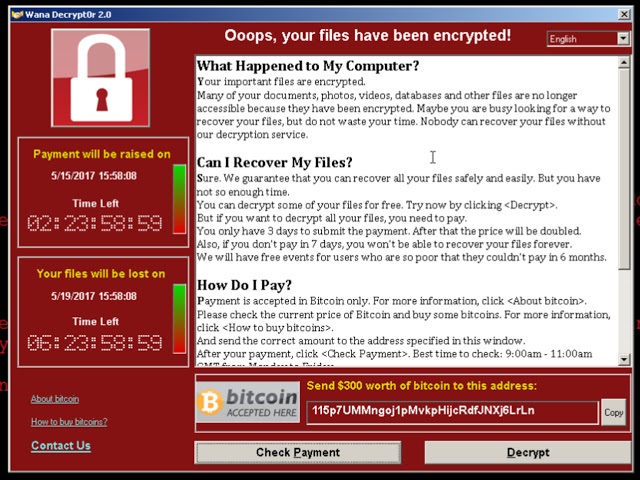
WannaCry: when is the second wave?
When to expect a second wave of WannaCry, which may be stronger than the first? No one knows the answer to this question, but experts unequivocally predict that new versions of the cryptographer will definitely appear. Any of these versions may become widespread, and then a wave of infections will become an epidemic.
The first version of WannCry in the middle of May infected approximately 727,000 computers in about 90 countries, but since then the speed of the forks of the worm has slowed considerably. The absolute majority of infections occurred on computers with the Windows 7 operating system. The fact is that the Windows 10 system has already closed the vulnerability that the NSA exploit EternalBlue uses, leaked online and applied by the authors WannaCry. And Windows XP SP3 computers simply cannot execute the malicious code, falling into the blue “screen of death” .
It was possible to stop the spread of infection completely by chance thanks to one guy . This hero is a 22-year-old hacker and blogger from the UK MalwareTech, whose name has not yet become public. As he said, that day he had a day off, he woke up around 10:00 and logged into the national cyber threat tracking system to watch the spread of bank malware Emotet, the most significant event of recent days. I did not notice anything unusual and went to breakfast. When I returned home around 2:30 pm, I found a bunch of reports about the infection of various hospitals and medical systems with cryptographer. Such infections occurred before, but here, as if the scale was larger than before. With the help of his friend, a hacker under the nickname Kafeine, the guy quickly took out a sample of the malware, launched it in a virtual machine and saw that it was sending requests to an unregistered domain.
Cisco Umbrella statistics showed that requests to this domain began on Friday at 8:00 am and grew like an avalanche. The blogger registered the domain on himself for 8 pounds ($ 10.69). This is standard practice, he says. Botnets often generate domain names for command servers (C2C) each according to their own algorithm. The algorithm is known to intruders, so they can register this domain in advance. Sometimes, researchers and antivirus companies manage to get ahead of them, and then they have the opportunity from the inside to study the work of the botnet command center, collect data on the geographical distribution of bots, and reverse engineer the software. So registration of these domains is a normal thing. MalwareTech said that over the past year has registered several thousand domains.
Since all infected people knocked on this domain, after gaining control over it, the researcher was able to compile a list of IP addresses and an infection map using log files. By evening, it turned out that it was the domain registration that stopped the further distribution of the cryptographer. Most likely, in this way, the authors of the malware implemented protection against the analysis of their program (protection against the virtual environment).
Shortly after the first one, the second and third variants of WannaCry were discovered, including those operating without a kind of “stop-crane” in the form of requests to a nonexistent domain. Surely since then there were other versions. Perhaps some of these versions reached the Honda factories. It is difficult to find excuses for Honda IT professionals who have not yet installed patches from Microsoft.
All Articles